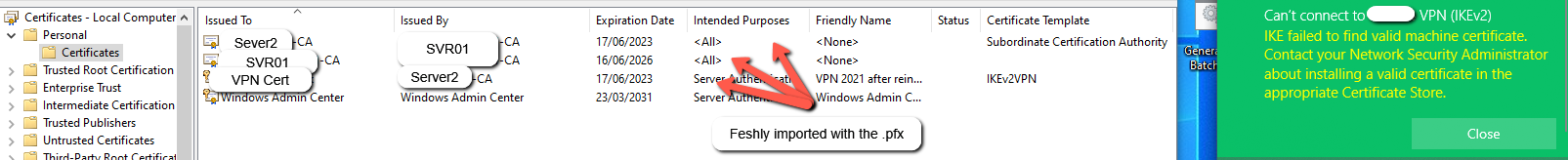
Hello @Adam Lacey ,
Has your "root" certificate expired? Root certificates often have a validity period of 20 years and it is often recommended to introduce an additional new root certificate after about half the validity period has elapsed (to smooth the hand-over) - so it would be an unpleasant surprise to suddenly discover that your sole root certificate has expired.
If the root certificate has not expired, then there may be no need to distribute anything to the client PCs (this will depend on the authentication mechanism being used). If the authentication mechanism does not require a client certificate (e.g. EAP-MSCHAPv2) then the clients need no update - they will still trust the root certificate and all other certificate information is available in the IKEv2 protocol exchanges.
If client certificates are needed for the authentication mechanism and these certificates have expired, then the clients will need to re-enroll.
Gary

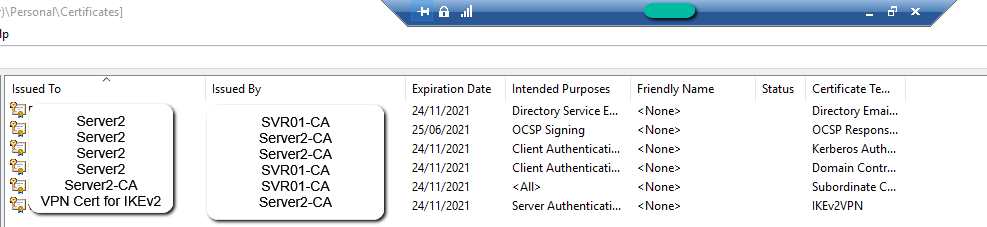
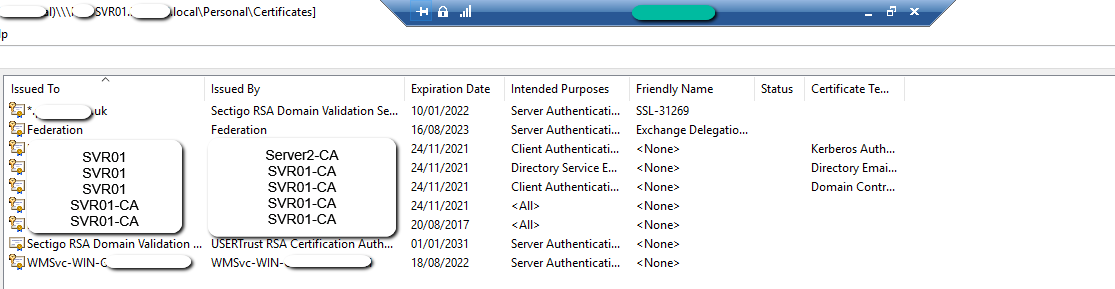
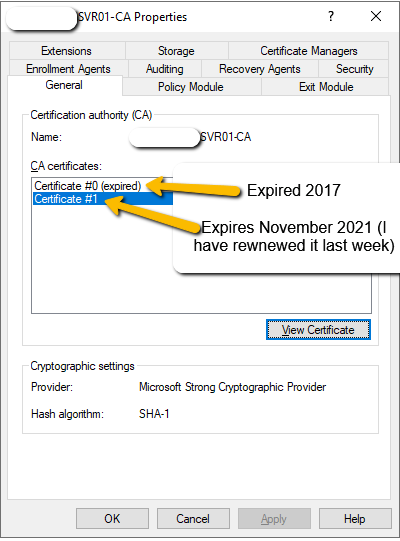 - SVR01 Certificates (I'm sure I deleted the 2017 expired one before):
- SVR01 Certificates (I'm sure I deleted the 2017 expired one before):
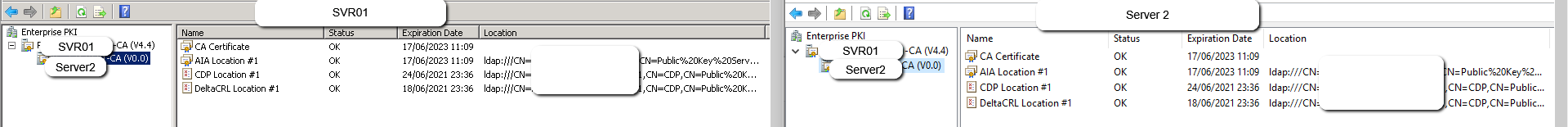
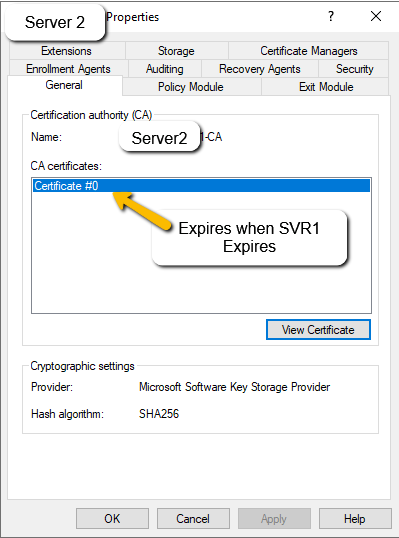 - Server2 Certificates:
- Server2 Certificates: