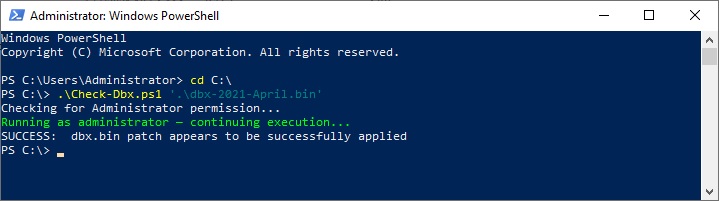
Hi @9manloon ,
I just want to say that I have found Nessus not to always be 100% reliable, the same could also be with any other scanning tool.
Even if the system is fully mitigated from vulnerabilities, the scanning software may sometimes still show that there's a vulnerability.
If you have followed the Microsoft guidance, then I would say it is enough.
----------
(If the reply was helpful please don't forget to upvote and/or accept as answer, thank you)
Best regards,
Leon