
Hello @Bundoo ,
Thank you for posting here.
Hope the information provided by Crypt32 is helpful to you.
Here are my suggestions for your questions:
Q1: How will I know if this PKI role is Forest wide and all the Forest DCs are sharing this same PKI role ?
A1: Since Public Key Services container is stored in configuration naming context, any it’s content is replicated between all domain controllers in the current forest (not only current domain) and are available to any client in the forest. This means that there is no way to limit PKI containers only to specific domain or domains.
For example:
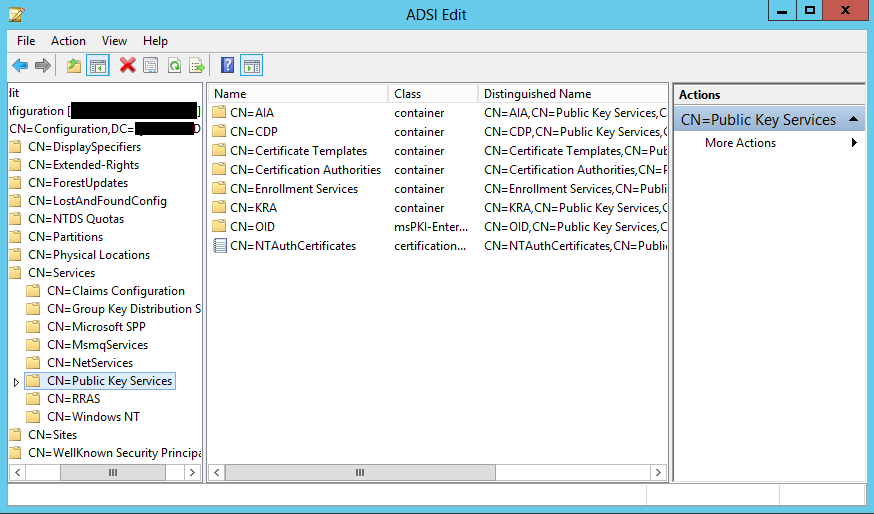
Q2: Can I just install AD Certificate services on an existing DC and assume that it has a role of Enterprise PKI now ?
A2: You should migrate AD CS to another member server instead of one Domain Controller.
For more information above AD CS migration, we can refer to link below.
Step-By-Step: Migrating The Active Directory Certificate Service From Windows Server 2008 R2 to 2019
https://techcommunity.microsoft.com/t5/itops-talk-blog/step-by-step-migrating-the-active-directory-certificate-service/bc-p/700730#M270%3FWT.mc_id=ITOPSTALK-blog-abartolo
AD CS Migration: Migrating the Certification Authority
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ee126140(v=ws.10)#BKMK_GrantPermsAIA
Performing the Upgrade or Migration
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc742388(v=ws.10)
Tip: Usually, we want a DC to be just a DC, there is nothing else, because this reduces possible resource conflicts and exploit vulnerabilities and minimizes patching of other applications that might cause downtime.
Ideally, a DC should be easy to replace, just by standing up another DC.
When we put other software and roles on one DC, maybe the DC is harder to replace it.
For example,
If we have a DC with AD CS(it is also a CA server), if there is some issues with this DC and we want to demote this DC, we need to remove AD CS first and then demote this DC.
Considerations for migrating a CA to a new machine:
1.When migrating a CA, the computer name of the target computer may be different from the computer name of the source computer, but the CA name must remain unchanged.
2.By default, Active Directory Certificate Services (AD CS) is configured with certificate revocation list (CRL) distribution point extensions, including the CA machine host name in the path. This means that any certificate issued by the CA prior to migration may contain a certificate verification path that contains the old host name. These paths may no longer be valid after migration. To avoid revocation checking errors, the new CA must be configured to publish the CRL to the old (pre-migration) path as well as the new path.
3.During the installation process, we must choose to use the CA's existing certificate and private key instead of creating a new CA certificate and key.
4.Each of the above small steps contains a lot of operations.
It is recommended that you set up a similar CA environment in the test environment, and perform migration operations in the test environment, and then record all these steps in a document, and write down the key points and precautions.
If there are no problems, follow the similar the steps in the production environment, so that even if you encounter any problems in the production environment, you should be able to troubleshoot or solve them well.
Hope the information above is helpful.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
