Hi @Neeraj Kumar
Thank you for posting in Q & A.
You would still be able to log on by using the Local Administrator credentials?
Cause
There are multiple reasons why NLA might block the RDP access to a VM:
The VM cannot communicate with the domain controller (DC). This problem could prevent an RDP session from accessing a VM by using domain credentials. However, you would still be able to log on by using the Local Administrator credentials. This problem may occur in the following situations:
The Active Directory Security Channel between this VM and the DC is broken.
The VM has an old copy of the account password and the DC has a newer copy.
The DC that this VM is connecting to is unhealthy.
The encryption level of the VM is higher than the one that’s used by the client computer.
The TLS 1.0, 1.1, or 1.2 (server) protocols are disabled on the VM.The VM was set up to disable logging on by using domain credentials, and the Local Security Authority (LSA) is set up incorrectly.
The VM was set up to accept only Federal Information Processing Standard (FIPS)-compliant algorithm connections. This is usually done by using Active Directory policy. This is a rare configuration, but FIPS can be enforced for Remote Desktop connections only.
Workaround
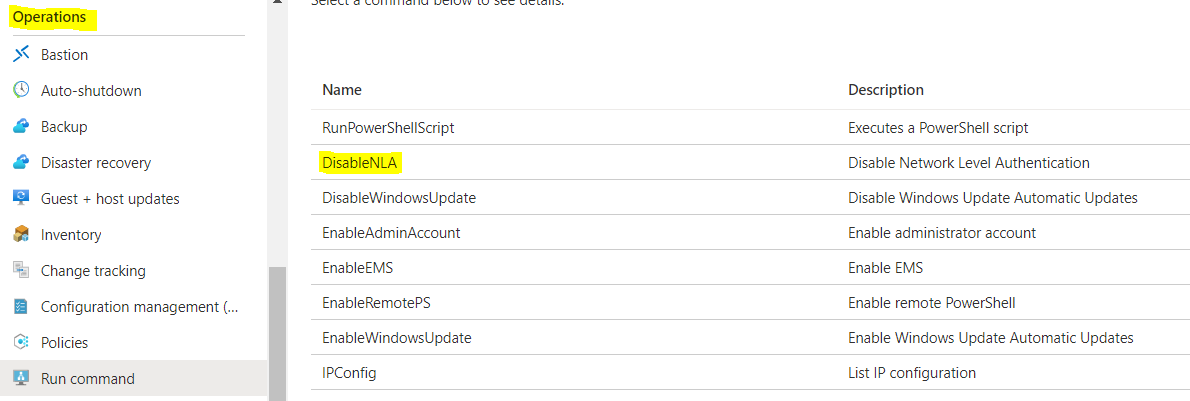
In Azure portal - VM blade - go to operations - Run command - disable NLA
after disable NLA try to login & check, refer below screenshot.
refer- https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/cannot-connect-rdp-azure-vm
If the Answer is helpful, please click Accept Answer and up-vote, this can be beneficial to other community members.
