@alfredo-msft-identiy
Here's the flow. First we direct the user to authorize:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize?client_id=****&redirect_uri=https%3A%2F%2F****%2Fauth%2Fcallback&scope=Group.ReadWrite.All+Chat.Read+Files.Read.All+Sites.Read.All+User.ReadWrite.All+offline_access&response_mode=form_post&response_type=code
We get a callback with:
'code' => '****10f24',
'state' => '***'
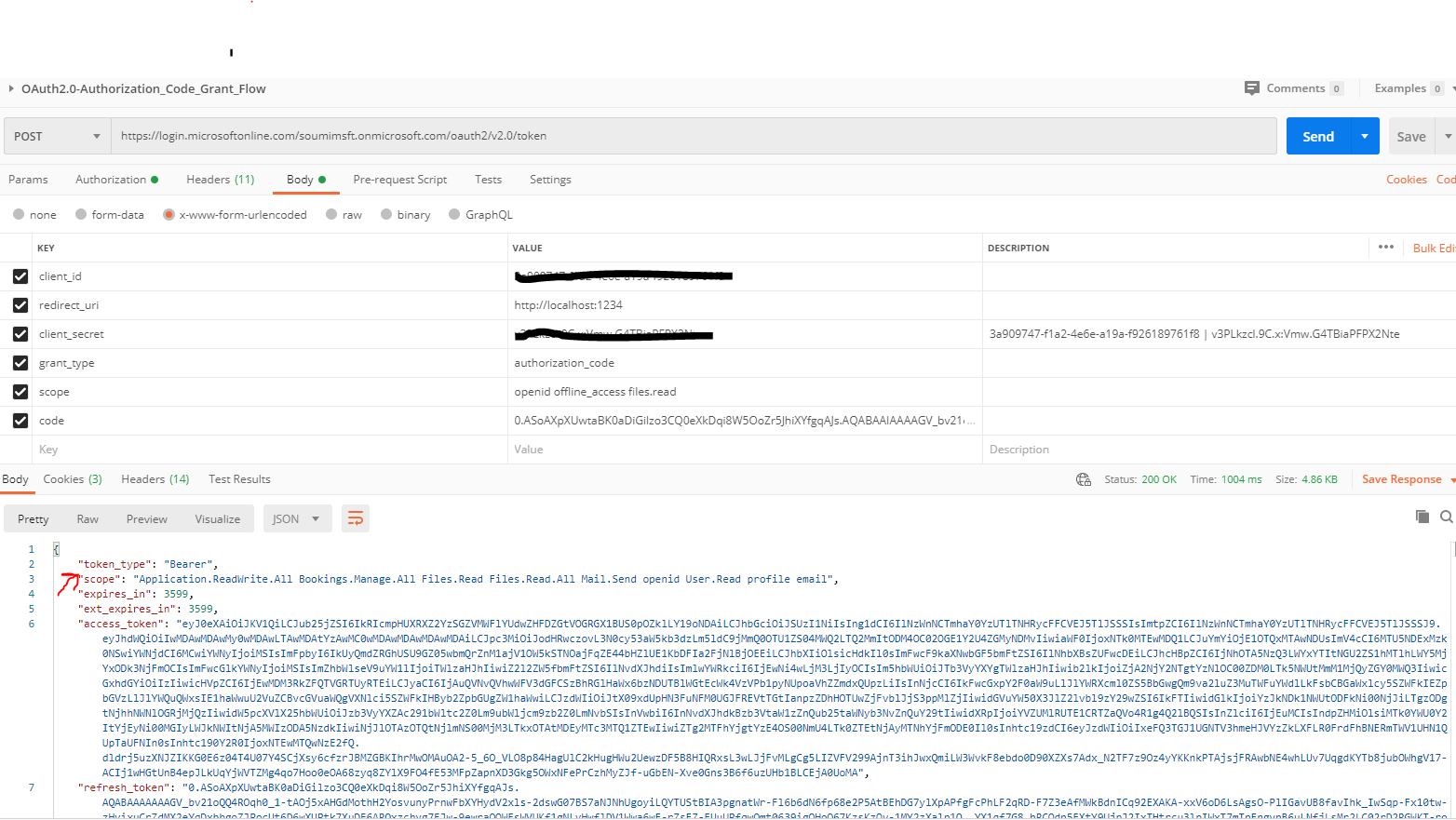
We then hit the token endpoint to exchange for an access token:
POST https://login.microsoftonline.com/common/oauth2/v2.0/token
Request:
'client_secret' => '****',
'code' => '****10f24',
'grant_type' => 'authorization_code',
'redirect_uri' => 'https://****/auth/callback'
And this is the response that we get:
'token_type' => 'Bearer',
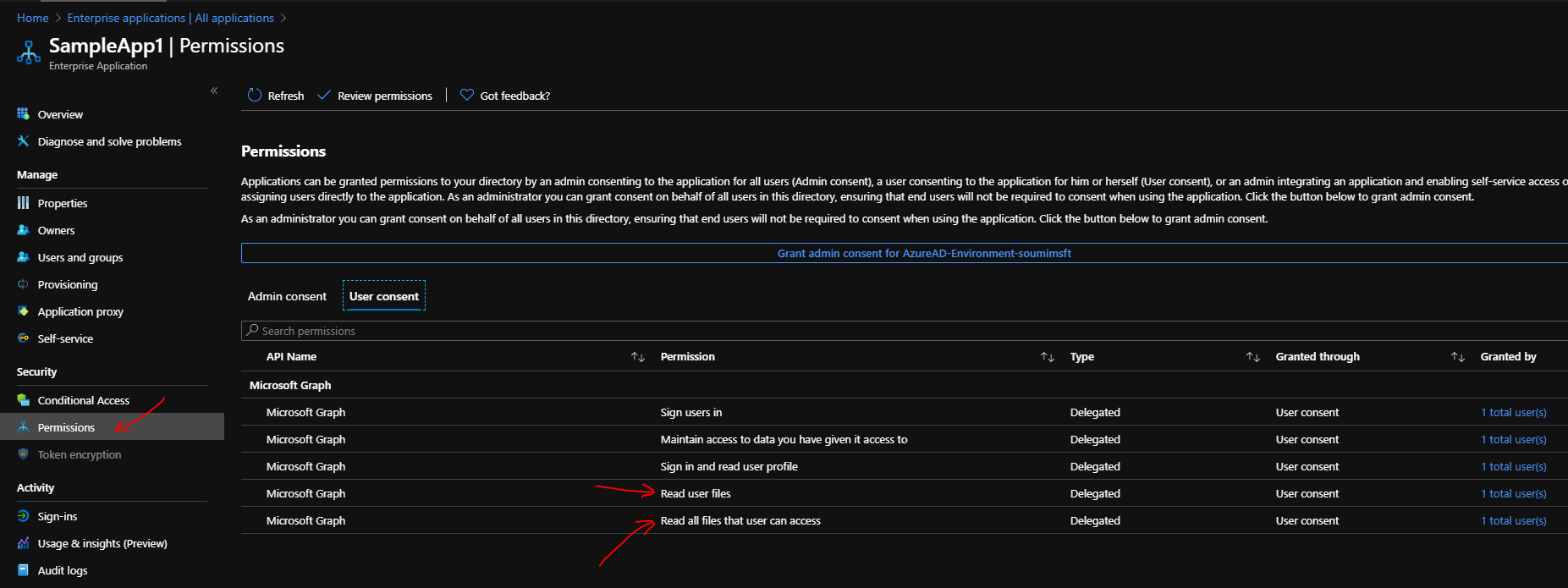
'scope' => 'Group.ReadWrite.All Files.Read.All User.Read',
'expires_in' => 3600,
'ext_expires_in' => 3600
Thanks!