Hi,
I have Azure AD and AD DS deployed.
Multiple services on multiple VMs use a single account to access services. The problem is, if a single service has a bad password (for whatever reason) it causes a lockout of the admin account and blocks all other VMs. I need to be able to track the faulty VM.
My issue is, that the Logs do not show the "Source Workstation" being the faulty VM, but the AD DS DC that's in front of it:
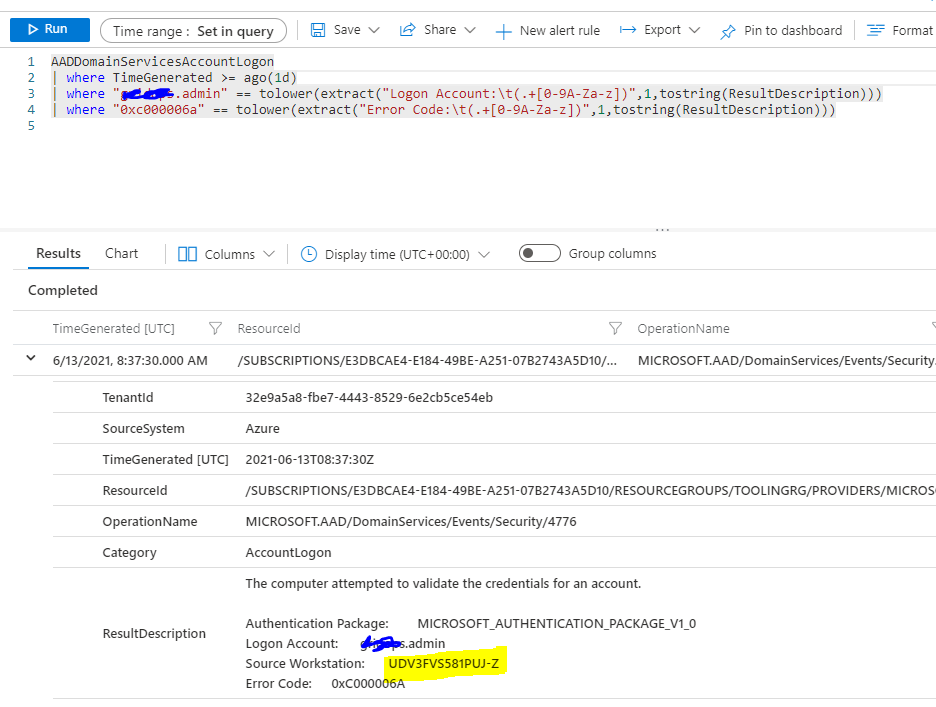
Is that a bug, or do I have something not set up correctly? How to track the source of bad-password requests?
What i am doing right now, is switching the VMs off and checking if the requests stop - but this is no long-term solution.


