Hello @Pratiksha Shetty ,
Thank you for posting here.
Here are the answers for your reference.
1) Can I run this command now even after creating the KDS root key once "Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10))"
A: If you run this command now even after creating the KDS root key once "Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10))", this will create multiple new KDS root keys.
For example:
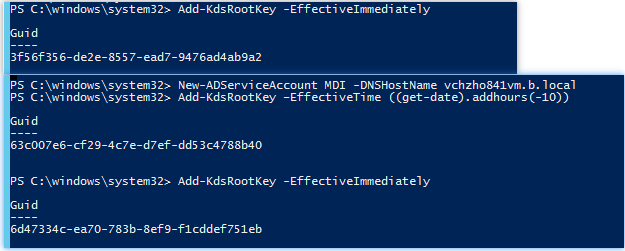
And you can view all the keys by the cmdlet: Get-KDSRootKey.
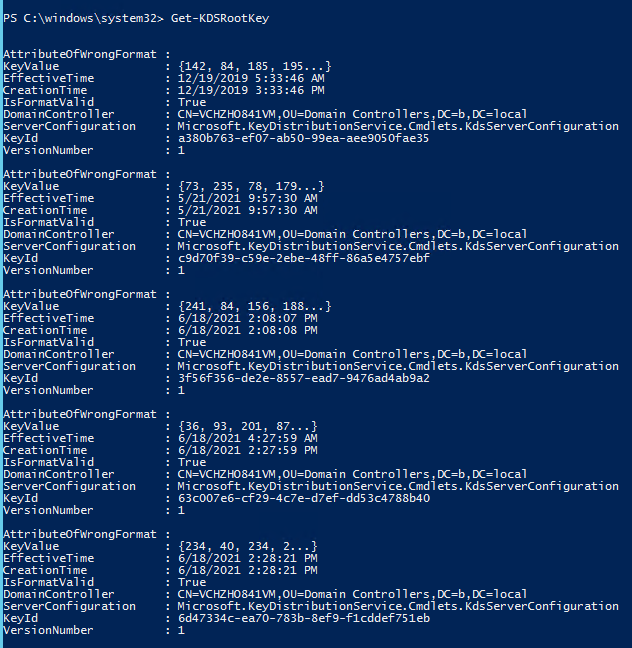
We recommend to create the KDS Root Key only once per domain.
Here is a similar case for your reference.
What happens if you Generate a new root key for the Group Key Distribution Service if one exissts?
https://social.technet.microsoft.com/Forums/en-US/c80a270a-9354-4a2a-812e-e6b6e7a2e159/what-happens-if-you-generate-a-new-root-key-for-the-group-key-distribution-service-if-one-exissts?forum=winserver8gen
2) If not then will it take 10 hours even if I have one DC?
A: It seems it will take 10 hours even if you have one DC if you run command "Add-KdsRootKey -EffectiveImmediately".
But if you it will take effect immediately even if you have one DC if you run command "Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10))".
For example:
In another new AD lab, on my newly AD Domain Controller (only one DC).
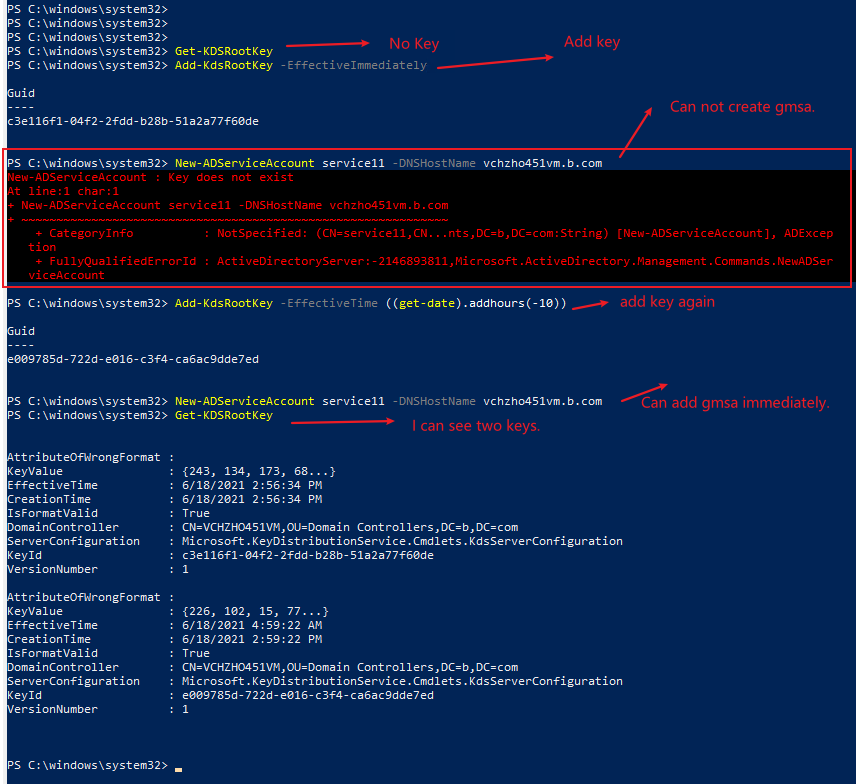
3) Is there any workaround to skip the waiting hours and run the new-adserviceaccount command ?
A: Based on my knowledge, there is no any workaround to skip the waiting hours.
If you must want to create service account immediately, you can run command "Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10))" and create service account immediately, then delete one of the two KDS root Key.
Refer to:
Delete KDS root Key:
http://www.windows-noob.com/forums/index.php?/topic/7625-delete-kds-root-key/
Tip: We do not recomment to create multiple the KDS Root Keys in one domain.
If you create more than one KDS root Keys and delete the redundant ones, we are not sure whether it will have any impact in the production environment.
Hope the information above is also helpful.
Should you have any question or concern, please feel free to let us know.
Please note: Information posted in the given link is hosted by a third party. Microsoft does not guarantee the accuracy and effectiveness of information.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.