Hi @NicholaiX-5929 · Thank you for reaching out.
For this purpose, you can configure below setting:
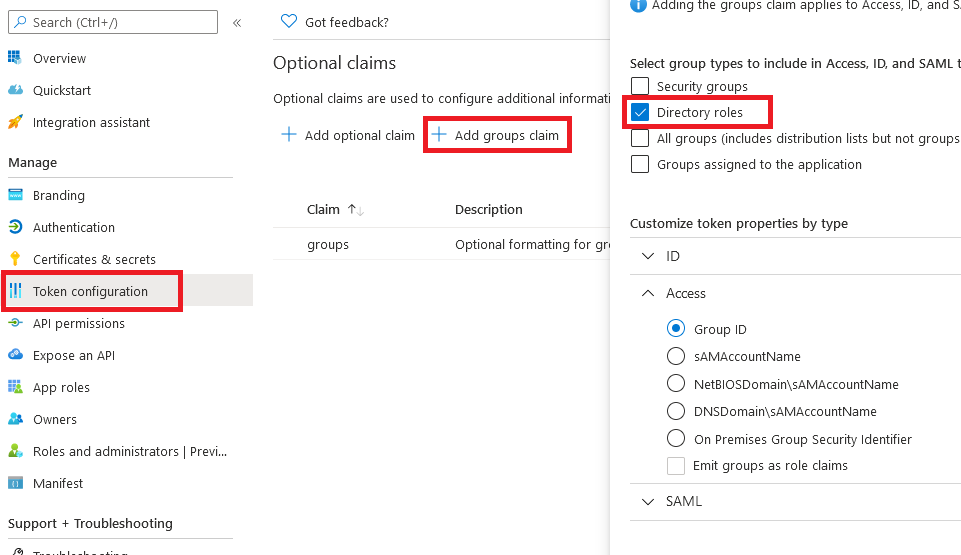
Directory roles: If the user is assigned directory roles, they are emitted as a 'wids' claim (groups claim won't be emitted). These GUIDs are constant and you can use them to maintain a mapping table.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
