@jagadish karem Thanks for reaching out.
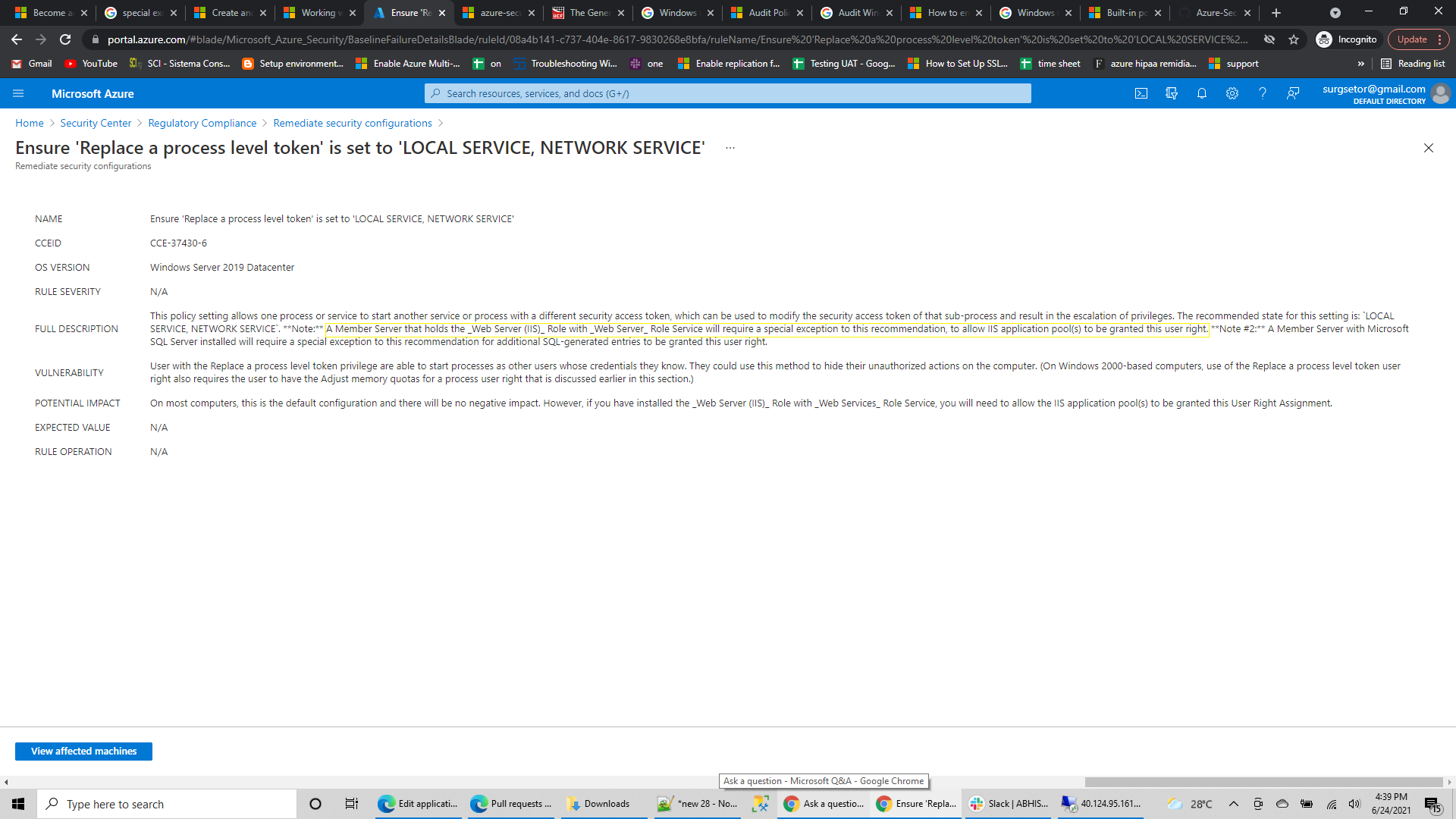
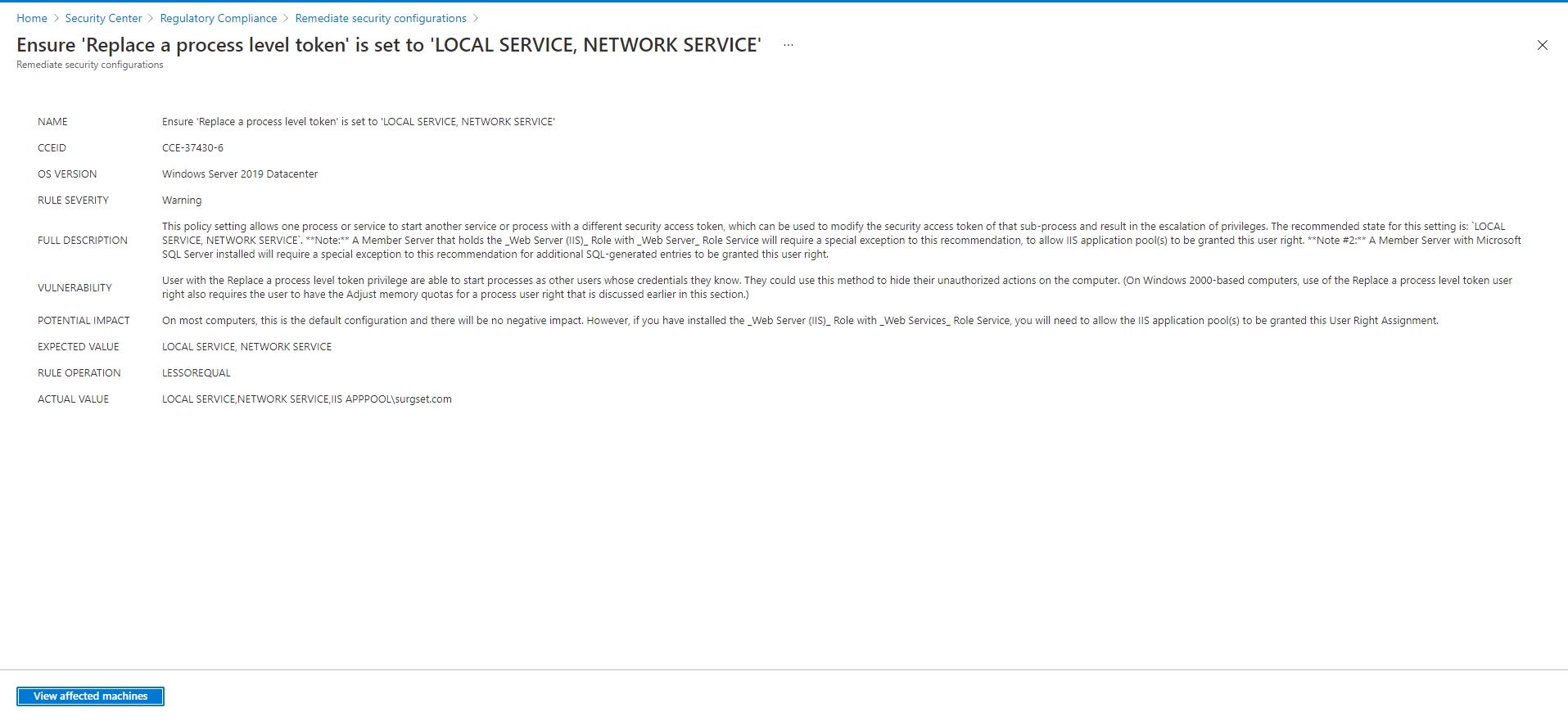
On most computers, restricting the Replace a process level token user right to the Local Service and the Network Service built-in accounts is the default configuration, and there is no negative impact.
However, if you have installed optional components such as ASP.NET or IIS, you may need to assign the Replace a process level token user right to additional accounts.
IIS requires that the Service, Network Service, and IWAM_<ComputerName> accounts be explicitly granted this user right.
Under security center if you do not want to see that recommendation, then you can suppress this alert by using a suppression rule.
You can use this link to create suppression rule for this server recommendation : https://learn.microsoft.com/en-us/azure/security-center/alerts-suppression-rules
-----------------------------------------------------------------------------------------------------------------
If the suggested response helped you resolve your issue, please do not forget to accept the response as Answer and "Up-Vote" for the answer that helped you for benefit of the community.