Hello everyone
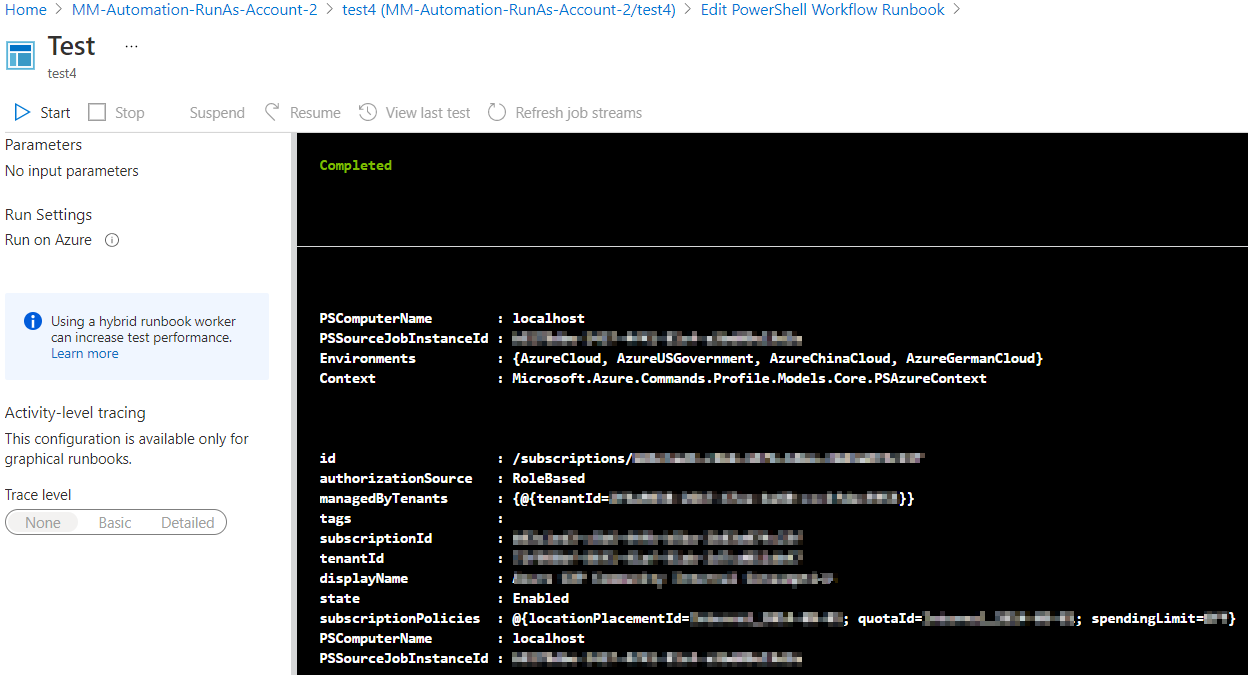
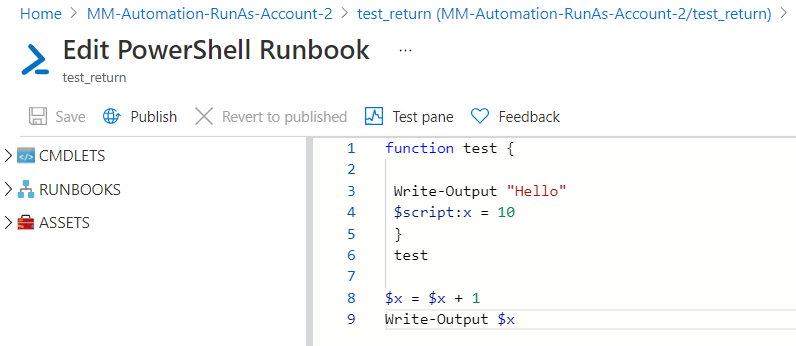
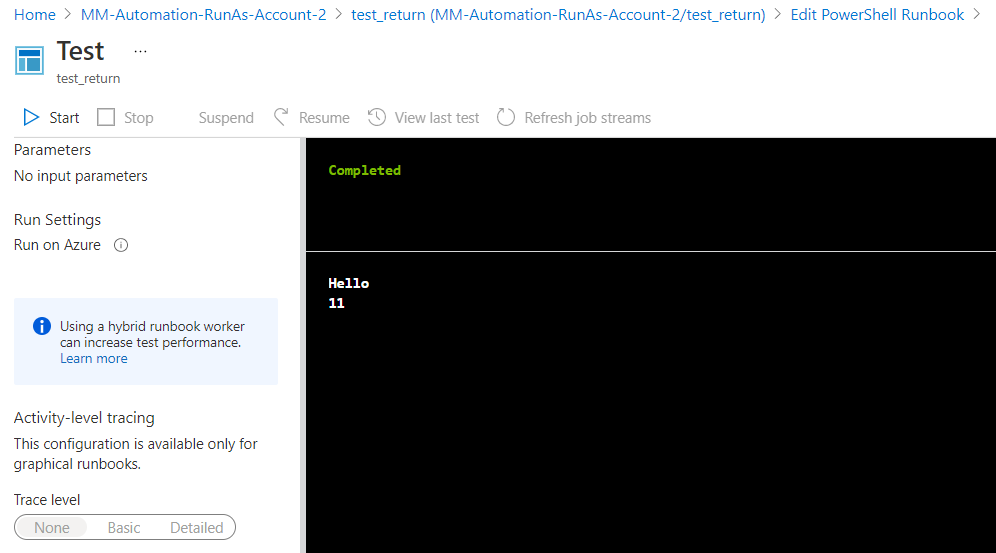
I created a powershell runbook below. can someone tell me how to transfer the powershell runbook to powershell workflow runbook.
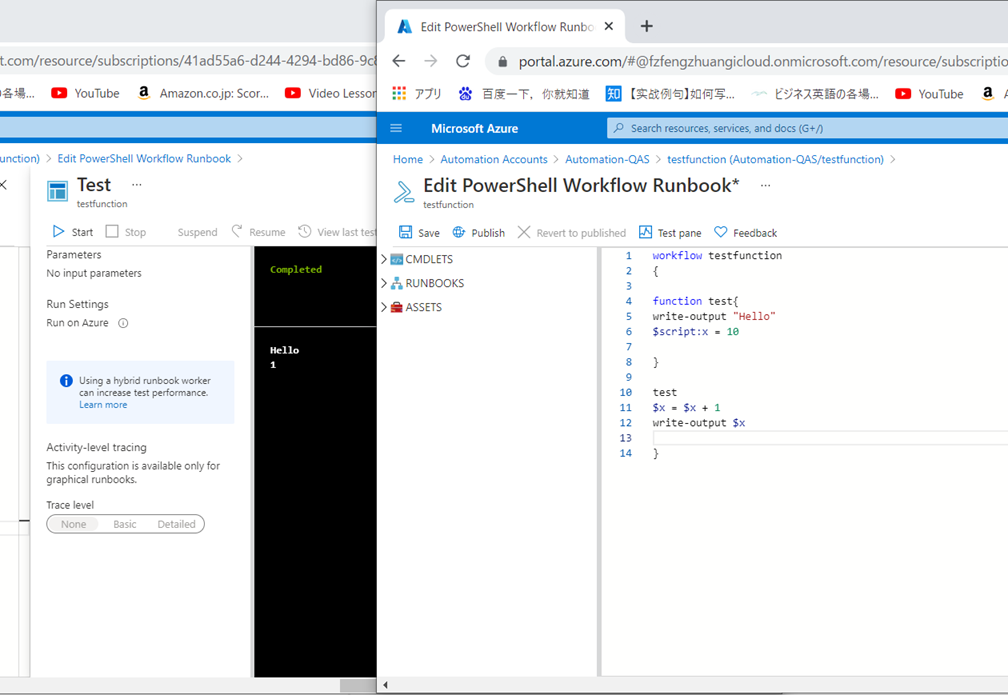
The error was happened when I copied the code to powershell workflow runbook and run it.
error: Runbook definition is invalid,Could not find type Microsoft.Azure.Commands.ResourceManager.Common.RMProfileClient
Could tell me why it cannot run in powershell workflow runbook
(it is can run in powershell runbook)
param(
[ Parameter (Mandatory= $true)]
[string] $ResourceGroupName,
[ Parameter (Mandatory= $true)]
[string] $VmName)
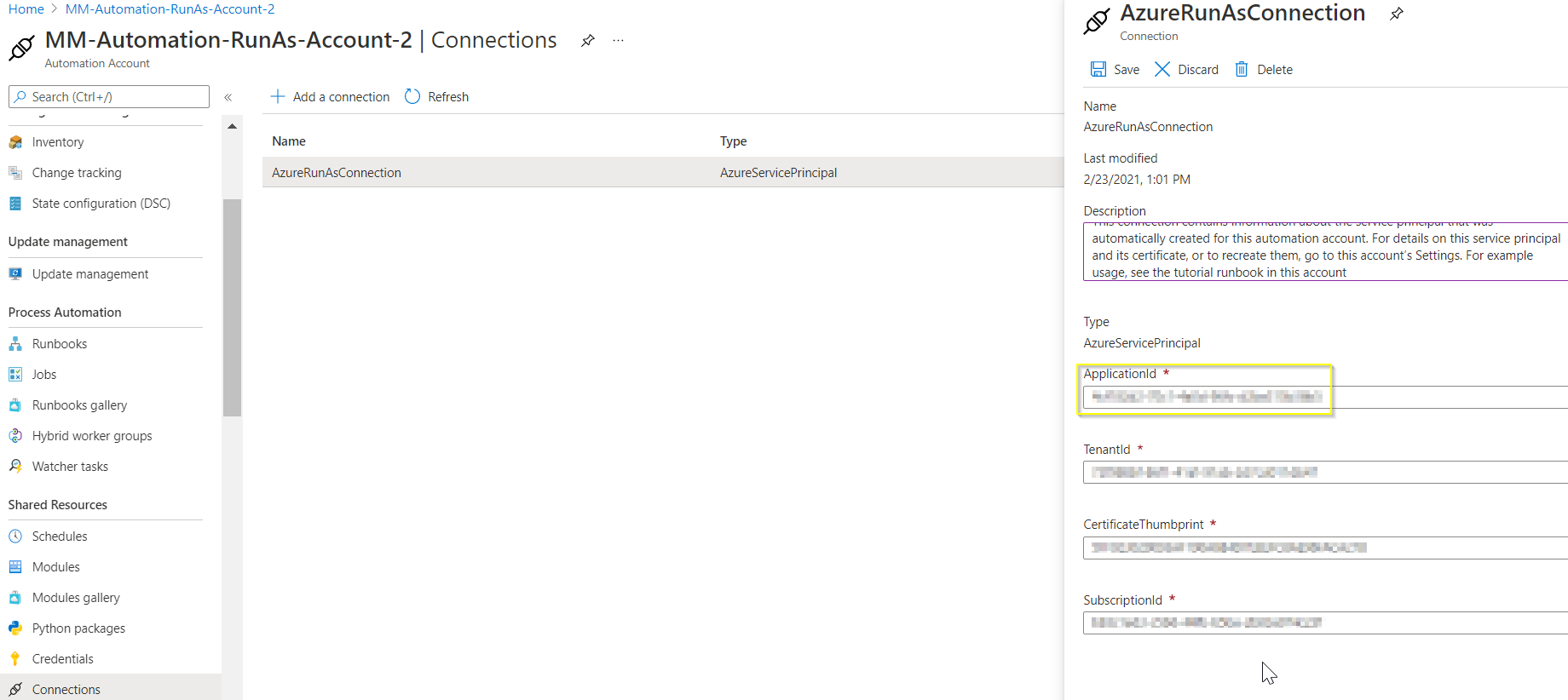
$ConnectionName = "AzureRunAsConnection"
$Conn = Get-AutomationConnection -Name $ConnectionName
Connect-AzureRmAccount -ServicePrincipal -Tenant $Conn.TenantID -ApplicationId $Conn.ApplicationID -CertificateThumbprint $Conn.CertificateThumbprint
$azProfile = [Microsoft.Azure.Commands.Common.Authentication.Abstractions.AzureRmProfileProvider]::Instance.Profile
$profileClient = New-Object -TypeName Microsoft.Azure.Commands.ResourceManager.Common.RMProfileClient -ArgumentList ($azProfile)
$token = $profileClient.AcquireAccessToken($azContext.Subscription.TenantId)
$authHeader = @{
'Content-Type'='application/json'
'Authorization'='Bearer ' + $token.AccessToken
}
$body = @{
xxxxxxxxxxx
}
$restUri = 'https://management.azure.com/subscriptions/{subscriptionId}?api-version=2020-01-01'
$response = Invoke-webrequest -Uri $restUri -Methodpost -Headers $authHeader -Body $($body | convertto-Json) -UseBasicParsing
Best wishes!