@Azure Apprentice Thanks for posting in our Q&A.
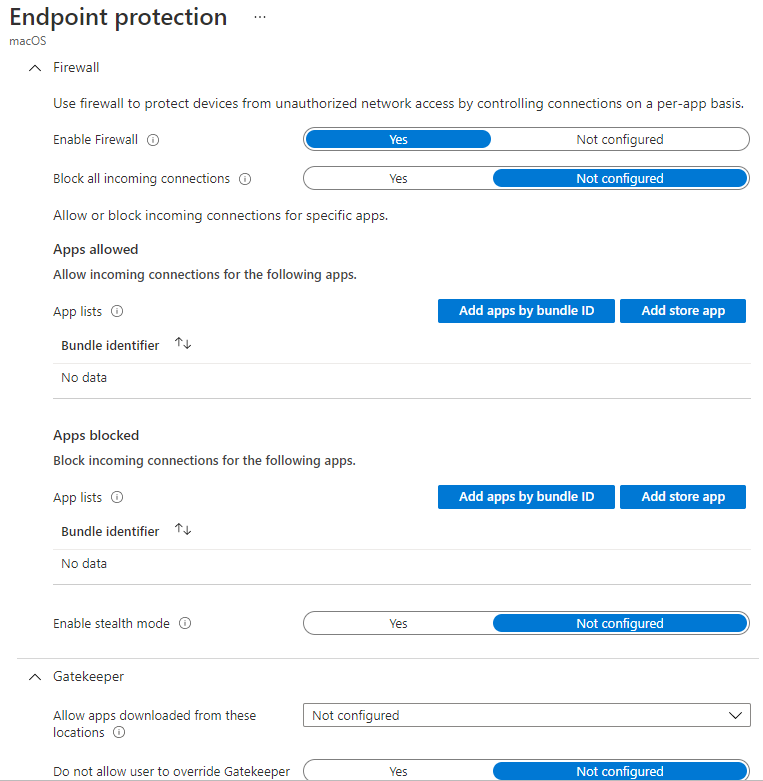
For this issue, there is no built-in settings that can be configurated to add an exception to the firewall based on port, folder, Application name etc.
Based on my research, whether intune has this feature is based on whether Apple provides this MDM feature. I find that the Apple Developer MDM documentation doesn't provide this feature that except to the firewall based on port and folder. We can refer to the following link:
https://developer.apple.com/documentation/devicemanagement/firewall
Note: Non-Microsoft link, just for the reference.
For Airplay, did you mean that the enrolled MacOS device could use Airplay normally when we didn't deploy the firewall restriction profile? If there is anything misunderstanding, feel free to let us know.
If the response is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.