Hi @sikumars-msft,
Thank you for your respone.
The web app is hosted on docker containers, outside the connector local network. The connector can establish communication with the web app only via the public IP.
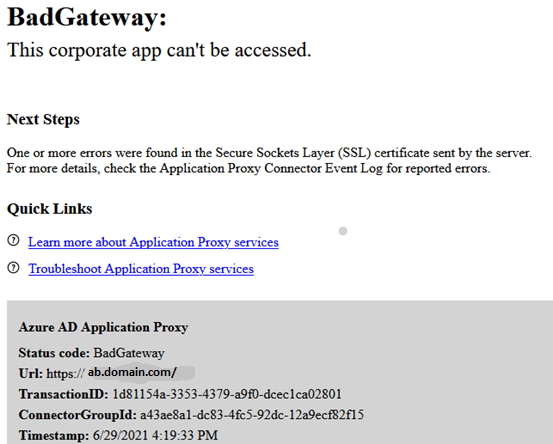
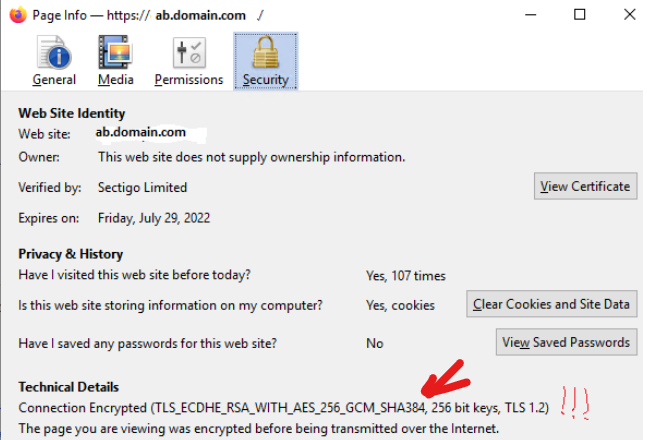
Access to the web app will be allowed only from connector's IP. At the moment I can access the domain ab.domain.com directly with no issues. Isn't this scenario supported ?
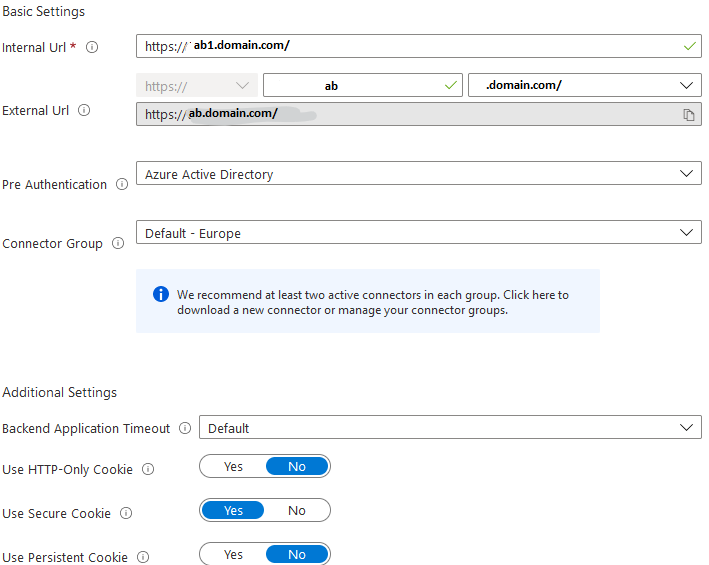
If I access the Internal URL ab1.domain.com from the connector machine, I get a certificate error as it doesn't match the domain ab1.domain.com. "Accept risk and continue" in browser and I can access the application.
Screenshot from connector machine:
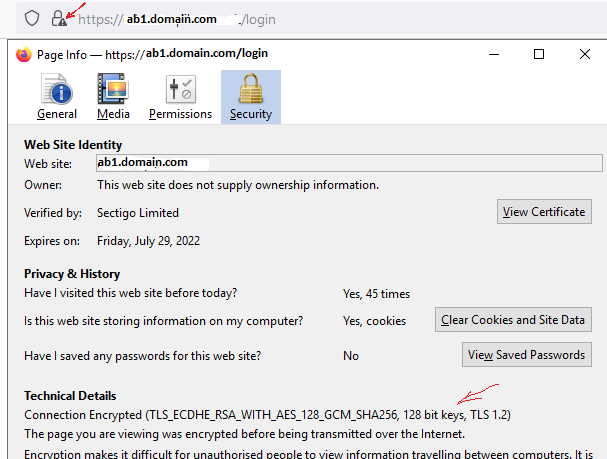
I removed any proxy/load balancer between the connector and the web app ( nginx server ). The traffic on ports 80 and 443 is forwarded with iptables straight to the nginx container.
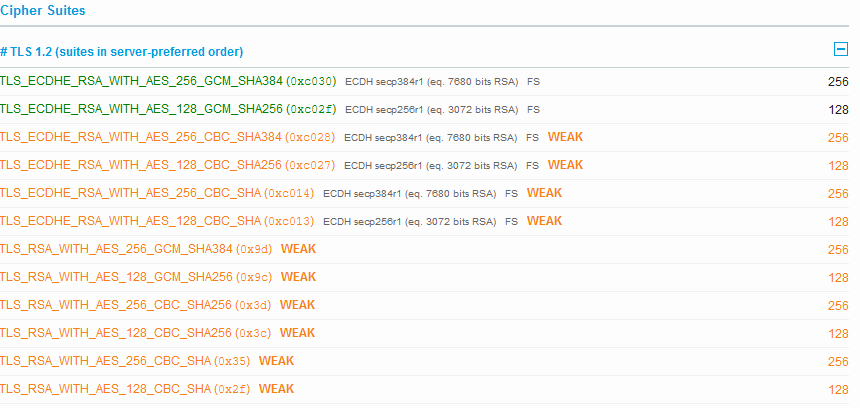
I've scanned ab.domian.com on sslabs and TLS v1.2 is supported + below cyphers:
The problem seems to be with the certificate presented to App Connector by nginx. ( Event 13001 )
The files/certificates recieved from Comodo are the ones below:
510739237repl_1.crt
AAACertificateServices.crt
SectigoRSADomainValidationSecureServerCA.crt
USERTrustRSAAAACA.crt
I've created the certificate for nginx with cat 510739237repl_1.crt SectigoRSADomainValidationSecureServerCA.crt USERTrustRSAAAACA.crt > mycert.pem
I have tried using only 510739237repl_1.crt as well.
In nginx config file I have the following directives:
ssl_certificate mycert.pem;
ssl_certificate_key private.key; ( private key used to generate the CSR )
Generate the pfx certificate required in Azure AD App Proxy:
openssl pkcs12 -export -out certificate.pfx -inkey private.key -in mycert.pem
I have tried a self-signed certificate and the result is the same - ( Event 13001 )
Do I need to have the certificates and/or the private key uploaded on the connector machine ? Or maybe what I'm trying to achieve is not possible because the connector is not on the same network with the web app ?
Many thanks
Claudiu D.