We have two Policies (and scripts) folders in our SYSVOL folder. It stays in sync on all six of our DCs. But I want to clean this up. How do I get rid of the oddly named "Policies_NTFRS_xxxx" folder and only have "Policies" folder? Same for Scripts as well...
It seems there are a lot of inaccessible folders in my correctly named Policies folder. I've tried running some icacls scripts I found in the forums here but it tells me it doesn't have permissions to run, even from an elevated PS prompt. I cannot take ownership of the folders at all either.
If I try to take ownership of the folders, it tells me I don't have permissions, even after attempting to take ownership with administrator permissions.
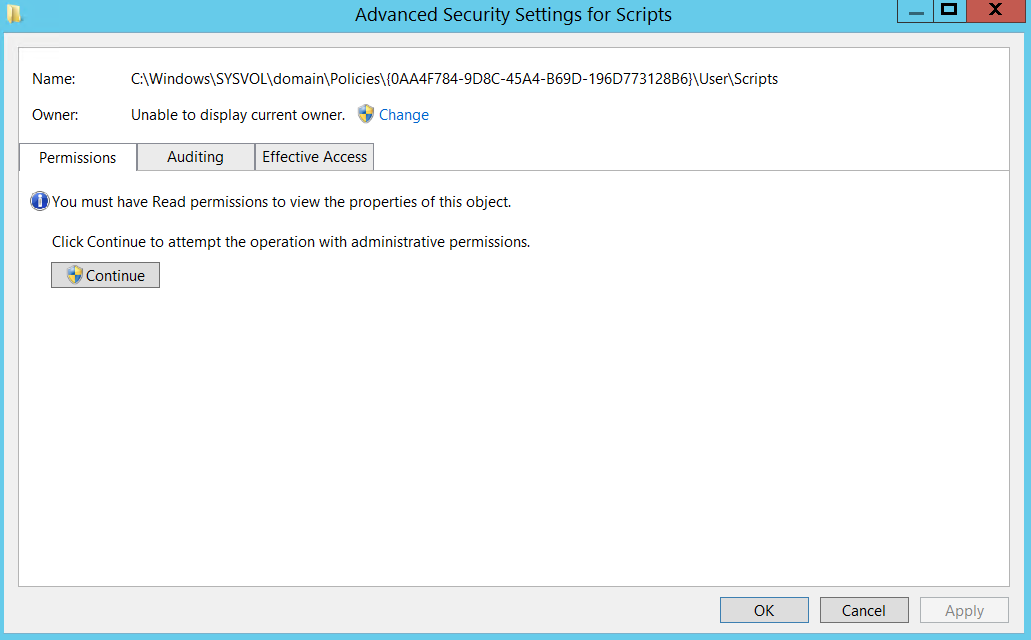
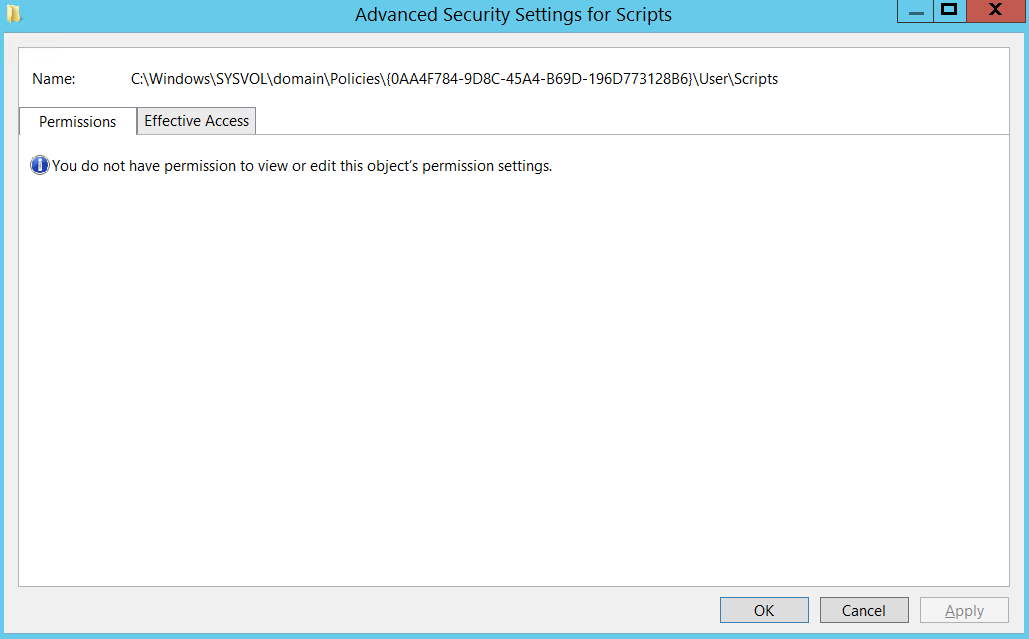
The script I tried to run is this:
$Policies = Get-ChildItem C:\Windows\SYSVOL\domain\Policies -Name -Filter "{*}"
foreach ($Policy in $Policies) {
icacls "C:\Windows\SYSVOL\domain\Policies\$policy" /remove:g "<domain>\Domain Admins"
icacls "C:\Windows\SYSVOL\domain\Policies\$policy" /grant "<domain>\Domain Admins:(OI)(CI)(F)"
icacls "C:\Windows\SYSVOL\domain\Policies\$policy"
}
It works for every folder in my oddly named Policies folder, but when I run it on my normally named Policies folder I get a bunch of inaccessible files errors.
icacls : C:\Windows\SYSVOL\domain\Policies{2F8111C2-4632-4D12-B8BF-DFE08204C2DE}: Access is denied.
I went through my excess GPOs we no longer use and removed them via group policy manager and replication appears to work across DCs as the count of GPOs has increased and decreased accordingly. Just our ACL permissions are wrong according to GPMC.
What is the proper way to fix this? How can I take ownership, purge the bad folders, and get rid of the oddly named policies (and scripts) folders so I only have one main Policies and Scripts layout as intended with AD?
Currently, we are on Server 2012 R2 with plans to upgrade in a few weeks to 2019 possibly if time permits and I can get this sorted out ;)
Update: I also have tried to go into GPMC -> delegations -> advanced -> advanced -> restore defaults ... for each remaining GPO we have. Yet the GPMC still reports ACLs errors...

