Perhaps your expectations are wrong, using the authorize endpoint will require you to enter credentials as detailed in the documentation, before returning an auth code or token: https://learn.microsoft.com/en-us/graph/auth-v2-user#2-get-authorization
As noted in the article, if using SSO you might be able to get the token directly, but that will not always work.
If you want to complete the flow by providing credentials directly, use the ROPC flow: https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc
Or client credentials: https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-client-creds-grant-flow#get-a-token
I am unable to get access token from the microsoft active directory graph api.
ahmad nawaz
21
Reputation points
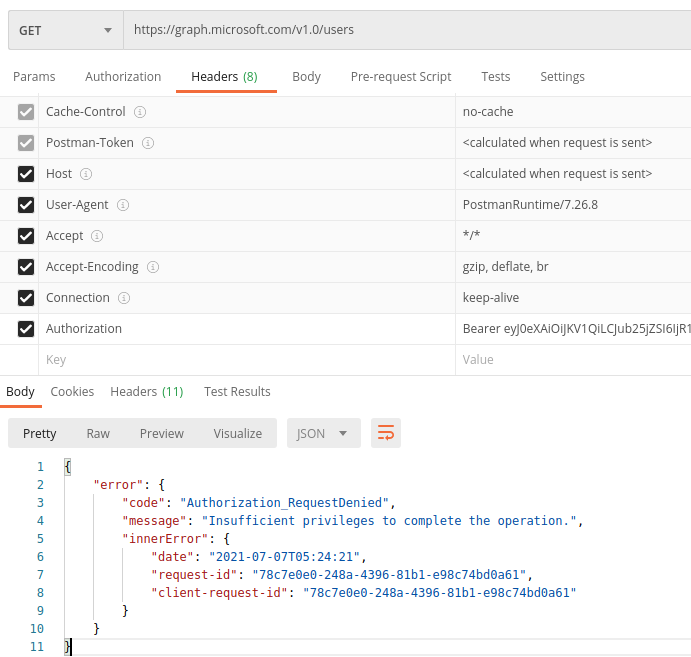
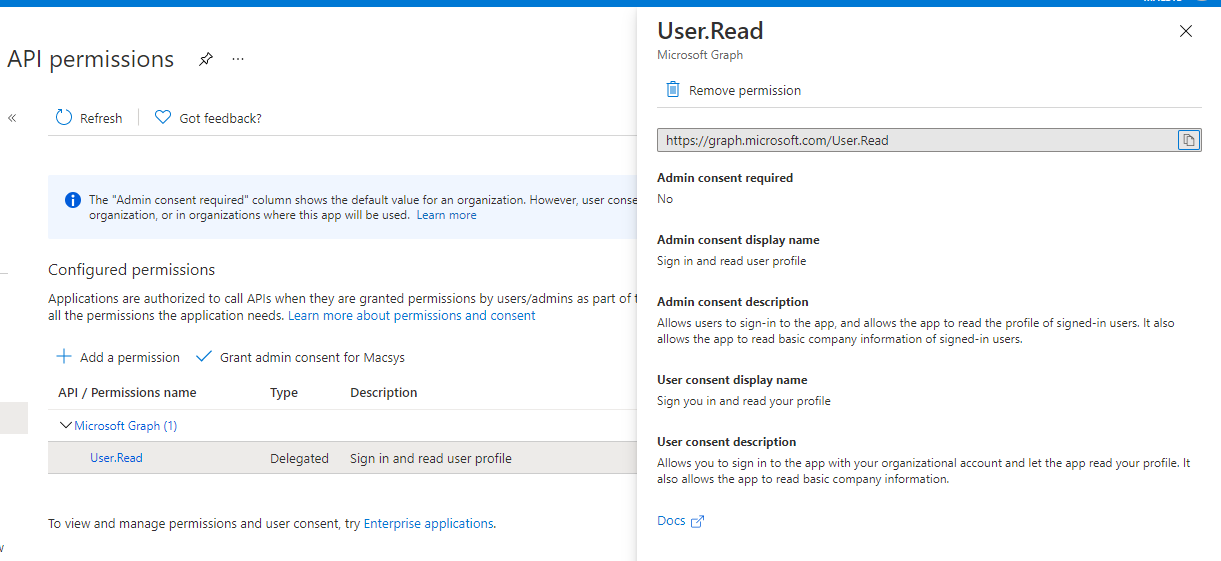
Here is my postman screenshot.
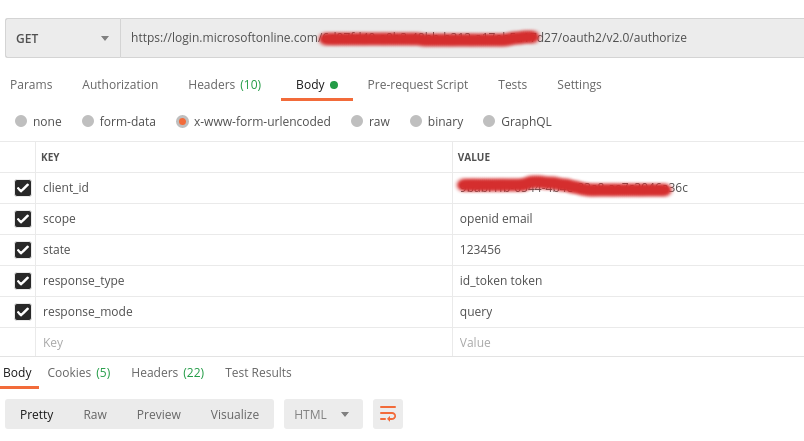
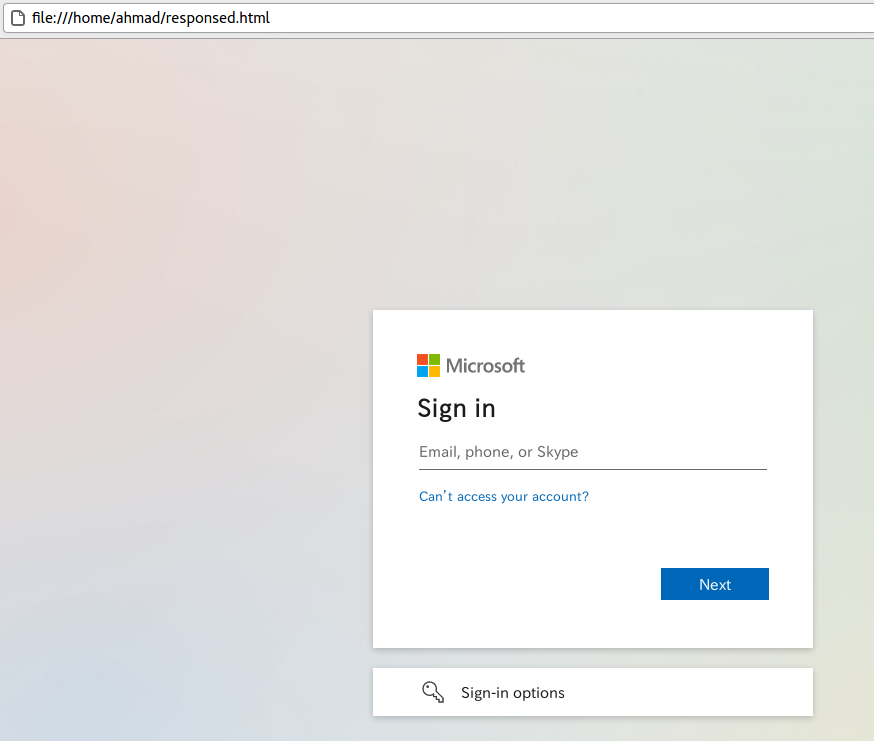
In response, I am getting a sign-in form. I saved the response in HTML file and it opens like this.
My requirements are simple.
I need to call https://login.microsoftonline.com/{tenant}/oauth2/v2.0/authorize to get the code that is necessary for getting the token.
Then I want to call {tenant}/oauth2/v2.0/token to get the access token
Then I want to call /oidc/userinfo to get the users of AD.
Is anything I am doing wrong?
Accepted answer
-
 Vasil Michev 100.2K Reputation points MVP
Vasil Michev 100.2K Reputation points MVP2021-07-06T13:26:22.397+00:00