@SWA5534 Thanks for reaching out.
You cannot control the user behavior on their personal devices. They always have the control to access any service from any browser/app they want. If you are concern about someone login in to Office services from a anonymous IP address which might originate from a TOR based network (Dark web if you consider this) then you can implement the Azure AD Identity protection which flags these scenarios under HIGH Risk users and you have option to investigate that with Azure Sentinel.
If you want more control, you must allow data/services access only via the corporate devices (Azure AD joined, Hybrid AAD joined ) where you can put more granular control over what your end user do. You have options to control app installations and even control what flows through your network (Corp net)
On corporate devices behind firewall, you can monitor any traffic which goes to unidentified area and may cause issues later. For example, if you have Palo Alto Firewall, you can add that as a Connector in Microsoft Sentinel and have sentinel generate some alerts on basis of that.
Dark web does not necessarily means bad, the end user might be just using any specific browsers (Like TOR) for anonymity towards some other services. This should always be investigated as if the services lies in TOR network, they are almost impossible to trace without any Exit Nodes.
Here is one example, how a user sign in from a TOR browser can be detected using AAD Identity protection and passed on to Sentinel for Investigation :
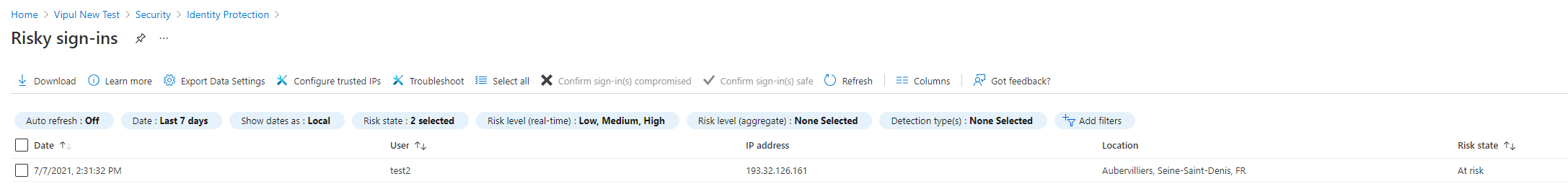
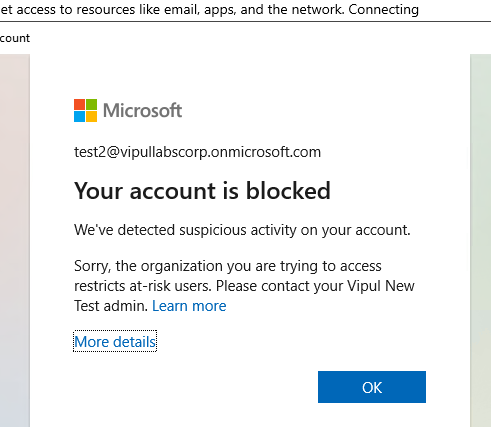
The user is then blocked automatically after this when AAD detects it.
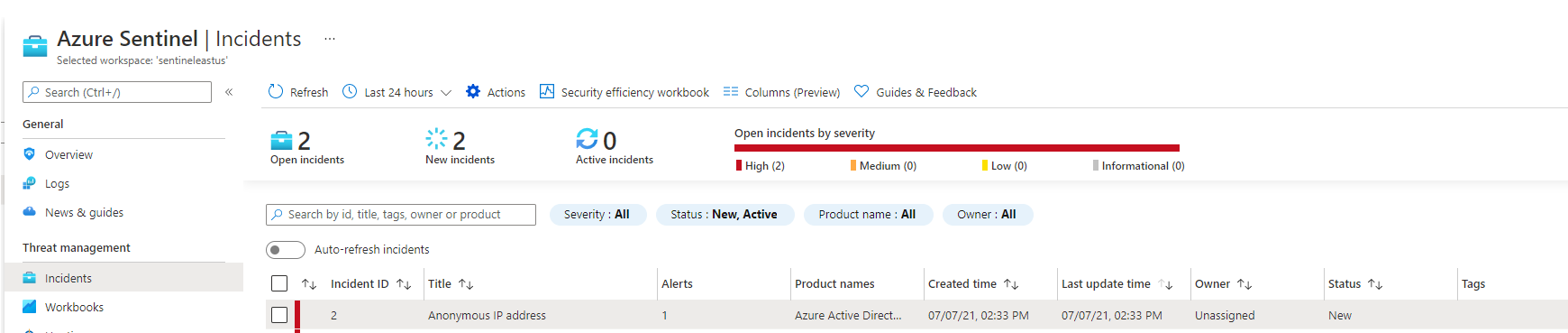
Under Sentinel, you get this type of Alert Incident created :
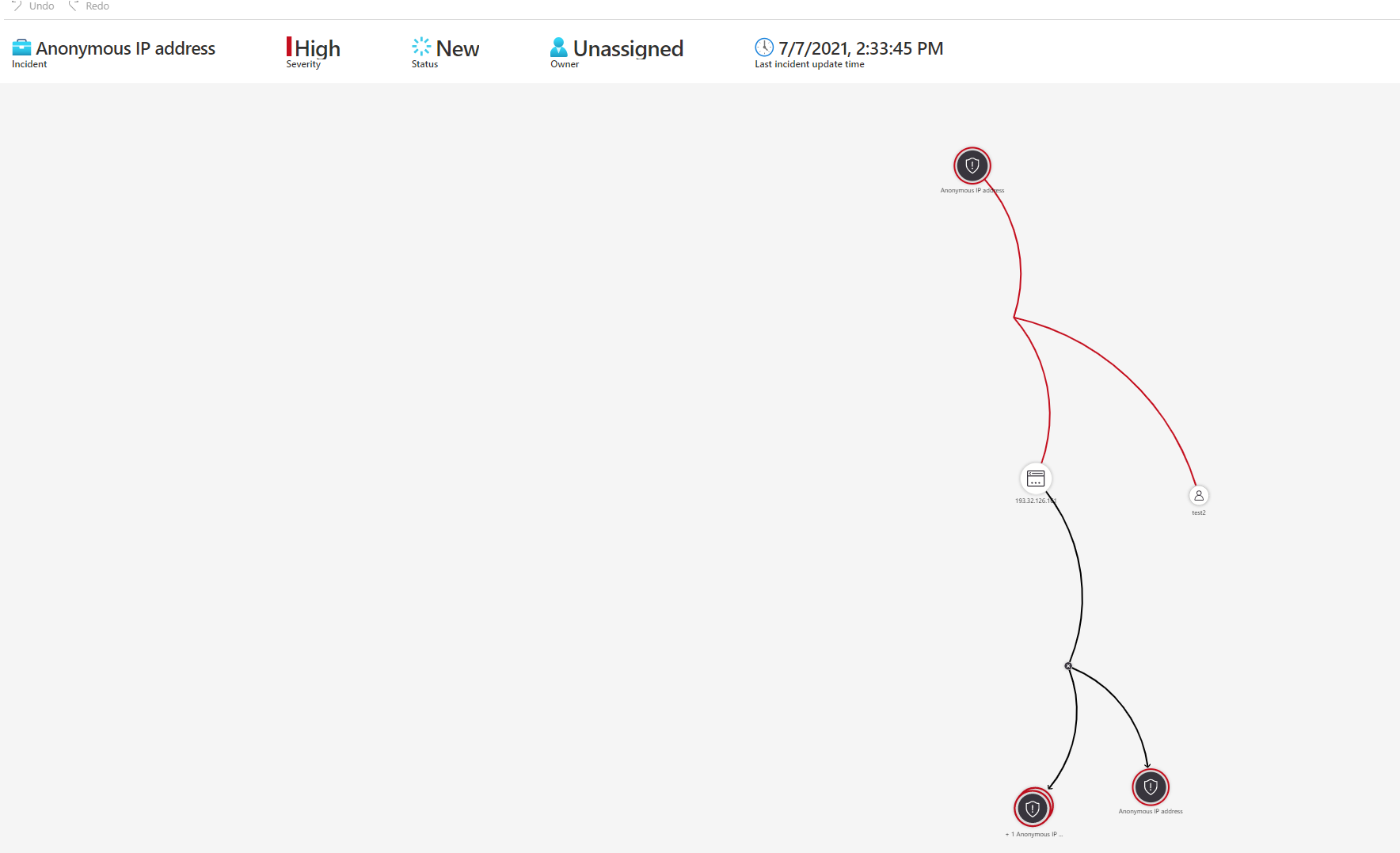
Which you when try to investigate using the Investigate option, it can tell you the entities it captured (Like which machine, user, IP etc) which can allow you to take further actions.
-----------------------------------------------------------------------------------------------------------------
If the suggested response helped you resolve your issue, please do not forget to accept the response as Answer and "Up-Vote" for the answer that helped you for benefit of the community.