Maybe something here helps.
https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4624
Computer Account Logon
Hi, i have a quick question. How often does a "computer account" (not to confused with a user logon) logon against a DC? I've been reviewing security logs and i've noticed quite frequent computer account logins (4624). Those logon events do not correlate to the "lastLogon" value of the Computer Account object
Subject:
Security ID: NULL SID
Account Name: -
Account Domain: -
Logon ID: 0x0
Logon Type: 3
New Logon:
Security ID: Domain\PC-102$
Account Name: PC-102$
Account Domain: Domain
Logon ID: 0x61fe8f7ee
Logon GUID: {86e8f2f4-eb16-50e6-0470-11525ea0d275}
Process Information:
Process ID: 0x0
Process Name: -
Network Information:
Workstation Name:
Source Network Address: 192.168.253.66
Source Port: 37776
Detailed Authentication Information:
Logon Process: Kerberos
Authentication Package: Kerberos
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
9 answers
Sort by: Most helpful
-
 Dave Patrick 426.1K Reputation points MVP
Dave Patrick 426.1K Reputation points MVP2020-07-14T22:03:32.17+00:00 -
S.Sengupta 15,266 Reputation points MVP
2020-07-15T01:20:44.91+00:00 I shall also suggest you to go through:
-
Daisy Zhou 18,706 Reputation points Microsoft Vendor
2020-07-15T03:40:59.453+00:00 Hello,
Thank you for posting in our Q&A forum.Based on the test in my lab, if the domain computer is connected to the domain network.
And if we do the following actions(maybe it also includes other actions that I didn’t think of), the computer will logon:
1.Restart the domain computer
2.Shut down and start the domain computer
3.Update domain group policy about comuter (such as run gpupdate /force or gpupdate /force /target:computer on domain computer manually, or the domain computer update domain GPO in the background)
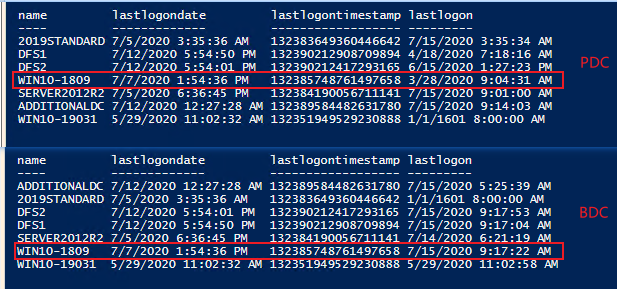
4.Establish a secure channel or update a secure channel between the domain computer and domain controller.I think it is "LastLogon" of the domain computer, it is only updated on one DC, that means this attribute is not replicated. We can get the "LastLogon" about computers in the domain with command on every DC in the domain and the lastest date value is the "LastLogon" value:
****Get-ADComputer -Filter * -Properties lastlogon,lastlogondate,lastlogontimestamp | select -Property name,lastlogondate,lastlogontimestamp,@{n="lastlogon";e={[datetime]::FromFileTime($_.lastlogon)}}****
For example, I have two DCs in the domain (Win10-1809):
For more information about secure channel, we can refer to the link below.
Detailed Concepts: Secure Channel Explained
https://social.technet.microsoft.com/wiki/contents/articles/24644.detailed-concepts-secure-channel-explained.aspx?Sort=MostUseful&PageIndex=1 -
Joe 1 Reputation point
2020-07-16T00:06:19.25+00:00 Hi Daisy,
Thanks so much for the response and detailed info. Very helpful.
So tested this a demo environment with a single DC. The events on the single DC are still not aligned with the "LastLogon" value
@DSPatrick and @SSengupta-4080 the provided links are for "user" logon events "contoso\administrator", not for a computer logon.
-
Daisy Zhou 18,706 Reputation points Microsoft Vendor
2020-07-16T09:11:38.07+00:00 Hi Jeo-4025,
How do you test it?I did test before in my lab:
1.Logon one domain-joined client, and run gpupdate /force or restart machine.
2.Then check event ID 4624 on this domain client or run the command above on DC, I can see the date/time is the time when I run gpupdate /force or restart machine.