Does this help?
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/outlook-s-mime-certificate-selection/ba-p/1128440
S/MIME Encryption, which public key of recipient was used
Does anyone know of a way how to figure out which public key (certificate) Outlook used to encrypt mail for a certain recipient?
The idea is that we are using AD-integrated Certificates and one user has 4 published certificates linked to his AD object. Now another user from our organization (Outlook/Active Directory/Exchange on-prem), just sent an email with S/MIME via Outlook to this recipient. And we'd like to figure out which certificate (from the 4) his Outlook used to encrypt the mail? Because if any other user sends an encrypted message to this recipient, the certificate with longest validity is used and the recipient can open this mail just fine. This he cannot do for the email of my first sender.
kind regards,
Dieter
4 additional answers
Sort by: Most helpful
-
 Evgenij Smirnov 541 Reputation points
Evgenij Smirnov 541 Reputation points2021-07-12T13:28:33.86+00:00 And on another note: Does the problematic sender, by any chance, have the recipient stored as contact in Outlook? If that contact has a certificate stored in it, chances are it will get used.
-
Dieter Tontsch (GMail) 937 Reputation points
2021-07-12T14:31:43.13+00:00 Thanks, this is quite sophisticated, we are trying to figure it out based on that. But this definitely helps. Would have been nicer if there would have been some possibility to check on recipients certificate within the email, though.
-
Dieter Tontsch (GMail) 937 Reputation points
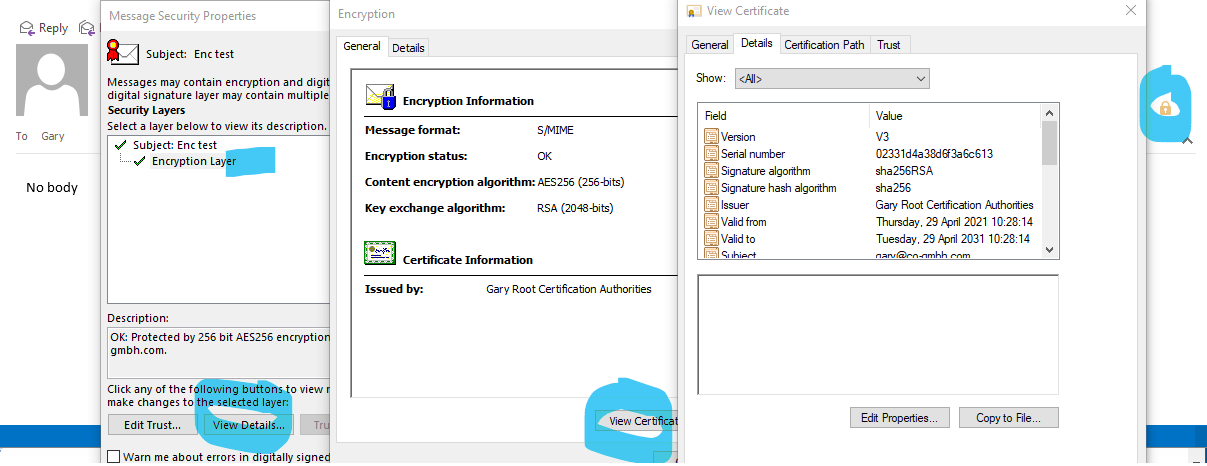
2021-07-12T15:34:14.607+00:00 OK @Gary Nebbett ,
you are partially right. If the recipient is able to open the Email he/she will be able to see, the way you described it, which certificate was used to encrypt. As a sender, like in sent items, I do not see this option. There I can only see my certificate, e.g. the one of the sender, like myself.
But what if the recipient, due to missing matching certificate, actually priv. key of the certificate used, cannot open that email vor verification? Or can he? I don't see a chance to verify an encrypted email as long as i don't have the matching priv. key for it, as a recipient.
And again as the sender of this email I do not know which certificate I used to encrypt for this particular recipient. That is my problem. But still, your post helped me. I have overseen this. I knew about this padlock, but I always thought it only shows information of the sender.
cheers,
Dieter -
 Gary Nebbett 5,851 Reputation points
Gary Nebbett 5,851 Reputation points2021-07-12T15:51:01.63+00:00 Hello @Anonymous ,
If the easy way does not work, you could try the hard way - this should work for both the sender (message in Sent Items) and the recipient.
The Transport Message Headers of the message will probably contain lines like:
Content-Type: application/pkcs7-mime; smime-type=enveloped-data; name="smime.p7m" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="smime.p7m"The first step is to export the smime.p7m attachment to a file. That is easier said than done, since Outlook does not seem to provide such a function; I use MFCMAPI:
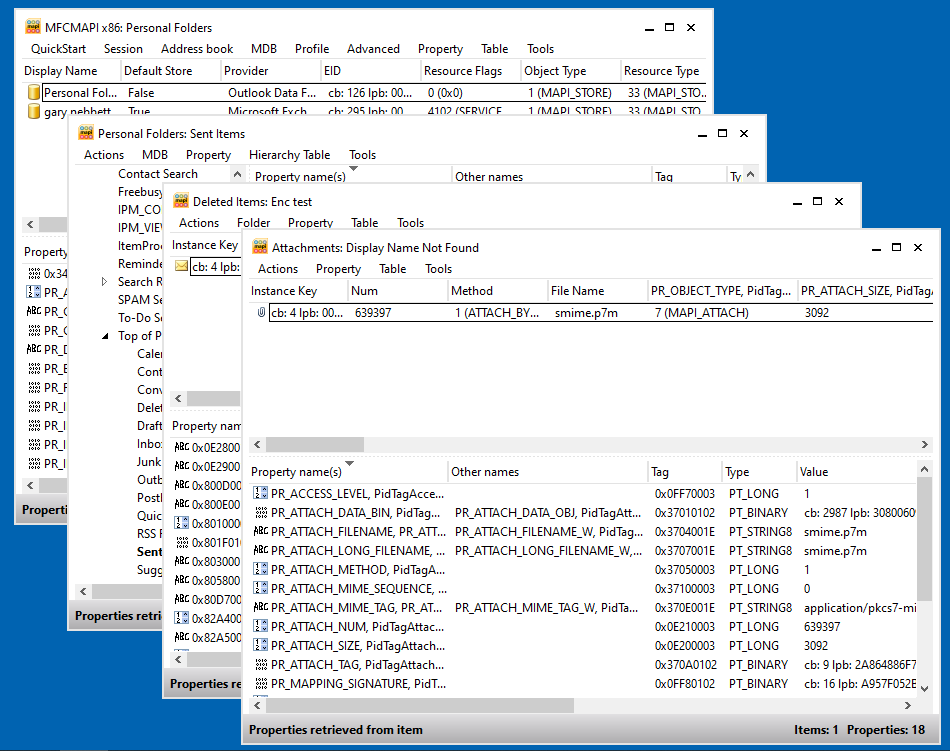
The saved file (smime.p7m) is a PKCS #7 enveloped data DER encoded binary blob (the base64 encoding is decoded when saving the data) - just use your favourite ASN.1 dumper (or perhaps just
certutil -asn smime.p7m) to see its contents (which identifies the certificate via issuer and serial number information).Gary