Hello!
While testing tiered AD infrastructer I was greatly suprised to see how one of the key gpo parameters is working.
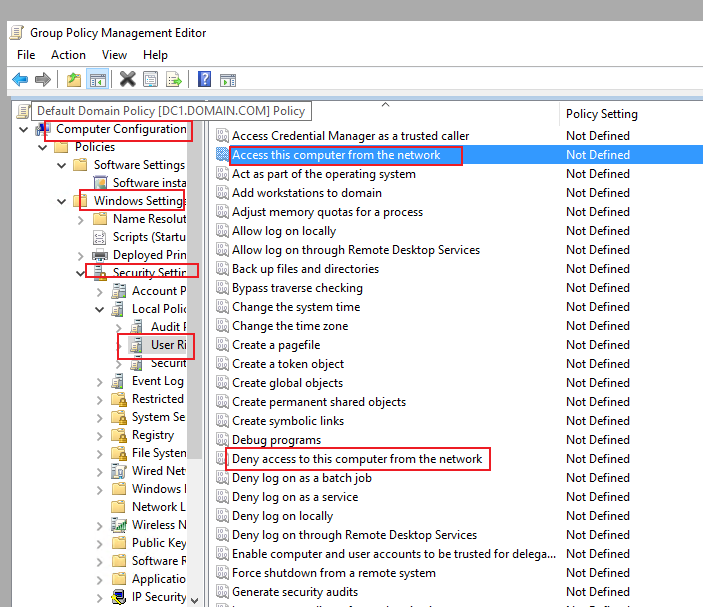
Suppose there's a domain controller - DC - which belongs to Tier0 OU (with no gpo applied except the Default Domain Policy) and a number of servers in the SERVERS OU (Tier1) to which the gpo with the following setting is applied:
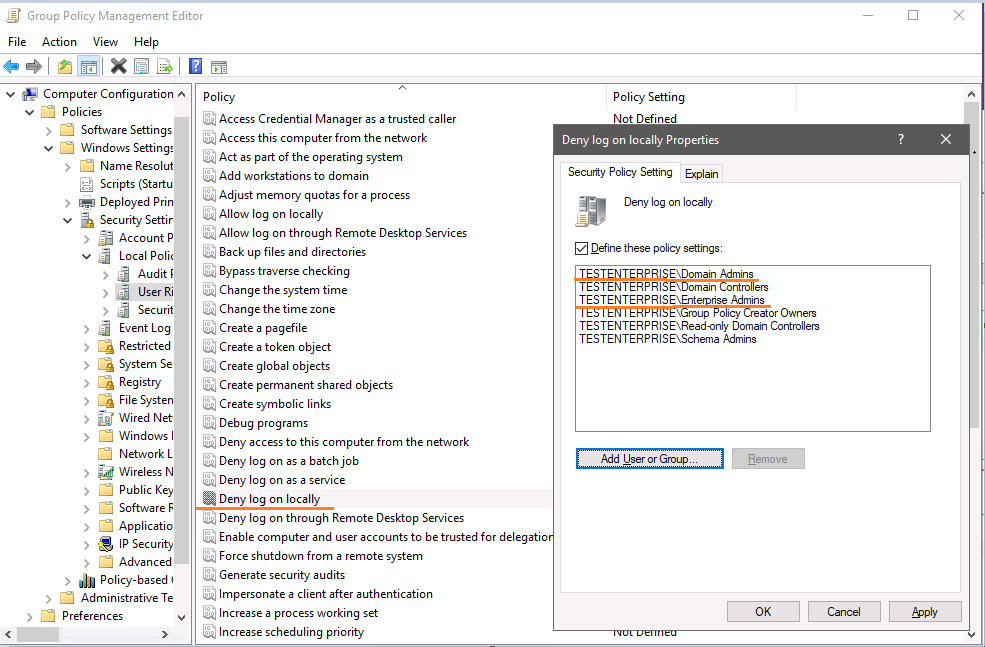
The most important idea in the tiered AD model is preventing the cross-tier logons - in other words, you should not be able to log on to Tier1 servers under Tier0 accounts - in my case it means I shouldn't be able to use any domain/enterprise admin accounts (which are Tier0 accounts) for logging onto Tier1 servers (in the SERVERS OU), and the aforementioned Deny log on locally policy setting is the setting that is supposed to do exactly that.
And it really does what I expect it to do - any domain/enterprise-wide administrative accounts can no longer log on to Tier1 servers - so far so good, but... either I'm missing something or enabling this option may lead to other - rather weird - consequences.
Once again: here's the MS's explanation of the Deny log on locally parameter:
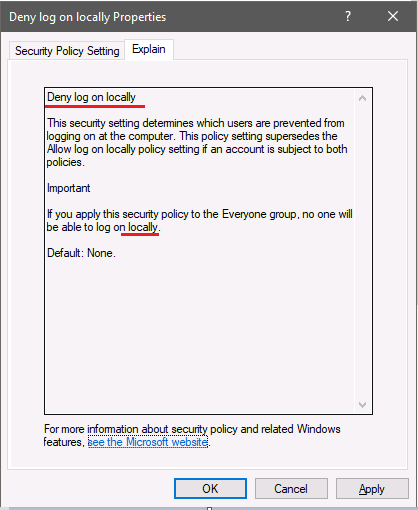
As far as I understand this text it means that the ONLY goal of this parameter is to deny log on locally TO THIS COMPUTER for the defined accounts.
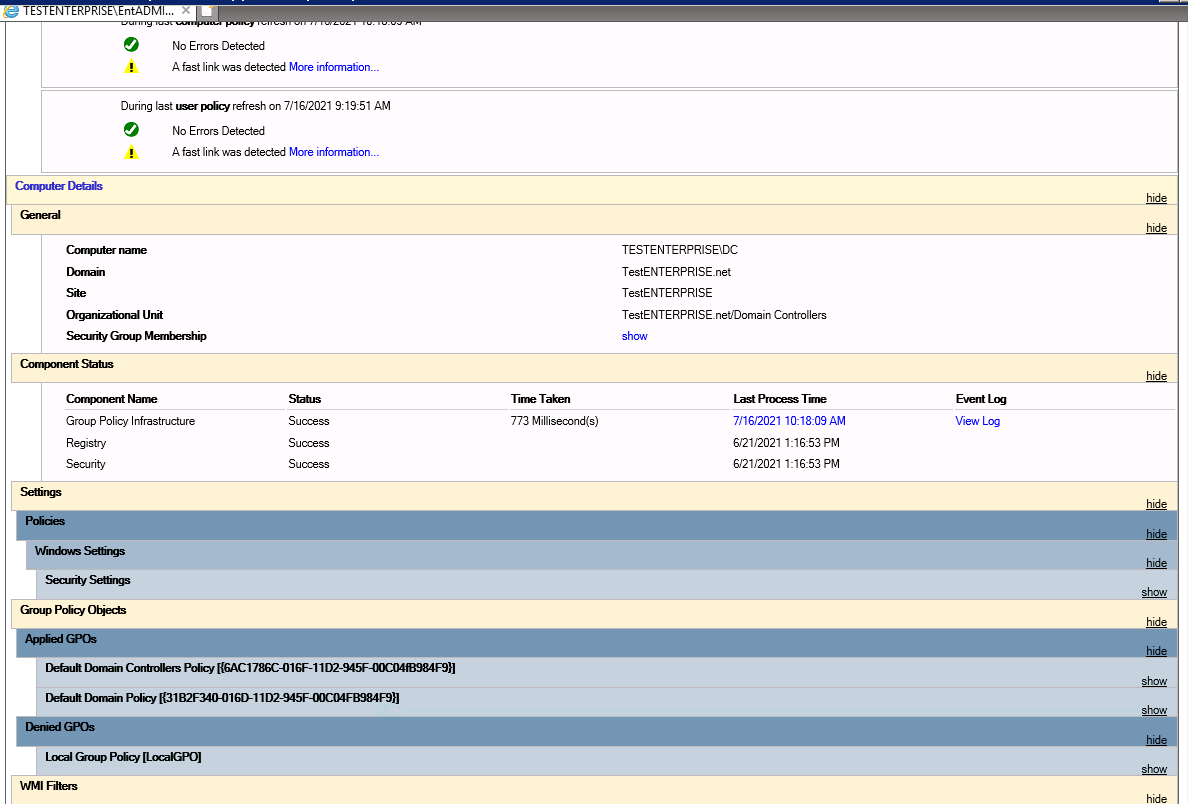
Why in this case I'm loosing the ability to connect to DC right after the policy gets applied?
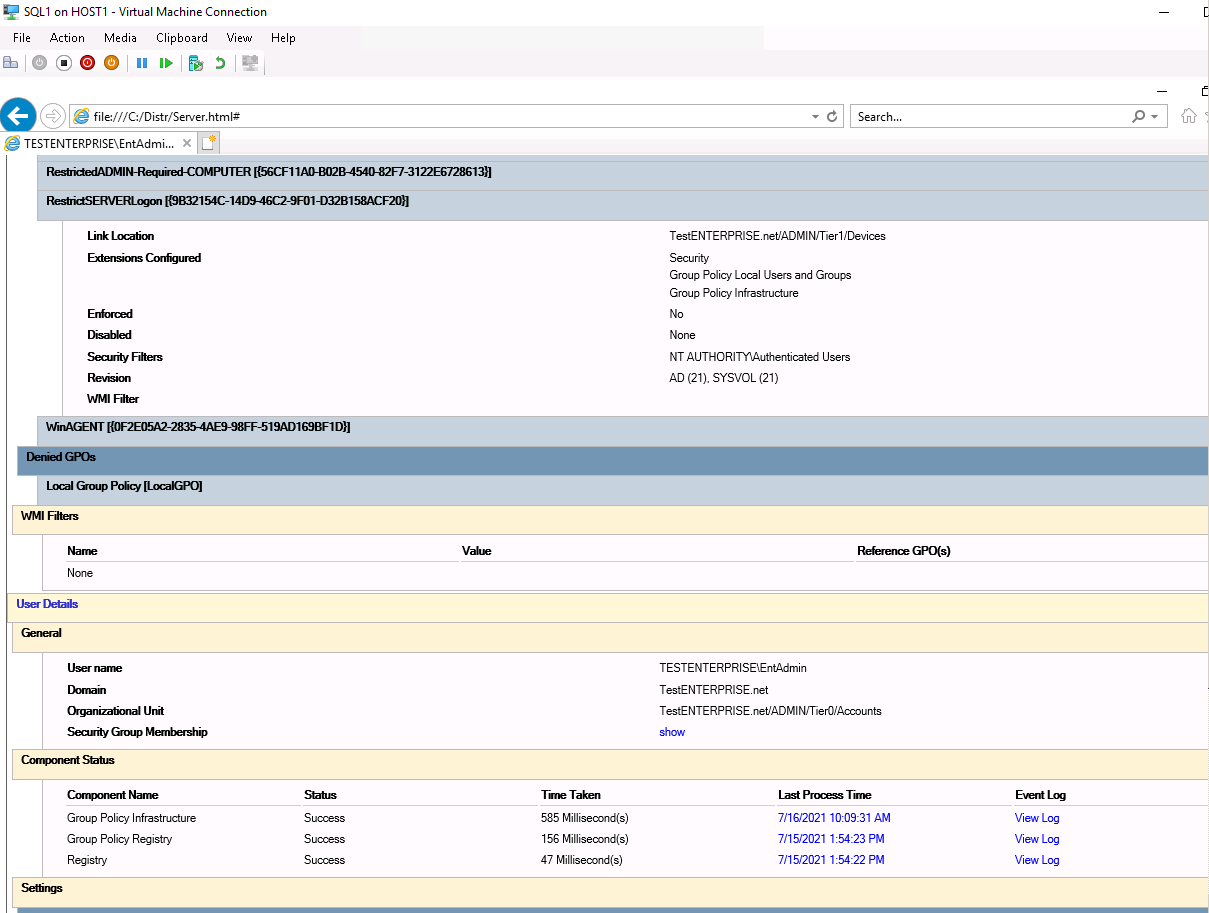
For example, when I try to access \dc as Domain\AdminT1 I see this:
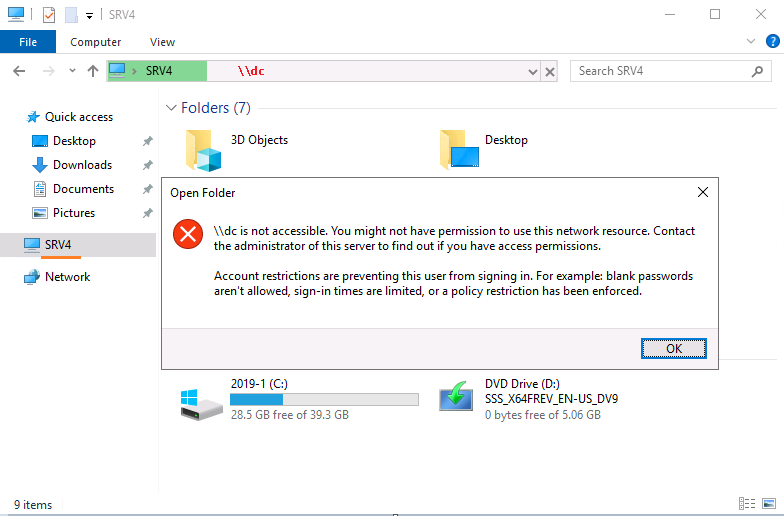
ANY domain user can access ANY domain computer by default so what is preventing Domain\AdminT1 from accessing \DC AFTER applying the policy ???
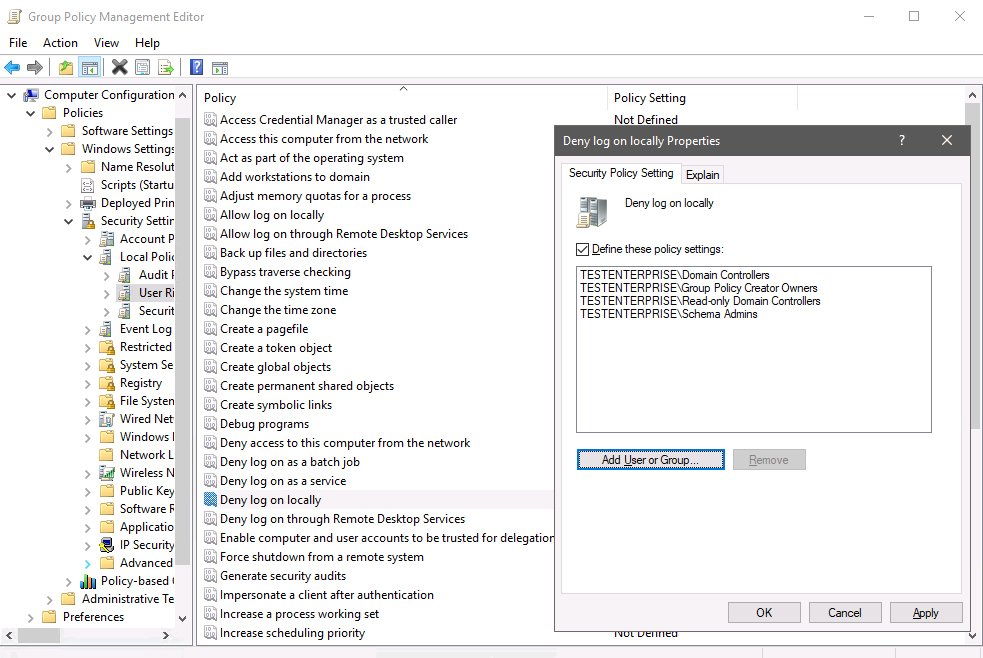
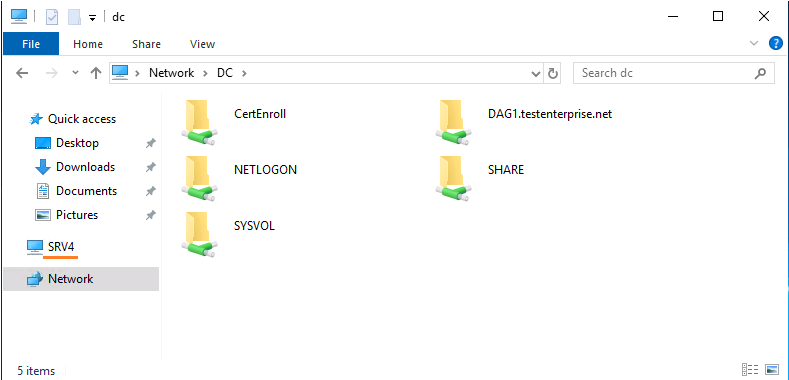
There're other gpo settings being applied but they do not have any effect on the possibility to connect to \dc - as soon as I delete the domain admins/enterprise admins accounts from the policy \dc gets accessible again:
???