Hello Experts,
hope you are doing well.
We are facing and issue where we see a large amounts of emails being moved to quarantine for a particular user. The emails are not spam or phish.
The user is using the integration for Outlook in Workable - https://www.workable.com/
However, communication is not only done through the integration in workable it's also done through the Outlook App in macOS, just adding this info for reference.
The issue seems to happen most often with "mail pyramids" where "reply" has been clicked more than a few times.
As of now the only way for me to release those those emails for the user is to go to:
https://security.microsoft.com/quarantine and manually release all the messages there.
Unfortunately, when the user navigates to the above link, does not see anything, so I have to do it as an admin.
What have I done to possibly solve this? Please feel free to correct me, if anything of the below is not as it should be.
In here:
https://security.microsoft.com/antispam -> I have created a separate Anti-Spam policy
Under "Users, groups, and domains" I have added only the particular user we are seeing this predominantly happen to.
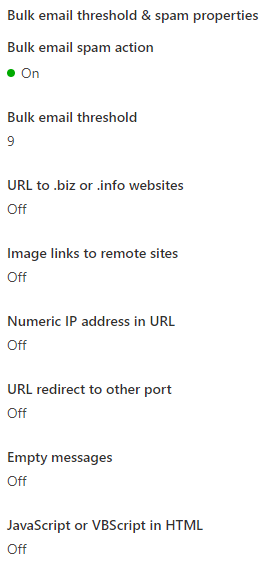
Bulk email threshold - I have set this to 9, with the hopes that this will reduce the sending of the email pyramids to Quarantine. I don't know if it's correlated, correct me if it isn't.
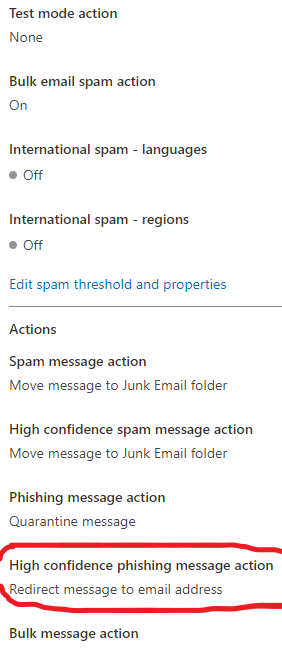
I've configured this setting to redirect High confidence phish emails:
"High confidence phishing message action
Redirect message to email address"
-Screenshots of the configuration attached for reference.
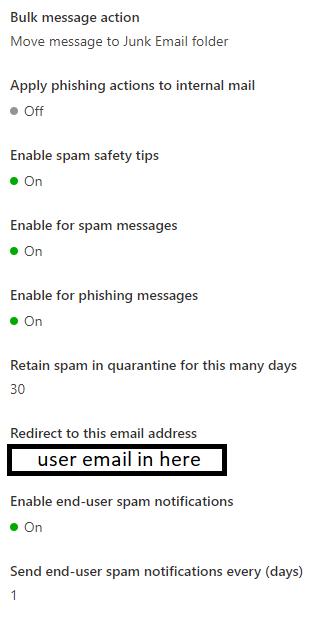
And the redirection email is set to the users email.
Will this newly configured granular policy work side by side with our default policy?
The idea is for the user to have the ability to receive the emails that are sent to quarantine, or somehow to review and release them.
The domains of the emails put in quarantine for the specific user are google, yahoo etc. Mostly popular and verified domains.
And this happens sometimes while using the Outlook integration and replying from it, but happens also while the user is going through the Outlook app for macOS.
Would there be some best practice configuration from Microsoft side in order to prevent this from happening when using the integration in Workable?
Although, we have emails put in quarantine for other uses too, we'd like to make an exception for the specific user if needed.
Any thoughts and advice on the matter is appreciated.
Thanks.