Hello @Stephen ,
Thank you so much for posting here.
Before removing the enterprise CA role, please make sure that all certificates that are issued by this CA will not be used. As mentioned, we could log on to the CA server and check all the issued certificates.
If we make sure that all the issued certificates will not be used, we could then revoke all the certificate and decommission the CA. Otherwise, we need to configure the third party certificates to replace the issued certificates that will still be used.
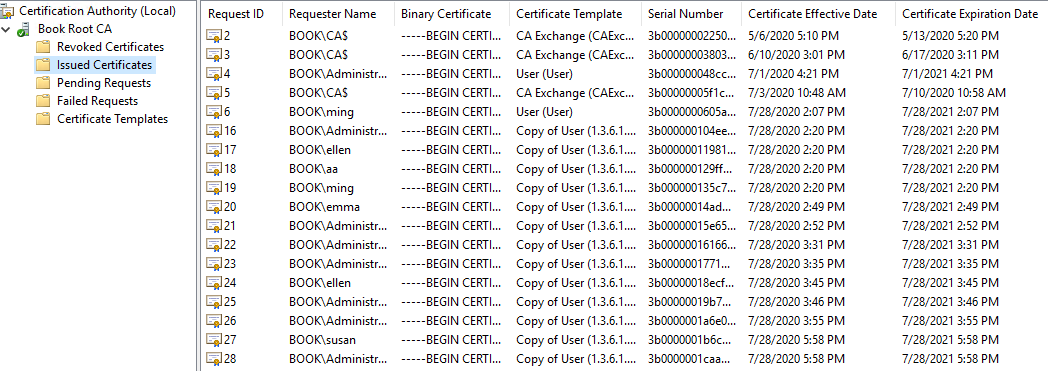
Based on my experience, removing the Enterprise CA Role will have no impact on the domain trust. As we know, there is no certificate involved during the domain trust creation.
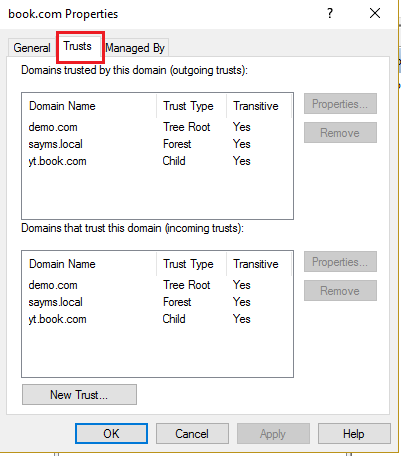
For the information about decommission a Windows enterprise CA, please refer to:
https://learn.microsoft.com/en-US/troubleshoot/windows-server/windows-security/decommission-enterprise-certification-authority-and-remove-objects
For any question, please feel free to post here.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
