Hi ,
Our forum mainly focus on Radius authentication issue, please understand we are not familiar with Windows Azure CRP Certificate Generator and have no azure environment to do the test. For azure part, you can add the related azure tag.
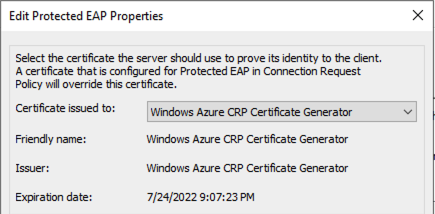
It's currently using Windows Azure CRP Certificate Generator, however when I upload our certificate and change it from the Network Policies clients are unable to authenticate to the Wireless Network.
Could you please clarify more details? Did you mean upload certificate to Windows Azure CRP Certificate Generator and then authentication failed or change Windows Azure CRP Certificate Generator to custom certificate then authentication failed?
How did you generate custom certificate?By ADCS or thir-party CA?
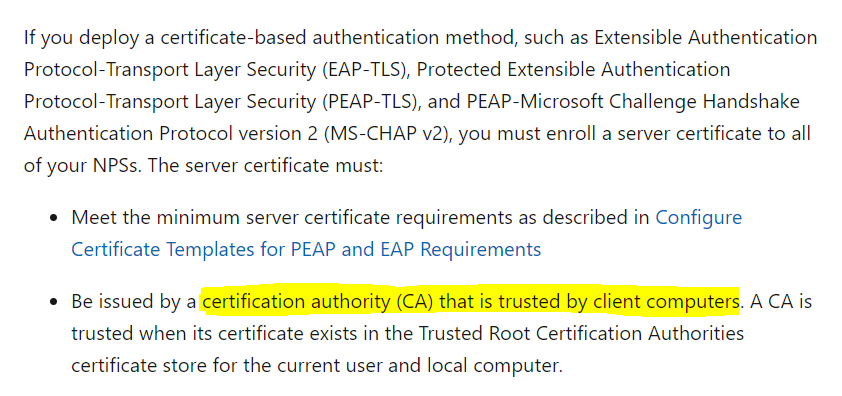
If you deploy a certificate-based authentication method, such as EAP-TLS, PEAP-TLS and PEAP-MSCHAP-v2, you must enroll a server certificate to all of your NPSs. The server certificate must be issued by a certification authority (CA) that is trusted by client computers.
For your reference:
Manage Certificates Used with NPS
So your client machine must trust your Root CA. You can also enable CAPI2 event log, it is useful for troubleshooting certificate-related issues. By default, this log isn't enabled. To enable this log, expand Event Viewer (Local)\Applications and Services Logs\Microsoft\Windows\CAPI2, select and hold (or right-click) Operational, and then select Enable Log. Then reproduce the issue again to generate related event log.
The following article talking about how to troubleshoot 802.1X authentication issue, you could have look:
Advanced troubleshooting 802.1X authentication
Best Regards,
Candy
--------------------------------------------------------------
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.