Hi Daisy,
Thank you. Unfortunately, I am confused by your reply below.
You said: “Meanwhile, the gpo setting is "Network security: Restrict NTLM: NTLM authentication in this domain" instead of "Restrict NTLM Audit NTLM authentication in this domain policy setting" you mentioned.
So you should change "Restrict NTLM Audit NTLM authentication in this domain policy setting" to "Disabled" first. This is to revoke this setting and cannot be set to any other value.”
Why would I disable the audit setting? Isn’t the whole point of this setting to understand and see the traffic that may be affected by disabling the NTLM settings? This should be informative only and not have an impact on the disable setting options. Wouldn’t you want to see what might be impacted before making any of the “Deny” setting change? Unless I am mistaken, this, as an audit setting, should not have any impact on any of the “Deny” settings.
You then said: “After that, you should evaluate whether you can disable NTLM authentication in your environment.” This is what I am trying to do but it is not clear on how best to do this.
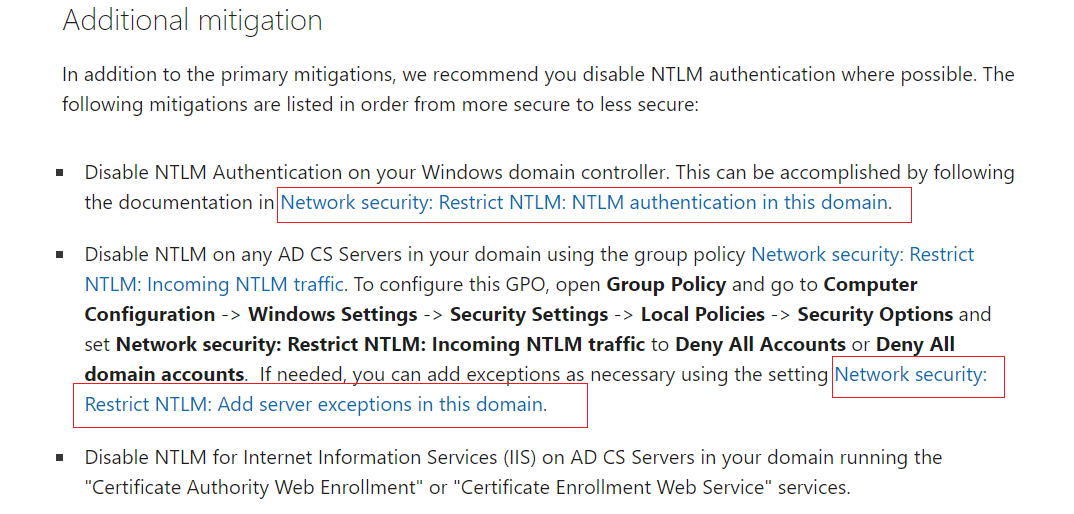
You included a screen shot of the Additional mitigation section fromhttps://support.microsoft.com/en-us/topic/kb5005413-mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-3612b773-4043-4aa9-b23d-b87910cd34291.
However, my understanding is that this is meant to be done in addition to selecting one of the Deny options from the Network security: Restrict NTLM: NTLM authentication in this domain document referenced https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-security-restrict-ntlm-ntlm-authentication-in-this-domain
This brings me back to square one.
Each of the Deny options states: “ The NTLM authentication attempts will be blocked and will return an NTLM blocked error unless the server name is on the exception list in the Network security: Restrict NTLM: Add server exceptions in this domain policy setting.”
When I check the Applications and Services Log\Microsoft\Windows\NTLM. Log, on the domain controller I see the domain controller next to the “Computer” label in the log. The exchange server appears next to the “Secure Channel name” label. What is this saying? Is this stating I need to add the domain controller and\or the exchange server FQDN to the server list in Network security: Restrict NTLM: Add server exceptions in this domain security policy setting?
The problem it seems is that according to the documenthttps://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-security-restrict-ntlm-add-server-exceptions-in-this-domain3 it states:
“If you define an exception list of servers in this domain to which client computers are allowed to use NTLM pass-through authentication, then NTLM authentication traffic will continue to flow between those servers, which make them vulnerable to any malicious attack that takes advantage of security weaknesses in NTLM. “ This would defeat the whole purpose of the Deny settings.
I guess, the main question is how do I determine if NTLM is truly a concern for our environment and if so, what Deny Option setting do I use to block this but not cause a problem with staff not being able to log into the desktop Outlook client resulting in their credentials being rejected\ignored?
Thank you,
Roger