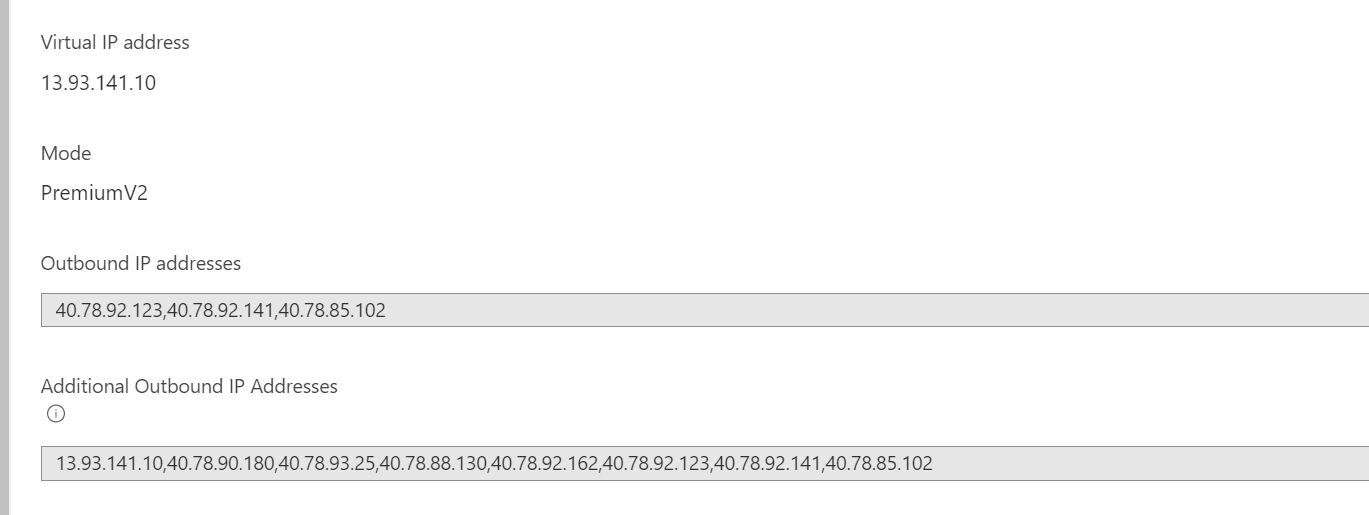
If the Web App is VNET integrated with a subnet that has the Microsoft.Web Service Endpoint enabled, then this behavior is expected. It is by design that when the Microsoft.Web endpoint is enabled, the normal IPv4 outbound IP is no longer used. Instead, any communications will go through special tunneling using IPv6 outbound.
For adding this to a firewall, an easy way to do so is to add an allow rule by Subnet name to ensure all of its traffic is covered.
For the case where this firewall / other resource is outside of Azure / your subscription, one option would be to allow all IPv6 Azure addresses. This is because the IPv6 addresses which the subnet may use can be any of the addresses available to the Azure backplane.
Information on the IPv6 list is available for download here- Download Azure IP Ranges and Service Tags – Public Cloud from Official Microsoft Download Center
An alternative option would be to use NAT Gateway which assigns a single static outbound IP for the app.