Hi,
Regarding the issue of the domain accounts being locked, here are some common troubleshooting advice:
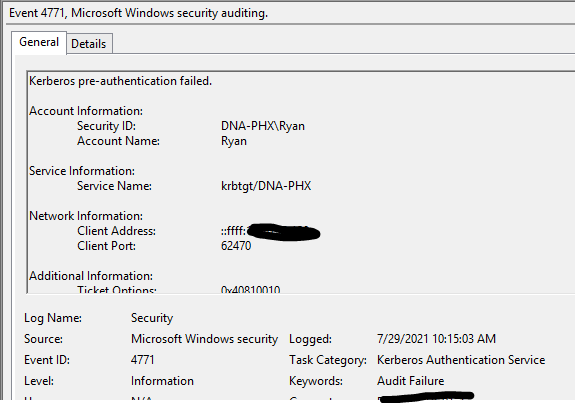
First, looking for event 4740 on the domain controller is, and the computer source can be found through this event (each domain controller needs to confirm whether there is this event); if not, need to enable the account management audit policy for the domain controller. , In [Computer Configuration \ Windows Settings \ Security Settings \ Local Policies \ Audit Policy \ Audit account management]
Then, find the 4625 events on the client computer source and check the process of the locked account. If there is no 4625 events on the computer source, you need to enable the following audit events:
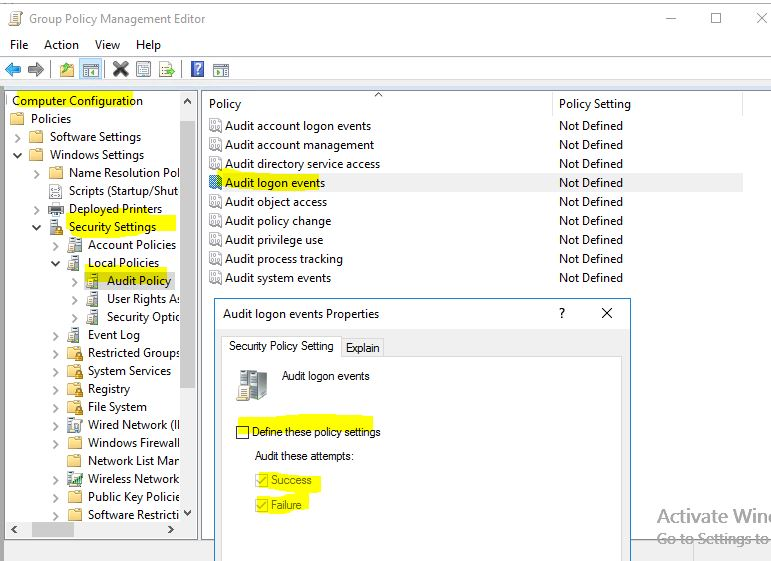
Tracking for this client, then analyze the event log to find out which process or apps send the BAD password.
If there are any progress, welcome to share here!
Best Regards,