Hi @Waqas Kayani ,
Thanks for using Microsoft Q&A !!
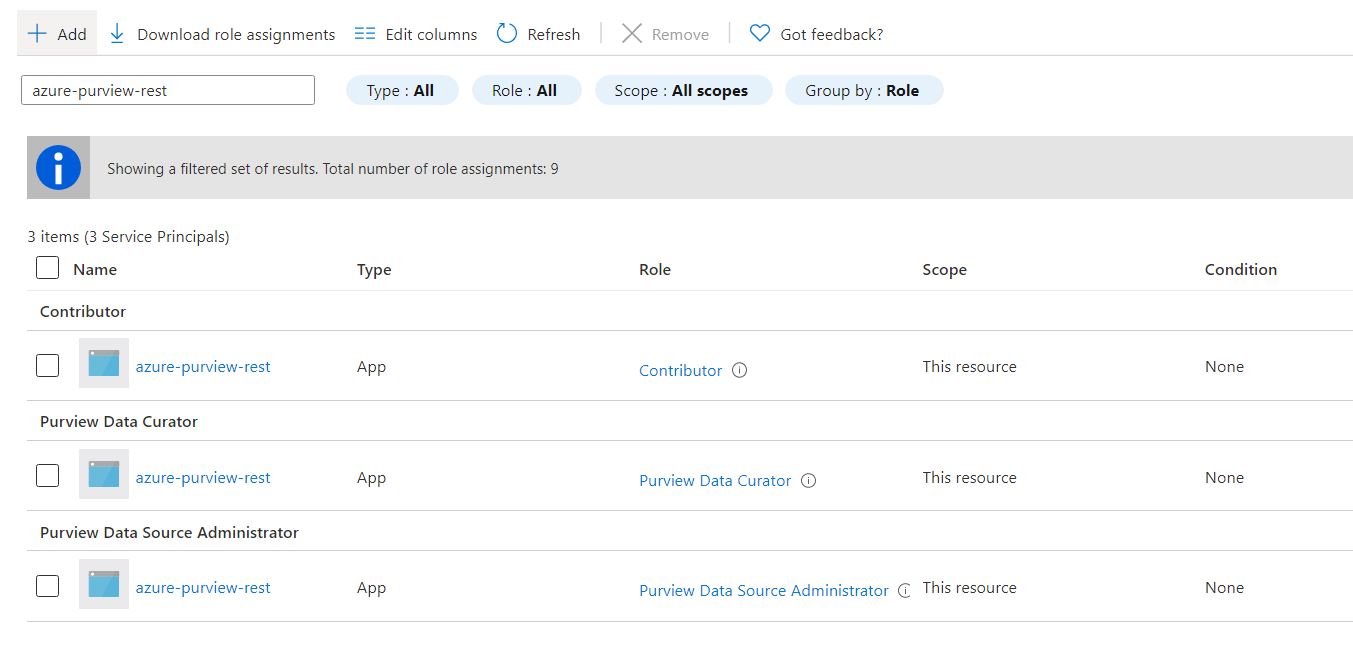
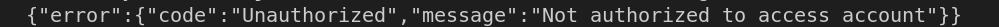
You are getting this error while using the scan endpoint as you have not provided proper permissions to your registered application/service principal of Purview Data Source Administrator as this role can manage the scans. I have tried this with the same and it worked fine with this role.
Please refer to the documentation for role details -
Please note that the Purview Data Source Administrator role has two supported scenarios. The first scenario is for users who are already Purview Data Readers or Purview Data Curators that also need to be able to create scans. Those users need to be in two roles, at least one of Purview Data Reader or Purview Data Curator as well as being placed in the Purview Data Source Administrator Role.
The other scenario for Purview Data Source Administrator is for programmatic processes, such as service principals, that need to be able to set up and monitor scans but should not have access to any of the catalog's data.
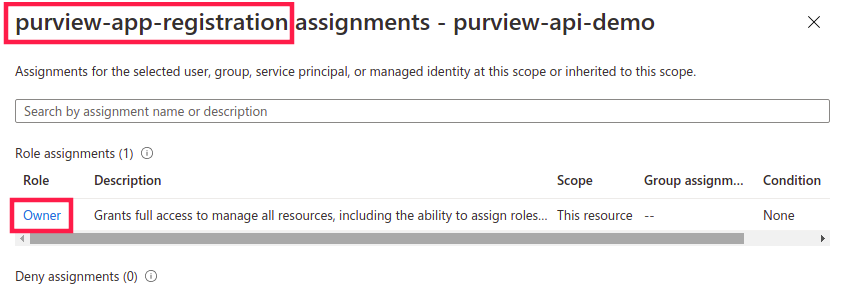
Also, I suggest you to use Azure Purview pre-defined Data plane roles like Purview Data Curator Reader, Purview Data Curator Role etc. instead of giving owner permissions to service principals.
Please let me know if you have any questions.
Thanks
Saurabh
----------
Please do not forget to "Accept the answer" wherever the information provided helps you to help others in the community.
 ]
]