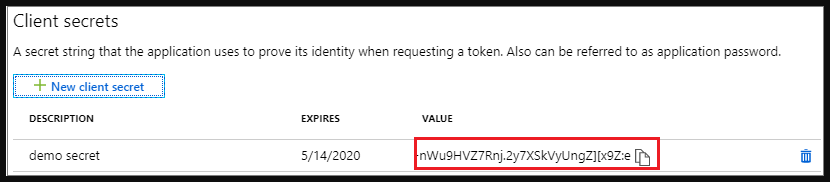
Hello,
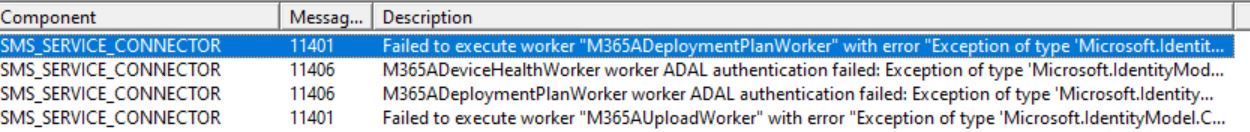
Receiving the below messages for the Service Connection Point Role.
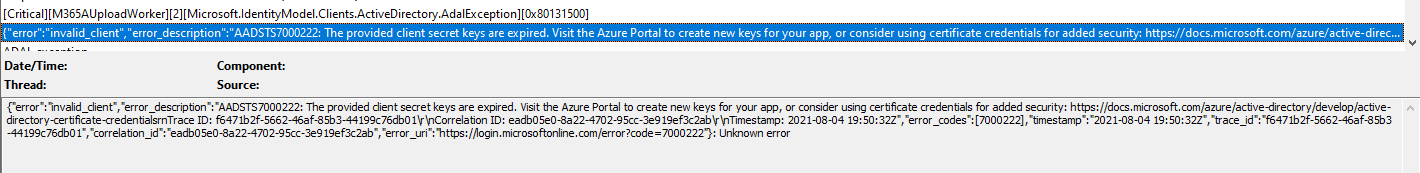
M365AUploadWorker worker ADAL authentication failed: Exception of type 'Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException' was thrown.
Failed to execute worker "M365ADeviceHealthWorker" with error "Exception of type 'Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException' was thrown.". See M365ADeviceHealthWorker.log for further details.
M365ADeviceHealthWorker worker ADAL authentication failed: Exception of type 'Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException' was thrown.
Below message appear in M365AUploadWorker.log
AADSTS7000222: The provided client secret keys are expired. Visit the Azure Portal to create new keys for your app, or consider using certificate credentials for added security: https://learn.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials
Trace ID: f6471b2f-5662-46af-85b3-44199c76db01
Correlation ID: eadb05e0-8a22-4702-95cc-3e919ef3c2ab
Timestamp: 2021-08-04 19:50:32Z
Exception details:
[Critical][M365AUploadWorker][0][Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException][0x80131500]
Timestamp: 2021-08-04 19:50:32Z at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Http.AdalHttpClient.<GetResponseAsync>d__22`1.MoveNext()
End of stack trace from previous location where exception was thrown ---
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Http.AdalHttpClient.<GetResponseAsync>d__21`1.MoveNext()
at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Flows.AcquireTokenHandlerBase.<SendHttpMessageAsync>d__72.MoveNext()
at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Flows.AcquireTokenHandlerBase.<SendTokenRequestAsync>d__69.MoveNext()
at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Flows.AcquireTokenHandlerBase.<CheckAndAcquireTokenUsingBrokerAsync>d__59.MoveNext()
at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Flows.AcquireTokenHandlerBase.<RunAsync>d__57.MoveNext()
at Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext.<AcquireTokenForClientCommonAsync>d__33.MoveNext()
at Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext.<AcquireTokenAsync>d__61.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.Utility.<GetAuthenticationResultAsync>d__49.MoveNext()
[Critical]M365AUploadWorker[System.Net.Http.HttpRequestException][0x80131500]
Response status code does not indicate success: 401 (Unauthorized).
[Critical][M365AUploadWorker][2][Microsoft.IdentityModel.Clients.ActiveDirectory.AdalException][0x80131500]
{"error":"invalid_client","error_description":"AADSTS7000222: The provided client secret keys are expired. Visit the Azure Portal to create new keys for your app, or consider using certificate credentials for added security: https://learn.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials\r\nTrace ID: f6471b2f-5662-46af-85b3-44199c76db01\r\nCorrelation ID: eadb05e0-8a22-4702-95cc-3e919ef3c2ab\r\nTimestamp: 2021-08-04 19:50:32Z","error_codes":[7000222],"timestamp":"2021-08-04 19:50:32Z","trace_id":"f6471b2f-5662-46af-85b3-44199c76db01","correlation_id":"eadb05e0-8a22-4702-95cc-3e919ef3c2ab","error_uri":"https://login.microsoftonline.com/error?code=7000222"}: Unknown error
ADAL exception
Exception of type 'Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException' was thrown. at Microsoft.IdentityModel.Clients.ActiveDirectory.Internal.Http.AdalHttpClient.<GetResponseAsync>d__22`1.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.Utility.<GetAuthenticationResultAsync>d__49.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.ServiceConnectorWorkerBase.<ApplyAuthorizationToRequestAsync>d__86.MoveNext()
Exception of type 'System.Net.Http.HttpRequestException' was thrown.
Exception of type 'Microsoft.IdentityModel.Clients.ActiveDirectory.AdalException' was thrown.
Unexpected exception for worker M365AUploadWorker
at Microsoft.ConfigurationManager.ServiceConnector.ServiceConnectorWorkerBase.<ApplyAuthorizationToRequestAsync>d__86.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.ServiceConnectorWorkerBase.<ApplyAuthorizationToRequestAsync>d__85.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.ExtensionMethods.<GetNegotiatedResponseAsync>d__9.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.AadServiceConnectorWorker.<GetLocationServiceEndpointUrlAsync>d__24.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.AadServiceConnectorWorker.<GetMicroserviceUriAsync>d__15.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.AccountOnboardingWorker.<DoOnboardScenarioAsync>d__19.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.AadServiceConnectorWorker.<DoWorkAsync>d__16.MoveNext()
at Microsoft.ConfigurationManager.ServiceConnector.ServiceConnectorWorkerBase.<ExecuteAsync>d__75.MoveNext()
Please provide the steps to troubleshoot the issue