Hello
Based on the link you provided, I did a test in my lab.
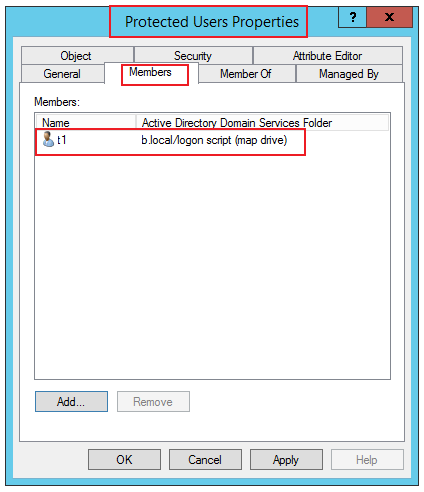
1.Add a domain user (t1) to Protected Users group.
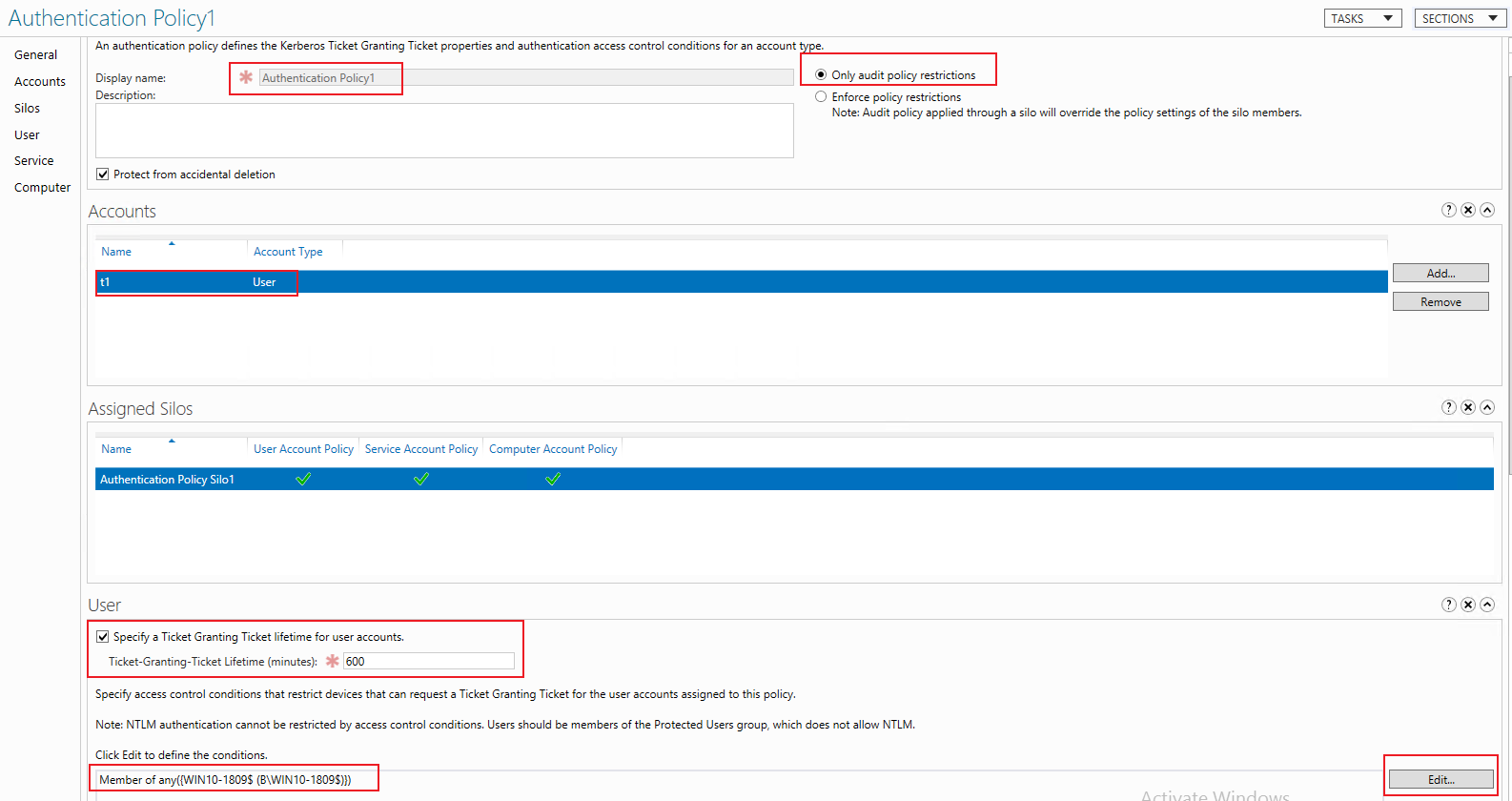
2.Create Authentication Policy.
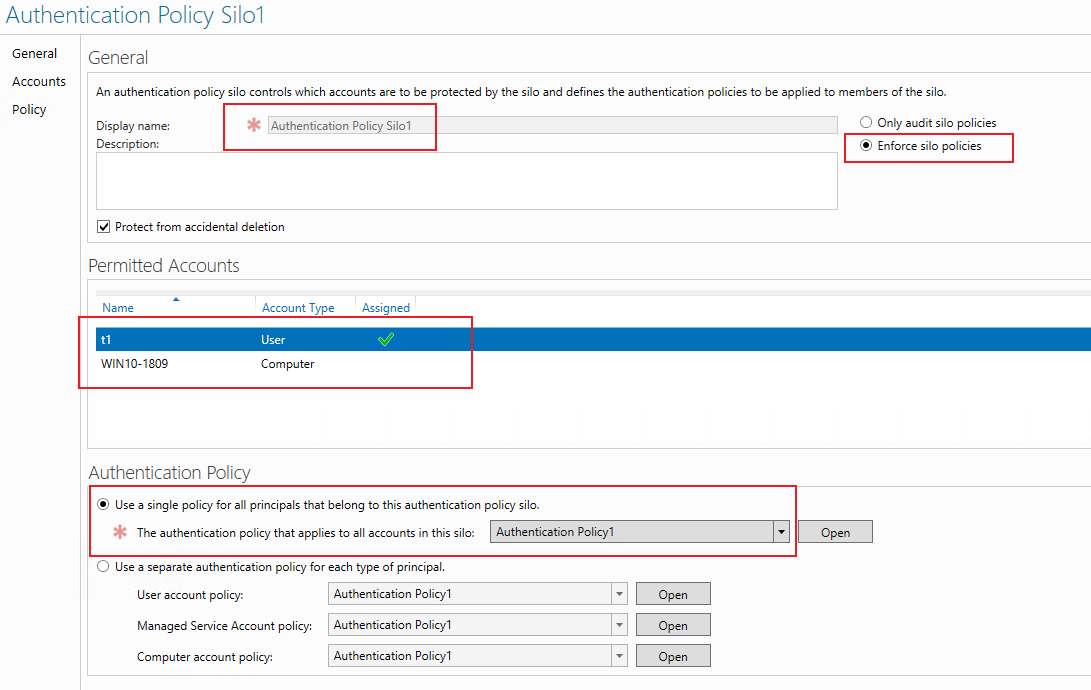
3.Create Authentication Policy Silo.
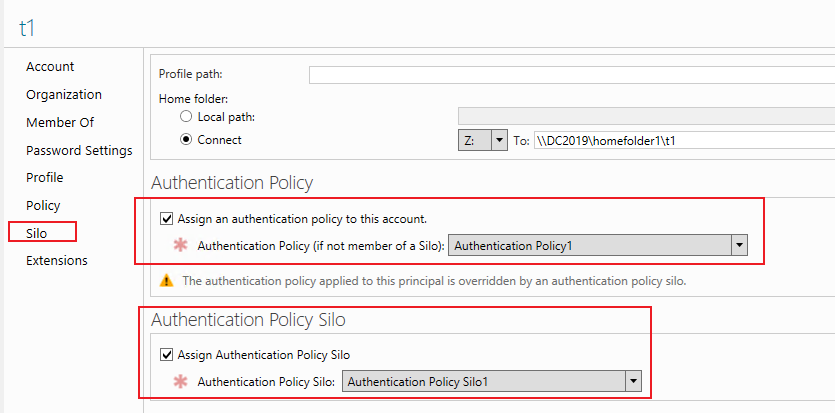
4.Bind Authentication Policy and Authentication Policy Silo to user account (t1)
5.Configure the following group policy setting (through local group policy)for Win10-1809 above.
Computer Configuration > Administrative Templates > System > Kerberos >Kerberos client support for claims, compound authentication and Kerberos armoring
6.Configure the following group policy setting through Default Domain Controller Policy object) for domain controller.
Computer Configuration > Administrative Templates > System > KDC > Key Distribution Center (KDC) client support for claims, compound authentication and Kerberos armoring
7.When I user domain account (B\t1) to logon client, I can not logon with error message.
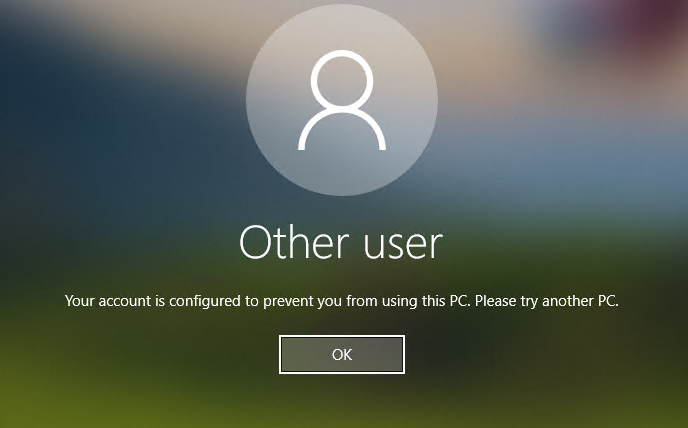
We can check if we missed some configurations or some configurations is mis configured.
For more information, we can refer to the link below.
Authentication Policies and Authentication Policy Silos
http://www.rebeladmin.com/2016/03/authentication-policies-and-authentication-policy-silos/
Best Regards,
Daisy Zhou


