Hi @JamesTran-MSFT ,
I have opened a ticket for Microsoft support and we are trying out some things.
Just to leave you with the replies to some questions:
What request do you use?
I'm using a HTTPS request with a redirect to a public exposed page. This gets the authentication token and asks for a User AAD login in case it hasn't done it yet.
The request is done in the correct format.
What redirect URI do you use when performing the request? The value used to perform the request should match the value of the redirect URI from the app registration from Azure Portal.
I'm using the following redirect https://admin.localtest.me/public/AADSignInCallback.aspx
The redirect works very well.
Please make sure you have the correct Reply address configurations as in both on the application side as well as the correct one registered in the app registration. Also, keep in mind that the address is case sensitive and this can cause some issues.
The URL is exactly the same in both the request and the App Registration->Authentication->Web Redirect URIs page.
I also get the code 200 response and then I redirect from the public page to an internal one, to continue the flow.
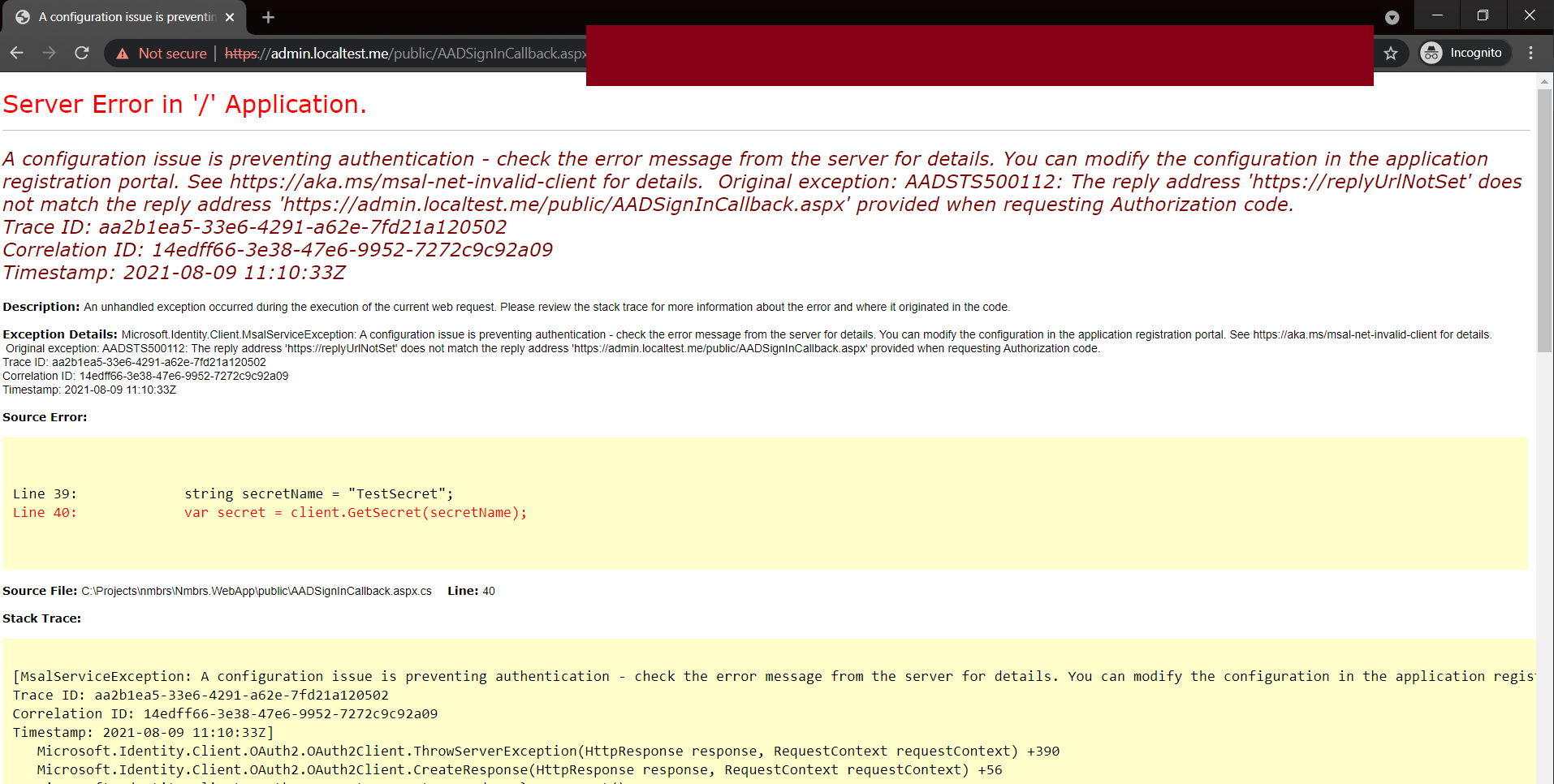
The issue is in the actual call to get the KV secret value even though the error points to URL
Original exception: AADSTS500112: The reply address 'https://replyUrlNotSet' does not match the reply address 'https://default.localtest.me/WebFormsKeyVault/SignInCallback' provided when requesting Authorization code.
I'm using the Azure.Security.KeyVault.Secrets.SecretClient.GetSecret("SecretName" request to get the secret value from a KV. (Assembly Azure.Security.KeyVault.Secrets, Version=4.2.0.0)
When we execute the GetSecret I get the error.
I have installed the Azure.Identty (version 1.5.0-beta.2) so I can specify the URL the following way:
var credentials = new AuthorizationCodeCredential(
TenantId
, ClientId
, ClientSecret
, code
, new AuthorizationCodeCredentialOptions
{
AuthorityHost = new Uri(Authority),
RedirectUri = new Uri(SignInCallback)
}
);
Where SignInCallback = "https://admin.localtest.me/public/AADSignInCallback.aspx" --> the same one that is on the App Registration
The solution to solve this was found by one of our colleagues Helder Santo, override the 'GetToken' method from AuthorizationCodeCredential Class in order to force the URI value.
And it works
var credentials = new AuthorizationCodeCredentialOverride(
TenantId
, ClientId
, ClientSecret
, code
, new AuthorizationCodeCredentialOptions // This is the new adition
{
AuthorityHost = new Uri(Authority),
RedirectUri = new Uri(AADTokenUtils.SignInCallback)
}
);
So far I'm able to get the value from the KV using this workaround.
A new issue has come along when trying to call the KV for the same client without the need for the client to re-login to AAD ?
This is to get values from the KV to fill in some parts of the application that are not on the same page as the authentication, like a Popup to change a KV value for example.