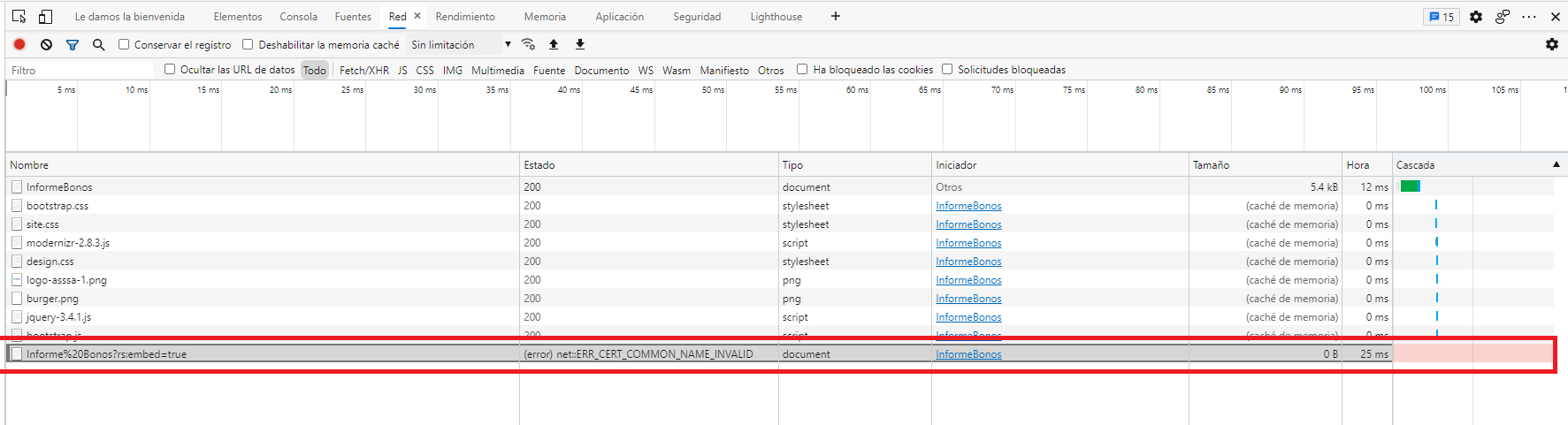
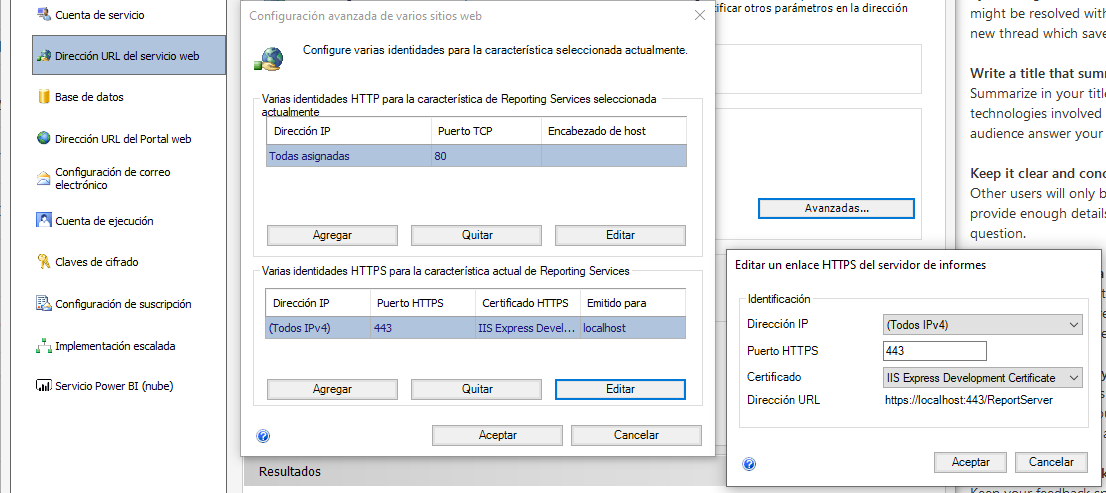
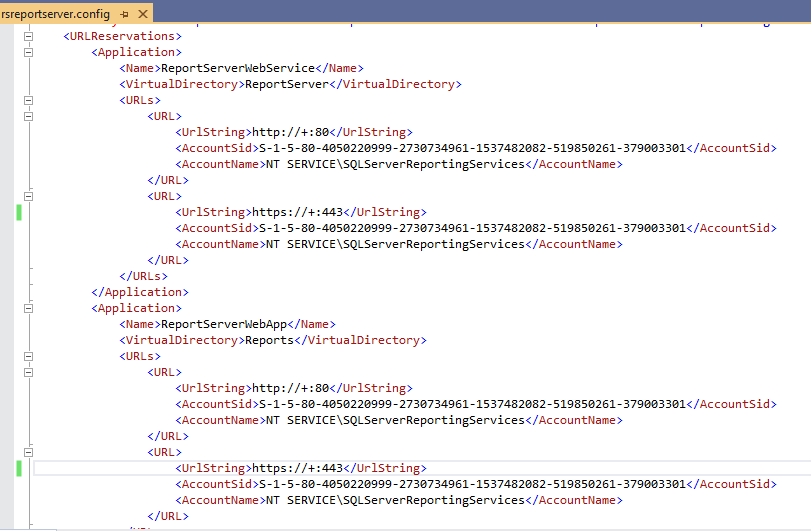
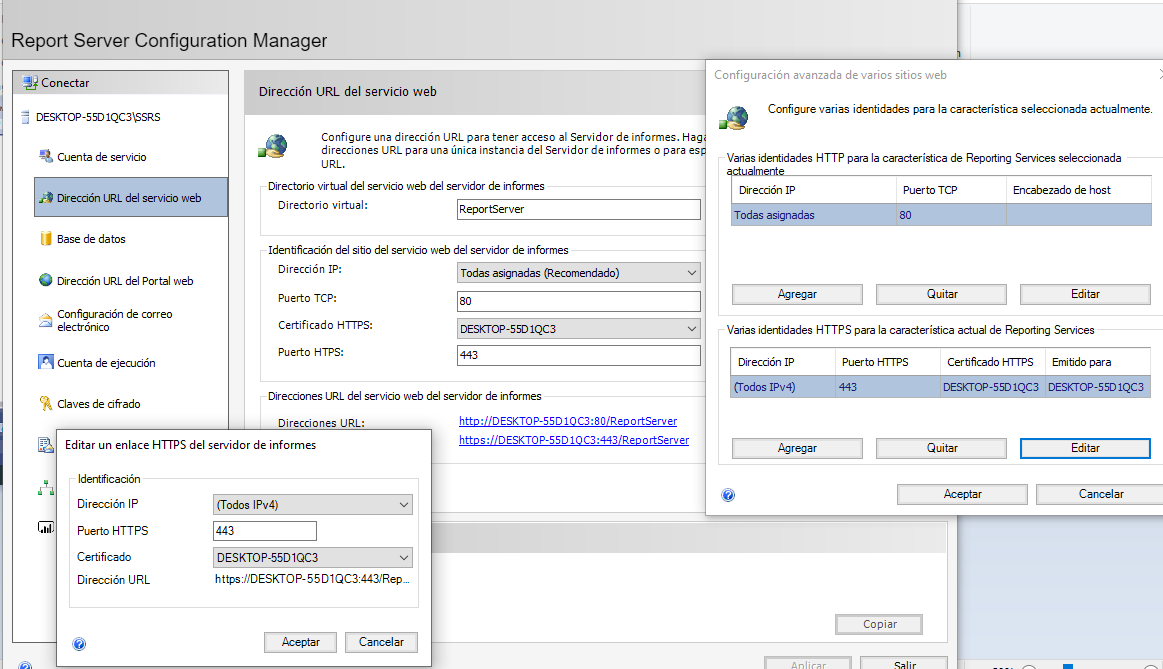
Well... a self-signed certificate is never trusted. If you want that your self-signed certificated to be trusted, you must add-it to the "Trusted Root Certification Authorities"
Follow these steps...
- Open the certlm.msc console
- Navigate to Personal / Certificates
- Select the certificate that has the same name for "issued to / issued by". Normally, the name should be your computer account
- Right click on the certificate and select All tasks / Export
- Click Next and select "No, do not export the private key" and click next
- let the default export file format and click next
- Select a folder location to export the file (it will be a .cer file)
- Click next and Finish
- Go back to the certlm.msc console and navigate to Trusted RootCertification Authorities / Certificates
- Right click on Certificates and click All Tasks / Import
- Click next and select the .cer file you have just exported
- Click next / next and finished
- Done
After that, go back to your Report Server configuration and repeat the same steps... it should work
hth