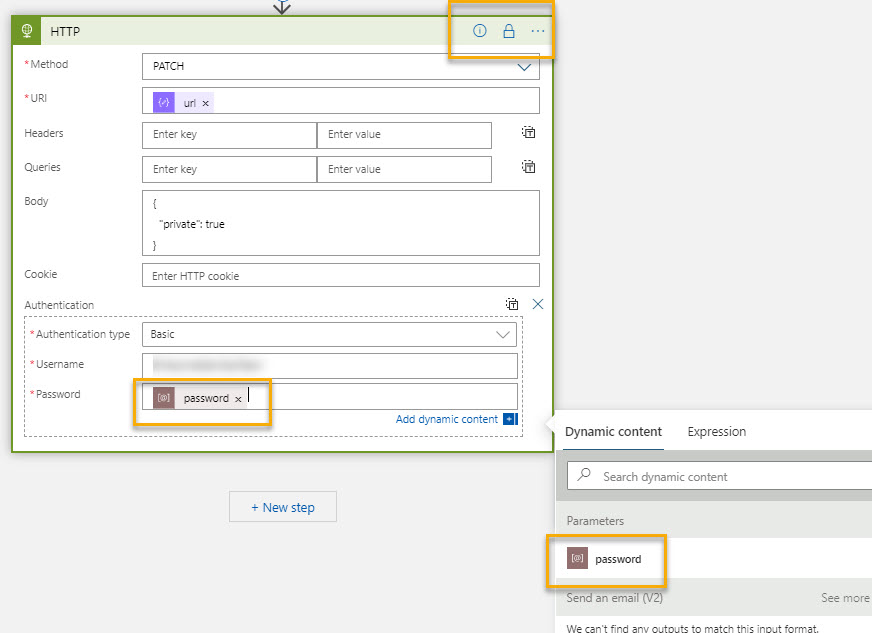
You can use obfuscation to secure the input and output in the designer: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#obfuscate
Please review the consideration when securing input and output: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#obfuscation-considerations
Access to run history data: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#secure-run-history
Updated:
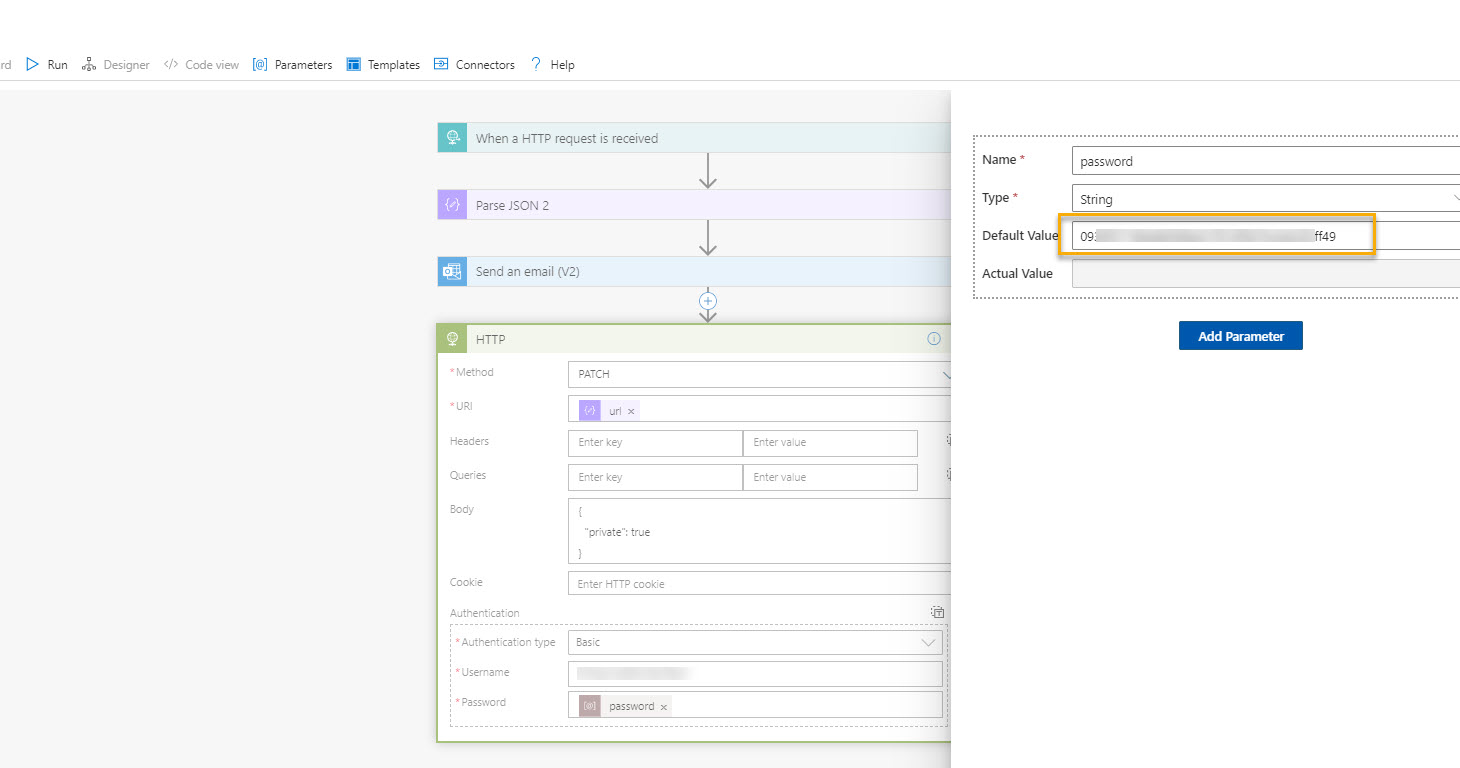
If you are creating the parameter of type string or securestring then the value will be visible in the designer and code view.
To protect passwords, keys, secrets, and other sensitive information define secured parameters at the template level and workflow definition level by using the securestring or secureobject type using ARM template. You can then store these values in the Azure Key Vault and use the parameter file to reference the key vault and secret. Your template then retrieves that information at deployment: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#secure-parameters-in-azure-resource-manager-templates
You can leverage this ARM template: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#secure-parameters-in-azure-resource-manager-templates
While deploying the ARM template it will ask you all the parameter that you have mentioned in the ARM template as below
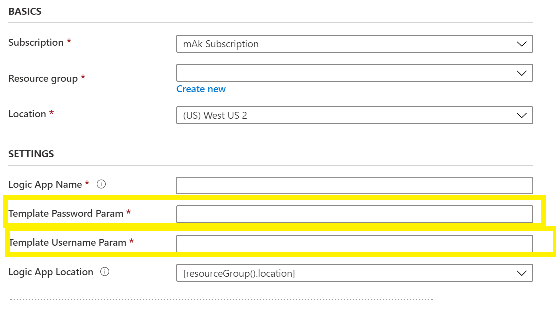
Once the deployment is completed. In the designer view, you will see two parameters are added
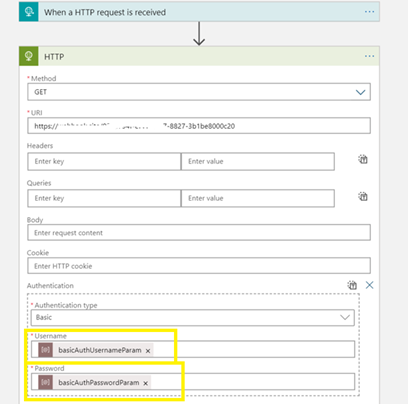
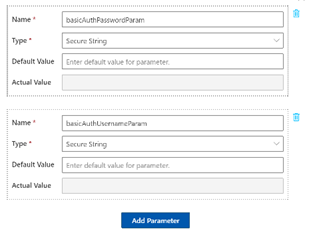
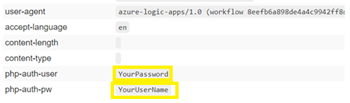
You can run the trigger and see that the username and password are passed correctly and in the code or designer view, you value not see any default value as this is set at the ARM template parameter level.
Hope the above helps.