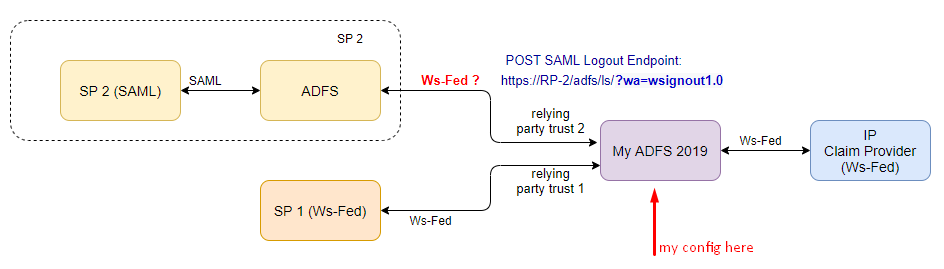
I did some test with a colleague and this is what we see:
ADFS-A <-- WS-Fed--> ADFS-B <-- SAML2 --> SP
If I sign out from the SP, it does send the signout request to the IDPs:
- https://ADFS-A/adfs/ls/?wa=wsignout1.0
- https://ADFS-B/adfs/ls/?wa=wsignout1.0
- https://ADFS-A/adfs/ls/?wa=wsignoutcleanup1.0
And if the token for the SP has a NameID issued in it, then also try to signout reaching to the SAML signout endpoint.
In my case that's:
- https://SP/signout
However, if there were no NameID issued, then we don't keep track of things and don't try to contact the SP endpoint.
And all this is assuming that the protocol used between ADFS-A and ADFS-B IS WS-Fed. By default it will not be the case between two ADFS farms if the SP is using SAML. If the SP is using SAML, the ADFS logic will be to use SAML between ADFS-A and ADFS-B. In my case I forced it to use WS-Fed between the two farm by deleted the SAML endpoints on my claim provider trust on ADFS-B.
Now the endpoint for the SP MUST be hosted and managed by the SP. Else you will not be able to perform a full sign-out in all circumstances. If you configure your relying party trust with a SAML Log Out endpoint pointing to the ADFSfarm itself, you will not be able to perform an IDP initiated signout. Nor a full log out if that is coming from another SP trusted by the IDP.