@paulocorreia Can you create the issue in azure function docker so the team can look into this further. Please share the violations scan reports when you create the issue in azure function docker repository. As per the screenshot I couldn't see more details on the vulnerabilities part on what CVEs causing this issue.
If there is an issue with CVEs mentioned in your violations report and the issue is with with underlying Debian image that is used for functions then this need to be first fixed at the Debian base image by the Debian team. Once the issue is fixed by them then we can fixed the same at our end with the base image used.
For vulnerabilities caused due to our end or the Debian has already fixed it in their base image then the function docker team can help in fixing it.
There are many reasons for CVEs to still be shown in production images at Debian end and you can read this for information: https://github.com/docker-library/faq#why-does-my-security-scanner-show-that-an-image-has-cves
If any CVEs that you think might affect you. You can track them using this link: https://security-tracker.debian.org/tracker/
Further, you can raise the issue with Debian for specific CVEs that are related to debian base image.
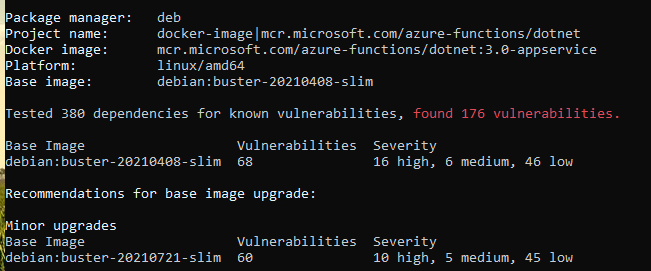
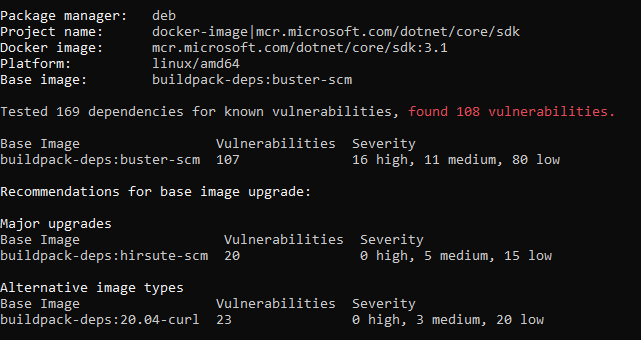
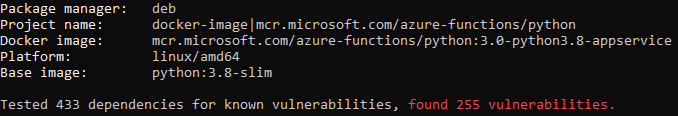
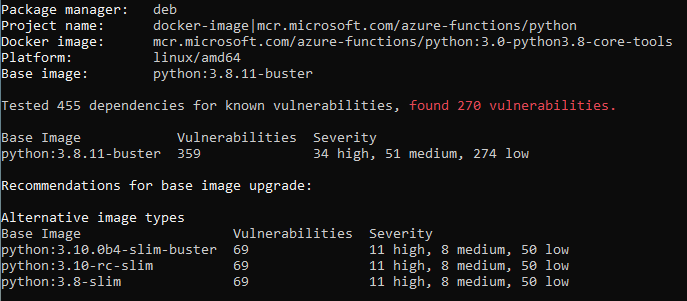 Alternatives are to... compile almost everything from source, as you might guess, for the customer that's not acceptable.
Alternatives are to... compile almost everything from source, as you might guess, for the customer that's not acceptable.