I'm not exactly sure what your question is, but take a look at this post.
Scroll down to the bottom and look at the Powershell script that I modified. It shows the listeners, process names, and the service name if one exists.
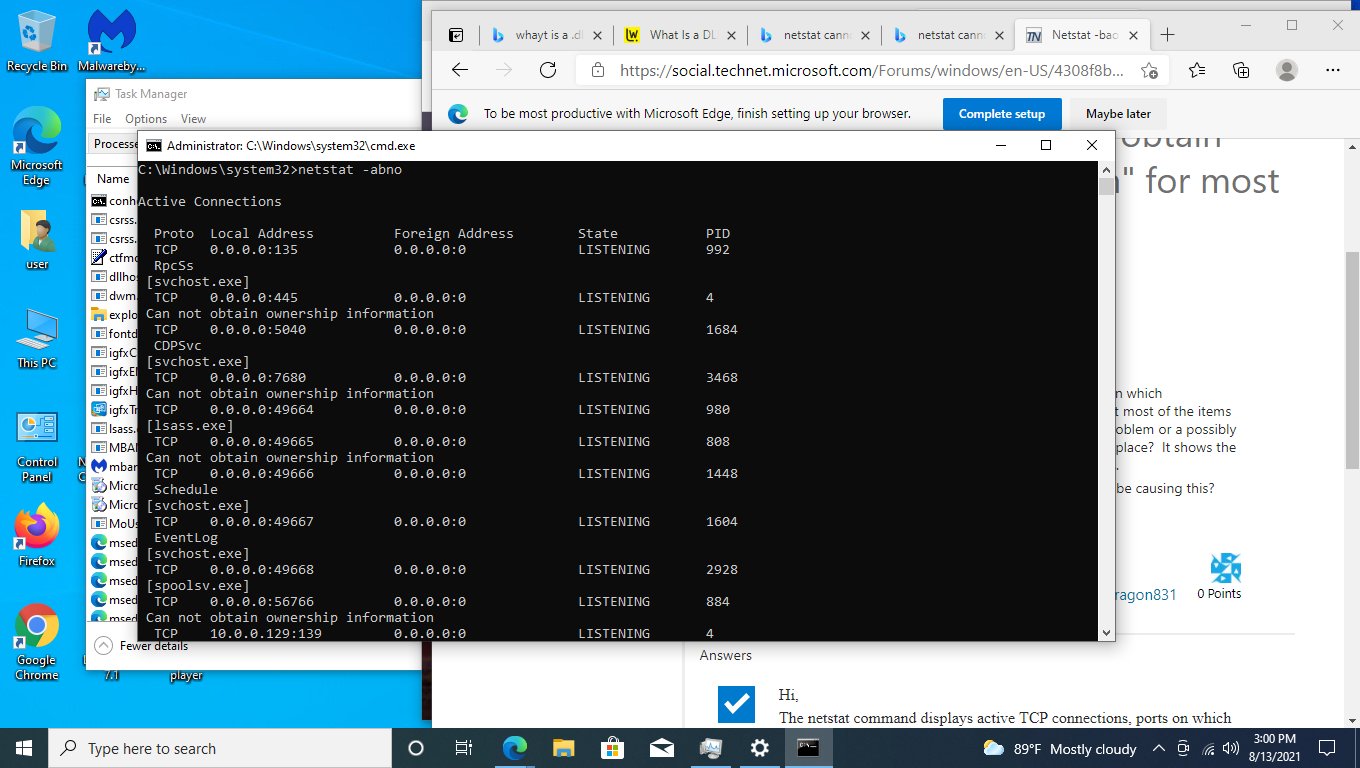
As I noted, port 80 shows up as "system PID 4". On my PC that is really IIS and I wanted to see if I could find more info about the "system listeners". I found that netsh would show that info.
netsh.exe http show servicestate view=requestq
I started hacking around to see if I could parse that output and possible incorporate it into the ShowListeners.ps1 script. I just left it as a second script. This may show you some of the "ownership information".
This is "work in progress" script.
# Script: ShowSystemListeners.ps1
# Author: MotoX80
cls
$r = (netsh.exe http show servicestate view=requestq) -join "" # make it one long string
$r = $r -replace " Request queue name", "============" # we only want these that are not indented
$ra = $r -split "Request queue name: " # create an array of each entry to be processed
$idx = 1 # skip over header
while ($idx -lt $ra.count) {
$tf = $ra[$idx] -match '(Process IDs:).*(URL groups:)'
if ($tf) {
#$matches[0] # uncomment to see what we found.
} else {
#"No pids???" # we didn't find the headings. not sure what kind of entry this is.
$idx++ # go to next entry
continue
}
$ids = $matches[0].split(" ") # get pids, but we only process the first one. I have not seen 2 pids on my machine
$p = ($ids -match "^\d+$")[0]
if ($p -eq $null) {
#"No pids2???"
$tf = $ra[$idx] -match '(Controller process ID:).*(Process IDs:)'
if ($tf) {
#$matches[0] # uncomment to see what we found.
} else {
#"No pids???" # we didn't find the headings. not sure what kind of entry this is.
$idx++ # go to next entry
continue
}
$ids = $matches[0].split(" ") # get pids
$p = ($ids -match "^\d+$")[0] # our pid
#$idx++ # I think that each listener must have a controlling pid
#break
#continue
}
"======================== $idx ======================================================================="
$tf = $ra[$idx] -match '(Registered URLs:).*(Server session)'
if ($tf) {
#$matches[0]
} else {
"No HTTP addresses???"
#$ra[$idx]
$idx++
#continue
}
$http = $matches[0].split(" ")
$http -match ':/'
""
"Process ID: $p"
$s = Get-CimInstance win32_service -FIlter "ProcessId=$p"
""
(Get-Process -Id $p -IncludeUserName| Format-List -Property Path, company, Description, Username | Out-String).trim()
"ComandLine : {0}" -f (Get-CimInstance win32_process -FIlter "ProcessId=$p").Commandline
""
if ($s) {
(Get-Service -Name $s.name | Format-Table -AutoSize | Out-String).trim()
""
}
$idx++
}