I ended up resolved the issue with Azure support. It ended up being a doc defect on our end as our document was pointing to the incorrect login URL. After we followed the correct one from the Azure doc the error cleared and I was able to successfully use SSO on Intersight with Azure as the IDP
Single Sign On Not Working with Cisco Intersight
I have been trying to setup SSO in Azure with Cisco Intersight. I have been following the steps provided using the two guides below but not sure what I'm missing and getting "Invalid Request" "Cannot create a web session. Failed to validate SAML assertion. Please contact your IdP administrator"
Steps taken for configuration:
-Create Cisco Intersight application in Azure
-Upload the Intersight metadata file from Intersight
-Changed the Required claim to user.mail with "Email address" as the Name Identifier format and user.mail as the source attribute
-Downloaded the Federation Metadata XML file and uploaded it to Intersight and matching domain name as my domain in Azure
-Created second user with Azure IDP and gave the account admin permission
The only thing that I can think of is that I'm using the Azure trial version and unable to create Groups for the application in Azure. However I should still be able to login using any single account from Azure.
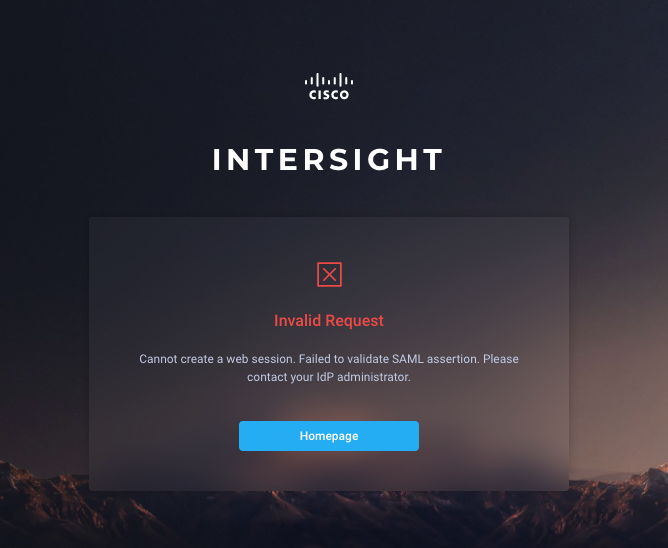 Using Chrome SAML-tracer I can see the error:
Using Chrome SAML-tracer I can see the error:
"https://www.intersight.com/uistatic/api/scope/an-error?reason=iam_saml_assertion_error&reasonType=InvalidRequest&isUserLoggedIn=false&__oc_Retry=0 HTTP/1.1"
Any suggestions or workarounds would be greatly appreciated. :)
3 additional answers
Sort by: Most helpful
-
Shashi Shailaj 7,581 Reputation points Microsoft Employee
2021-08-21T19:34:00.21+00:00 @Eddie Caballero ,
I do not think it has anything to do with the Azure Trial subscription . The trial version of azure suscription is fully functional for 30 days. I followed the following steps and got it working in my case.- Create Cisco Intersight application in Azure AD.
- Download the SP metadata from the Intersight console . Settings > authentication > Single sign on > Download SP Metadata.
- Use this metadata file to upload on the Cisco intersight enterprise app on Azure AD side.
- Changed the Required claim to user.mail with "Email address" as the Name Identifier format and user.mail as the source attribute on Azure AD side.
- Once done, download the Federation Metadata for the Cisco Intersight from Azure AD from Single sign on blade.
-
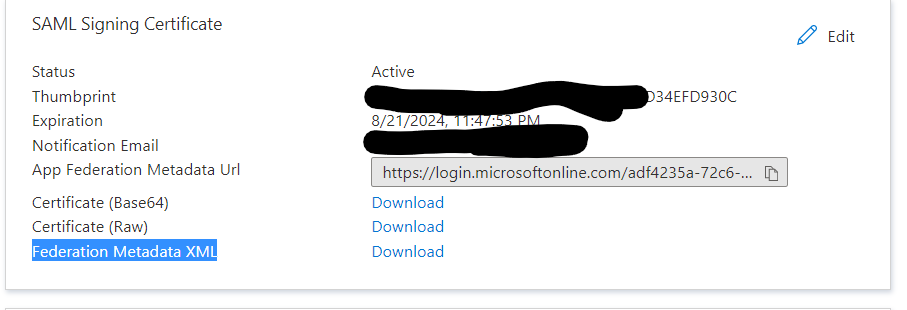
- Now go back to Cisco intersight console and go to Settings > authentication > Single sign on > Add Identity Provider and Add Azure AD as an identity provider. I used the legacy domain name in my case [AADTenant].onmicrosoft.com rather than a proper publicly routed domain . I think this should not cause any issue but I would like you to test this setup if you can since it worked for me .
-
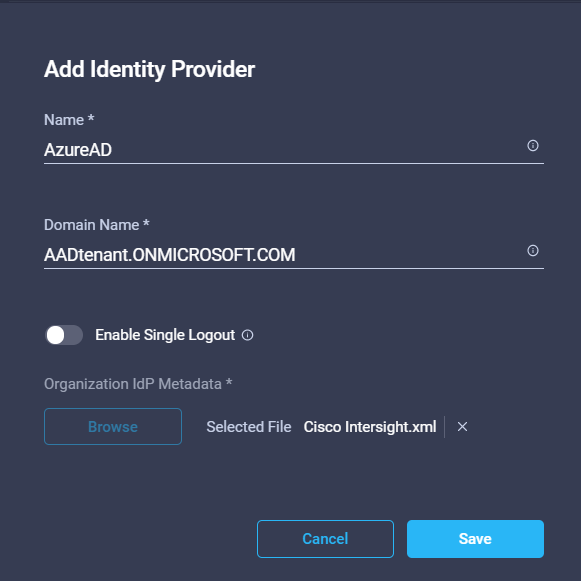
- Now add the user from your Azure AD tenant to the intersight console by going to Settings > Access & Permissions > Users > Add User . Use the same Azure AD tenant domain same as what you had mentioned while Adding the IdP in above step .
-
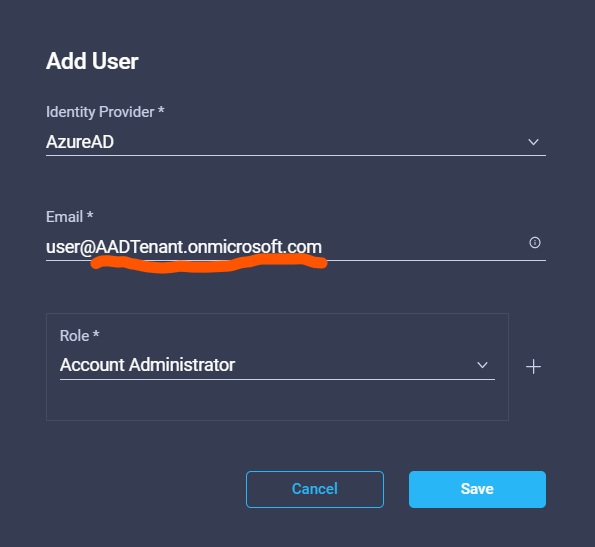
- You would like to have a Account administrator role in cisco intersight so that they can SSO as needed.
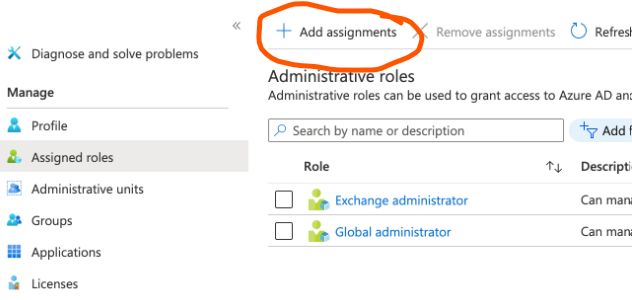
- As a last step make sure that this user is assigned the cisco intersight application via Azure AD > Enterprise Application > Cisco Intersight > Users and Groups > Add User/Group .
- Test the single-signon from the Azure AD SSO page . It should work without any issue.
-
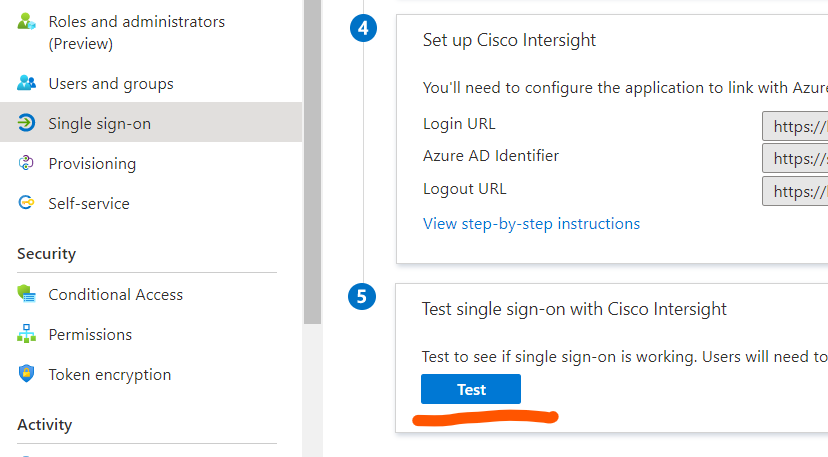
I have followed the above steps and I was able to get it working . Could you please try downloading the Intersight SP metadata and uploading it in the cisco intersight application configuration on azure Side ? The only one extra step that I completed was that I assigned the second user to the Intersight application by adding them to Azure AD > enterprise Applications > Cisco Intersight > Users and Groups > Add user . I would suggest you to repeat the process and assign the application to the second user (which you will make account administrator on cisco intersight side) as well on Azure AD enterprise app configuration of Cisco Intersight .
Hope this helps in fixing the error. In case the information provided is helpful , please do accept the post as answer so that the discoverability of this question improves for other members with similar queries in the community. In case this still does not help , please do let us know the detailed error and we will continue to help you further.
Thank you.
-
Eddie Caballero 96 Reputation points
2021-08-21T21:19:54.017+00:00 @Shashi Shailaj thank you for your response. I tried to follow your steps which are the same as the docs but the ADTenant was the difference in yours.
I deleted the config to start from scratch and still got the same error :(
Steps that I tried:
-Create Interight application in Azure
-Upload the metadata from Intersight
-Edited the Name ID claim to Email address with user.mail as the source attribute
-Downloaded the Federation Metadata XML and uploaded to Intersight SSO IDP- My tenant name in Azure is -tenant- so to follow your steps I created the IDP similar to yours as AzureAD for IDP and Domain Name -tenant-.onmicrosoft.com and not My-tenant-.onmicrosoft.com as I had it before
-Created a user in Intersight with Account Admin access as user@-tenant-.onmicrosoft.com
-Last step was adding the user to the application in Azure with the default access type (Trial version does not allow me to create any other access type for this user)
-However user is a Global and Exchange Administrator, I also added a second userI still get the same error "Invalid Request" "Cannot create a web session. Failed to validate SAML assertion. Please contact your IDP administrator."
-When I run SAML tracer on Chrome I can see the following errors:
Are their any additional configs I need to do in Azure outside the scope of Enterprise Applications? Let me know if there is anything else that I am missing
- My tenant name in Azure is -tenant- so to follow your steps I created the IDP similar to yours as AzureAD for IDP and Domain Name -tenant-.onmicrosoft.com and not My-tenant-.onmicrosoft.com as I had it before
-
Kohlmeyer, David 1 Reputation point
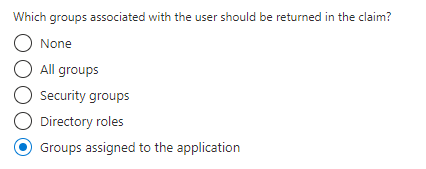
2021-09-14T18:04:34.587+00:00 I had the same error until I limited the groups returned in the claim to just the ones assigned to the application. I assume my account was a member of too many groups which hit some limit. Under 'User Attributes & Claims' modify the claim for memberOf to only returned 'Groups assigned to the application'