
The Audit object access policy handles auditing access to all objects that reside outside of AD. The first use you might think of for this policy is file and folder auditing. You can also use the policy to audit access to any type of Windows object, including registry keys, printers, and services.
Furthermore, to audit access to an object such as a crucial file, you must enable more than just this policy; you must also enable auditing for the specific objects that you want to track. To configure an object’s audit policy:
Open the object's Properties dialog box.
Select the Security tab
Click Advanced.
Select the Auditing tab as shown below
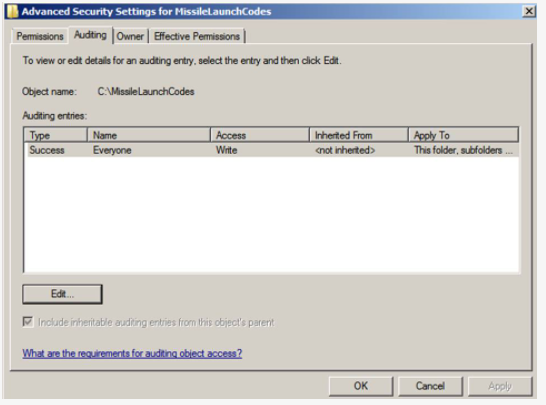
However, be warned: This policy can bog down servers. Audit only crucial objects and audit only for crucial access (e.g., Write access).
The policy has 11 subcategories:
File System
Registry
Kernel Object
SAM
Certification Services
Application Generated
Handle Manipulation
File Share
Filtering Platform Packet Drop
Filtering Platform Connection
Other Object Access Events
refer- Object Access Events
If the Answer is helpful, please click Accept Answer and up-vote, so that it can help others in the community looking for help on similar topics.

