
Yes, it can.
But you must enable some audit first on the DC's
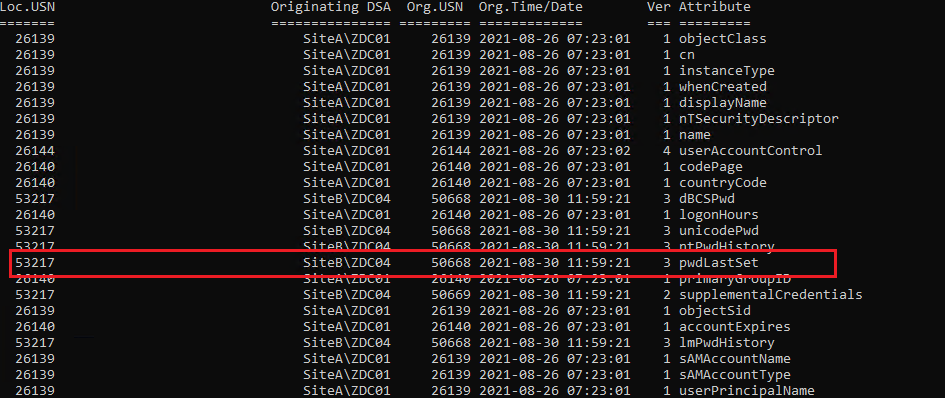
Then, if you have multiple DC's, i suggest you to use the following command to know which DC has received the password change request
repadmin /showobjmeta mydomain.local "DN"
For example, a user that has a Distinguished Name: CN=MyUser,CN=Users,=MyDomain,DC=Local
The command will be:
repadmin /showobjmeta mydomain.local "CN=MyUser,CN=Users,=MyDomain,DC=Local"
This will list you all properties of the user account and you will be able to have the DC that made the password change.
Then, open the security log on this DC and look for the Event ID 4738 "User Account Management"
You should see a list of attributes and one of them will be "Password Last Set"
hth