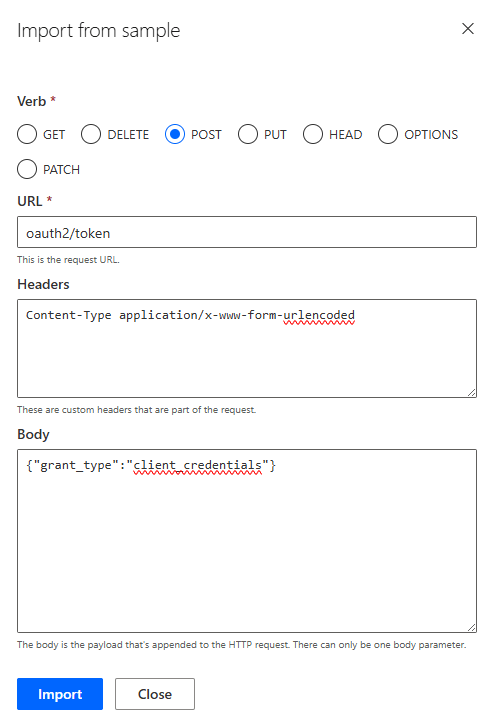
I want to create a connector to the API of an application called Maestro by Kinaxis. This API uses the following url to acquire a token "/oauth2/token". To get the token a client id and client secret are sent to this url along with the header Content-Type : application/x-www-form-urlencoded and the body {"grant_type":"client_credentials"}.
While I have been successful using this API in Python and even Power Query, I cannot find a way to set up a custom connector in Power Automate/Apps.
Here is the problem:
Every configuration I try results in need to be able to have control over the Authorization header but the custom connector setup does not give any known way to do that. Here is what I have tried:
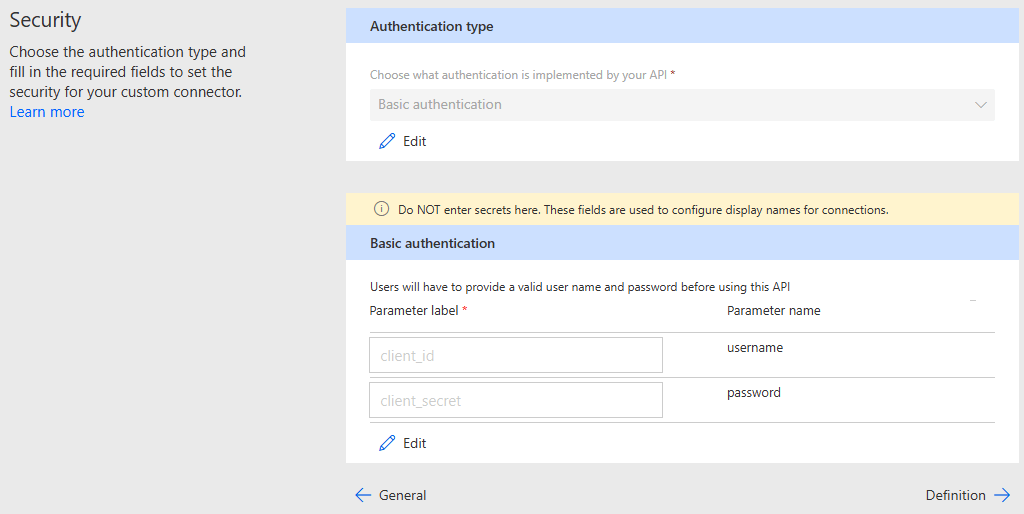
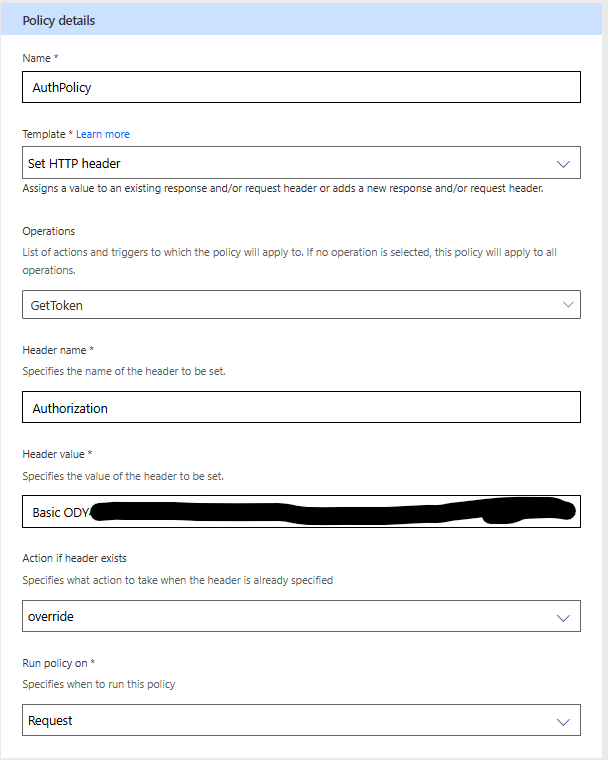
- Set security to Basic Authentication and supply the connector with the client id and secret when establishing the connection then creating a "GetToken" action to call the /token url. This fails because I believe the client id and secret are sent to the host+base url initially and then it forces itself to send a bearer token in the Authorization header of the GetToken action. I've tried to work around this by creating a Policy that overwrites the Authorization header when this action is ran. However, policy never seems to actually do anything. When I test the action the request's Authorization header was still "Bearer eyJ0eXAiO......" instead of what should have been overwritten by the policy ("Basic ODY4NmF....etc.").
- Set the security to No Authentication and create a "GetToken" action to call the /token url. I really thought this would work but I still see that in testing the request header is sent as "Authorization : Bearer ..." instead of "Authorization : Basic ...." and creating a policy to overwrite this does nothing.
- Set the security to Oauth2.0 (Generic Oauth 2). The API I am trying to use does NOT have an Authorization url. I tried putting the /token url in for Authorization url, Token url and Refresh url. The problem here is that it tries the "authorize" with the authorization url by sending the client id and client secret as a GET request when the url expects a POST request.
- Tried going back to setting the security to Basic and instead of the base url being "/TheBaseUrl" I set it as "/TheBaseUrl/oauth2/token/". The problem with this is also that it send the wrong type of request and I am also prevented from building any actions off of it since it was to prepend any action url with whats in the base url.
- Tried importing from Postman. While it worked in Postman and I was able to make a successful subsequent call beyond just getting the token, as soon as I imported it into the custom connector, it was rife with errors and things that the custom connector UI would not allow.
After all of this I have one major question that I cannot find an answer to in any of the documentation. That questions is, Does creating a "Set HTTP Header" Policy allow you to set the Authorization header?
I believe my #1 above is the closest I've gotten to the correct solution. Here are a few screenshots of the set up and the resulting request/response of testing a GetToken action:
Security Settings:
My GetToken Action:
My Policy to override the Authorization header:
The tested GetToken request:
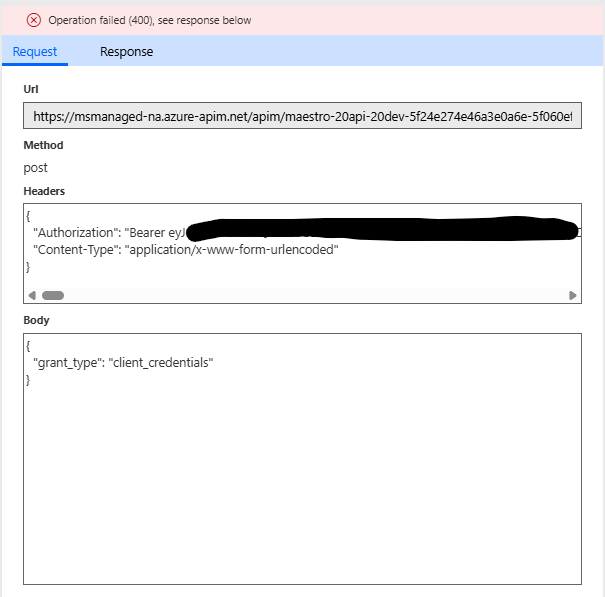
The tested GetToken response:
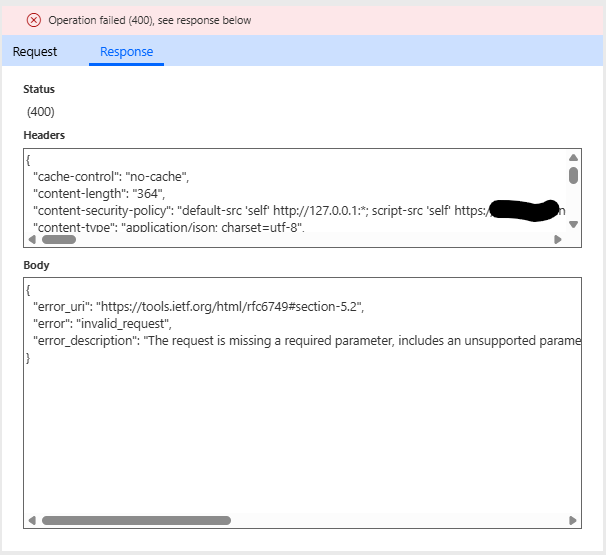
Here is the full text of the Response body:
{ "error_uri": "https://tools.ietf.org/html/rfc6749#section-5.2", "error": "invalid_request", "error_description": "The request is missing a required parameter, includes an unsupported parameter value (other than grant type), repeats a parameter, includes multiple credentials, utilizes more than one mechanism for authenticating the client, or is otherwise malformed." }
