I have been doing some research into security permissions in Active Directory, and I’ve been using a tool called AD ACL Scanner: https://github.com/canix1/ADACLScanner/releases/tag/6.2
I’m not sure if this is a tool you have used previously in security reviews, but it basically has a number of options & filters before you run a scan. One of which is to ‘exclude all built-in security principals’ (which I enabled before executing a scan of our domain). Secondly you can ‘filter by severity’, which I have done, to just flag up the critical issues.
One thing it’s flagged as a ‘critical’ risk is a group which doesn’t appear to be a Microsoft/AD default, has full control over the domain. It lists two entries in the HTML report it generates, one applies to ‘This object and all child objects’, and another applies to ‘computer’. Another entry of strange members also is listed as a critical vulnerability, has full control, which applies to ‘user’.
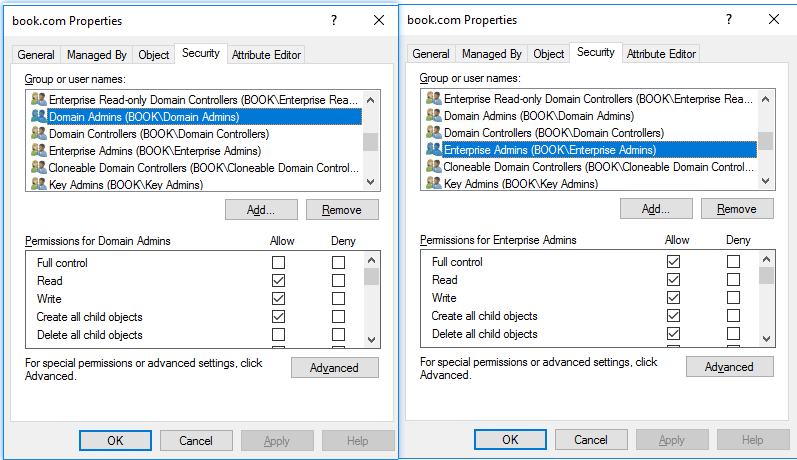
I’ve verified the results in AD users and computers, I’ve right clicked on the root of the domain > properties > security and it does have a tick in full control for this strange group, in the allow column, as well as a tick in every other permission in the list in the allow column.
It’s even more confusing as if you click the domain admins group in the ACL for the root of the domain, even that does not have full control. Enterprise admins does however.
My concern is this group with full control over the domain has actual user accounts in it, who do work in ICT, but not at a senior level enough to warrant domain admin type access. e.g. they aren't also members of the domain admins group. With what I have described above, does this sound like an oversight in the security design of our AD?
With full control (even if they are not a direct member of domain admins), what kind of problems could these users cause? Can you provide some examples?