Hello Gregg-3132,
Thank you for posting here.
So the app1 and app2 have the same numerous audit failures for unknown usernames, is that right?
We can configure audit policy on DC and servers.
GPO: Default Domain Policy
Legacy audit policy:
Computer Configuration\Windows settings\security settings\local policies\audit policy
On DC
Audit Account Logon Events – Failure
Audit Account Management - Success and Failure
On server
Audit Logon Events – Failure
Or use advanced audit policies (advanced audit policies will overwrite traditional audit policies by default):
Computer Configuration\Windows settings\security settings\Advanced Audit Policy Configuration
On server
Logon/Logoff:
Audit Account Lockout – Failure
Audit Logon – Failure
On DC
Account Logon:
Audit Kerberos Authentication Service - Failure
Audit Credential Validation – Failure
Account Management:
Audit User Account Management – Success and Failure
We can run the following commands on the domain controller to force the refresh policy and check whether the related audit policy settings are enabled:
gpupdate /force
auditpol /get /category:*
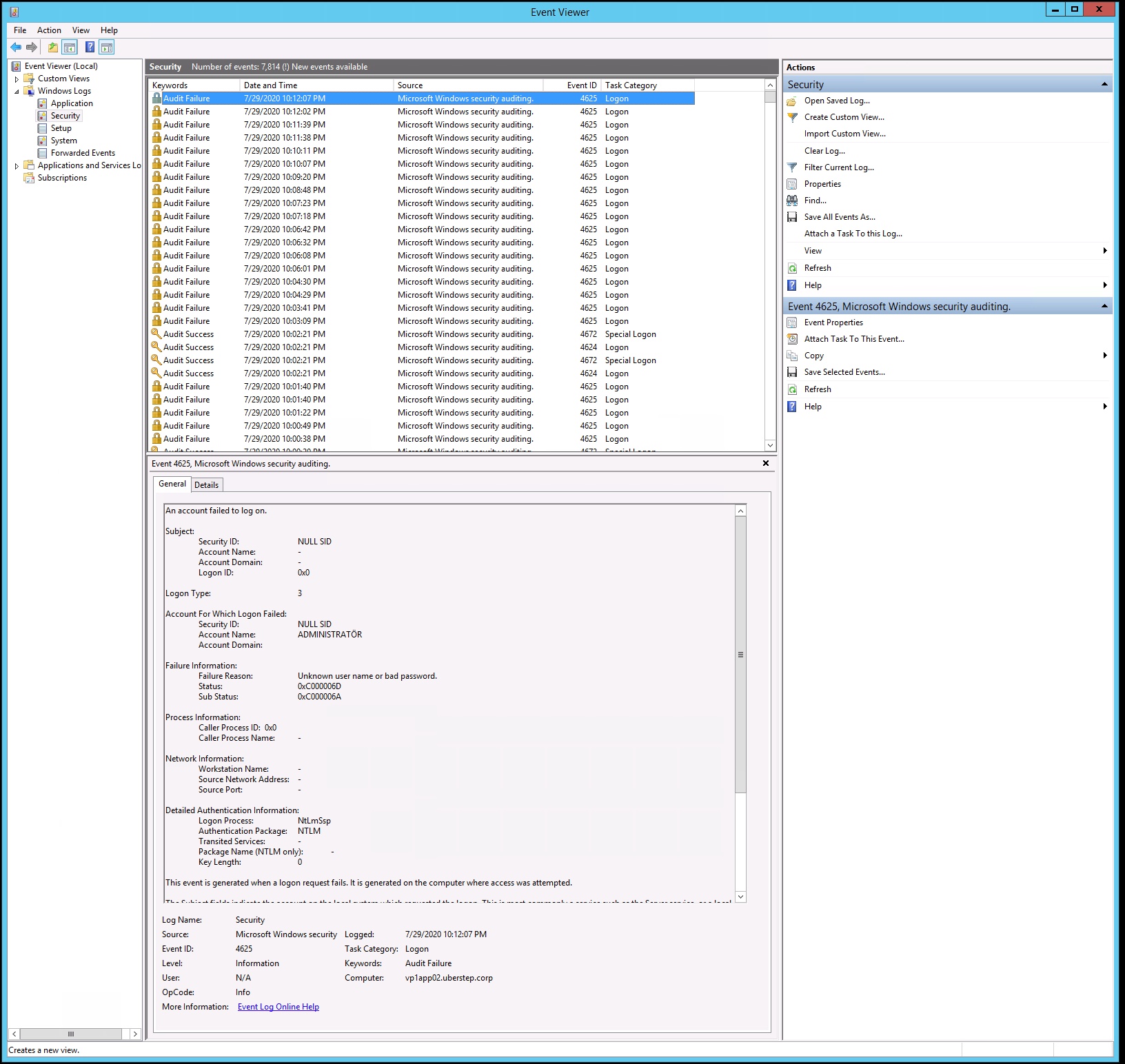
If the Event ID 4625 reoccurs, we can check if there is Event ID 4776 (NTLM authentication) or Event ID 4771 (Kerberos authentication) on DC.
Meanwhile, I can see logon type is 3 above, it is network login. The most common is to access network shared folders or printers. IIS certification is also Type 3.
We can try to capture the netmon to see if there is any network access related to \servername\sharedfoldername in log.
About how to capture network monitor traffic:
1.Choose the version for your system to download, install it as typical: https://www.microsoft.com/en-US/download/details.aspx?id=4865
2.Run Network Monitor as administrator.
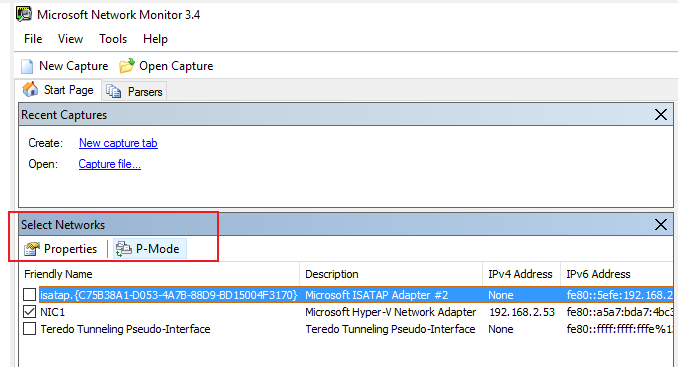
3.In the bottom left-hand, choose the NIC or NICs you want to capture.
4.Run command: ipconfig /flushdns to clean DNS cache, and nbtstat -RR to clean NETBIOS cache. Run klist purge command.
5.Then start capture when the issue reoccurs. After the necessary information is collected, click Stop.
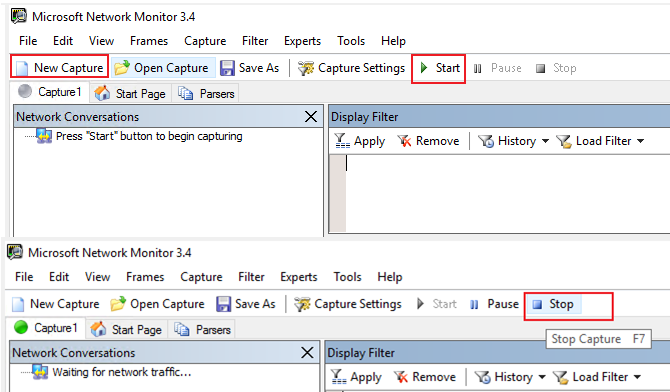
6.Save the captured files.
Best Regards,
Daisy Zhou