Hi @WindowsGeek ,
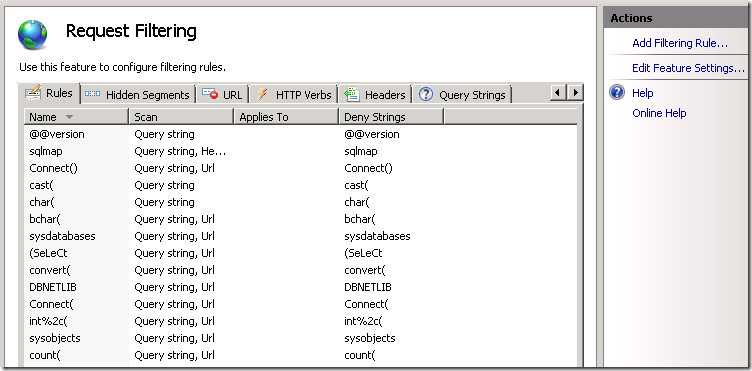
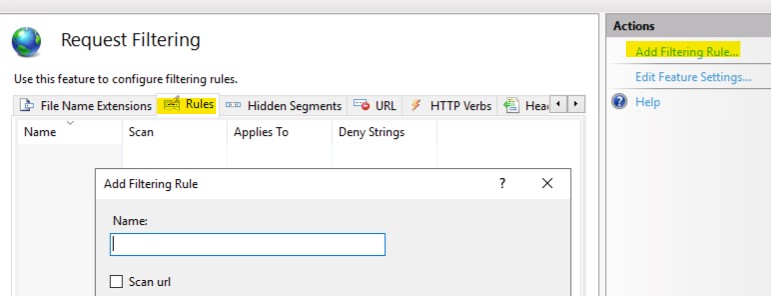
You can manually add rules in IIS Manager according to the rules on the image.
- Click Rule section in Request Filtering module.
- Click Add Filtering Rule... on the right.
- Enter rule like below image:
-
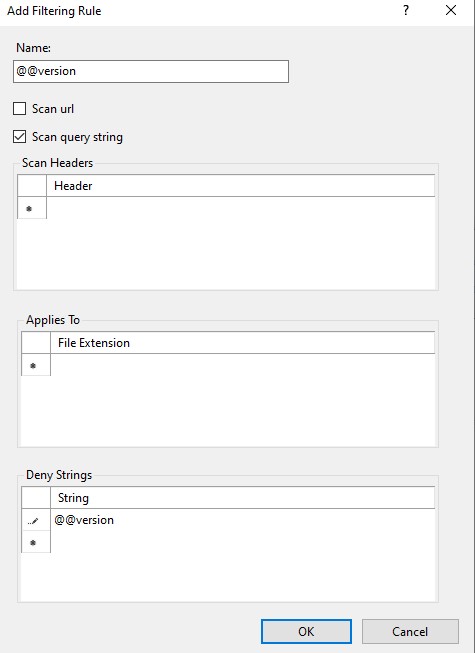
However, the rules on the image are incomplete, you may miss some part of them. In Microsoft document, it has shown a complete list of filters to prevent SQL injection. The list is not the same as the one in the image, but it is just as effective. You can copy it to web.config or applicationhost.config file.
<requestFiltering>
<filteringRules>
<filteringRule name="SQLInjection" scanUrl="false" scanQueryString="true">
<appliesTo>
<clear />
<add fileExtension=".asp" />
<add fileExtension=".aspx" />
<add fileExtension=".php" />
</appliesTo>
<denyStrings>
<clear />
<add string="--" />
<add string=";" />
<add string="/*" />
<add string="@" />
<add string="char" />
<add string="alter" />
<add string="begin" />
<add string="cast" />
<add string="create" />
<add string="cursor" />
<add string="declare" />
<add string="delete" />
<add string="drop" />
<add string="end" />
<add string="exec" />
<add string="fetch" />
<add string="insert" />
<add string="kill" />
<add string="open" />
<add string="select" />
<add string="sys" />
<add string="table" />
<add string="update" />
</denyStrings>
<scanHeaders>
<clear />
</scanHeaders>
</filteringRule>
</filteringRules>
</requestFiltering>
If the answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
Best regards,
Bruce Zhang