This web site .....
...says ....
-Credentials
Credentials of the user to connect with. Either specify a PSCredential object or a string. In case of a string value a lookup will be done to the Generic Credentials section of the Windows Credentials in the Windows Credential Manager for the correct credentials.
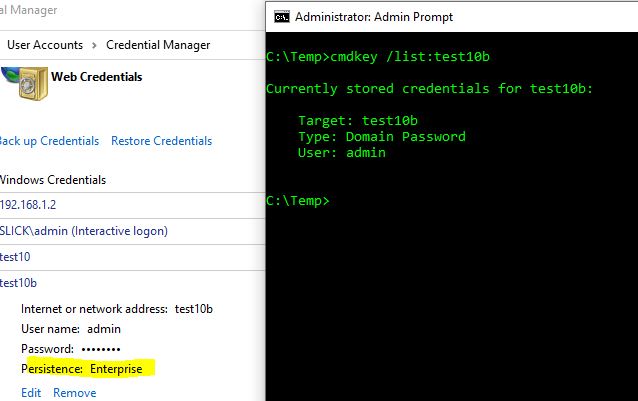
Cmdkey.exe will list available credentials. Add these commands to your PS script and review the txt file to verify that your script is running as the account that you expect and view the available credentials.
cmdkey.exe /list | out-file C:\temp\ProxyCreds.txt
whoami.exe | out-file C:\temp\ProxyCreds.txt -append
Cmdkey shows some of my credentials as "Saved for this logon only" while others show "Local machine persistence". You may have a "this logon only" problem.
I don't know how you created those credentials, but I see that the New-StoredCredential Powershell cmdlet has a -Persist switch. Maybe try that.
New-StoredCredential -Target Test -UserName test -Password test -Comment "test" -Persist LocalMachine