Hi Sina Salam and Vemula Srisai,
BTW, for my AI advisor I use ChatGPT because CoPilot is not yet answering questions with the specificity required.
My understanding is the 'managed identities' are the preferred way to assign roles in IAM RBAC to resources. ChatGPT advises...
QUOTE
When you should use a Managed Identity
- The resource (e.g., App Service, Function, VM) runs inside Azure.
- It needs to access another Azure resource (like Key Vault, Storage, SQL, etc.).
- You want no credentials in code — Azure handles tokens automatically.
- Both provider and subscriber resources are within the same Azure Tenant.
ENDQUOTE
That specifically describes my case so I am using managed identities (please see first attached screenshot).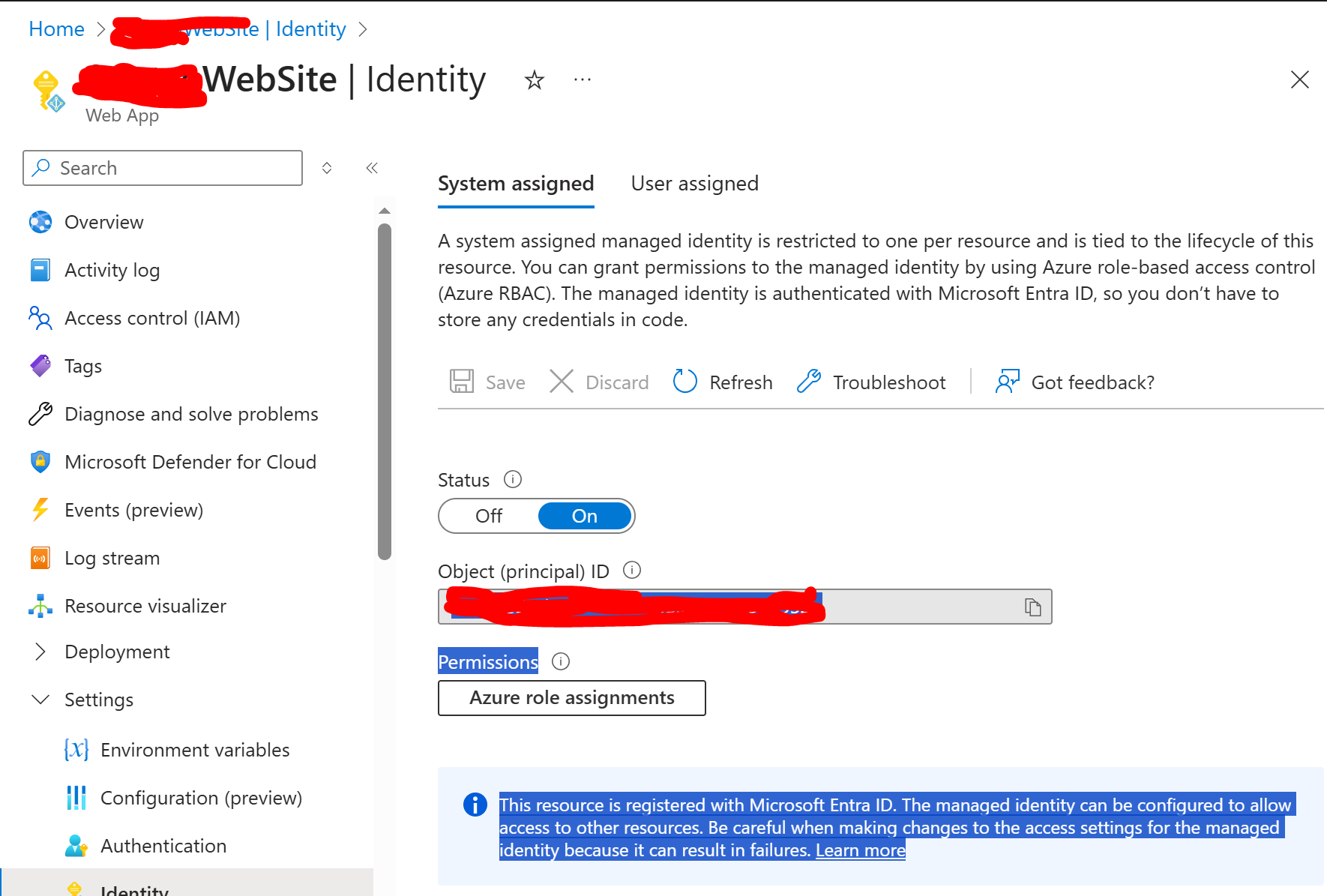
Also, please note that I am definitely trying to import RSA256 (2048-bit) SSL Certs. They work when uploaded directly from my filesystem into my Web App. The RSA256 (2048-bit) SSL Cert does NOT load from my Key Vault.
The second screenshot shows that my Web App HAS both the Key Vault Certificates User and Key Vault Secrets User (just in case, will prune later once this is sorted). (See attached 2nd screenshot)
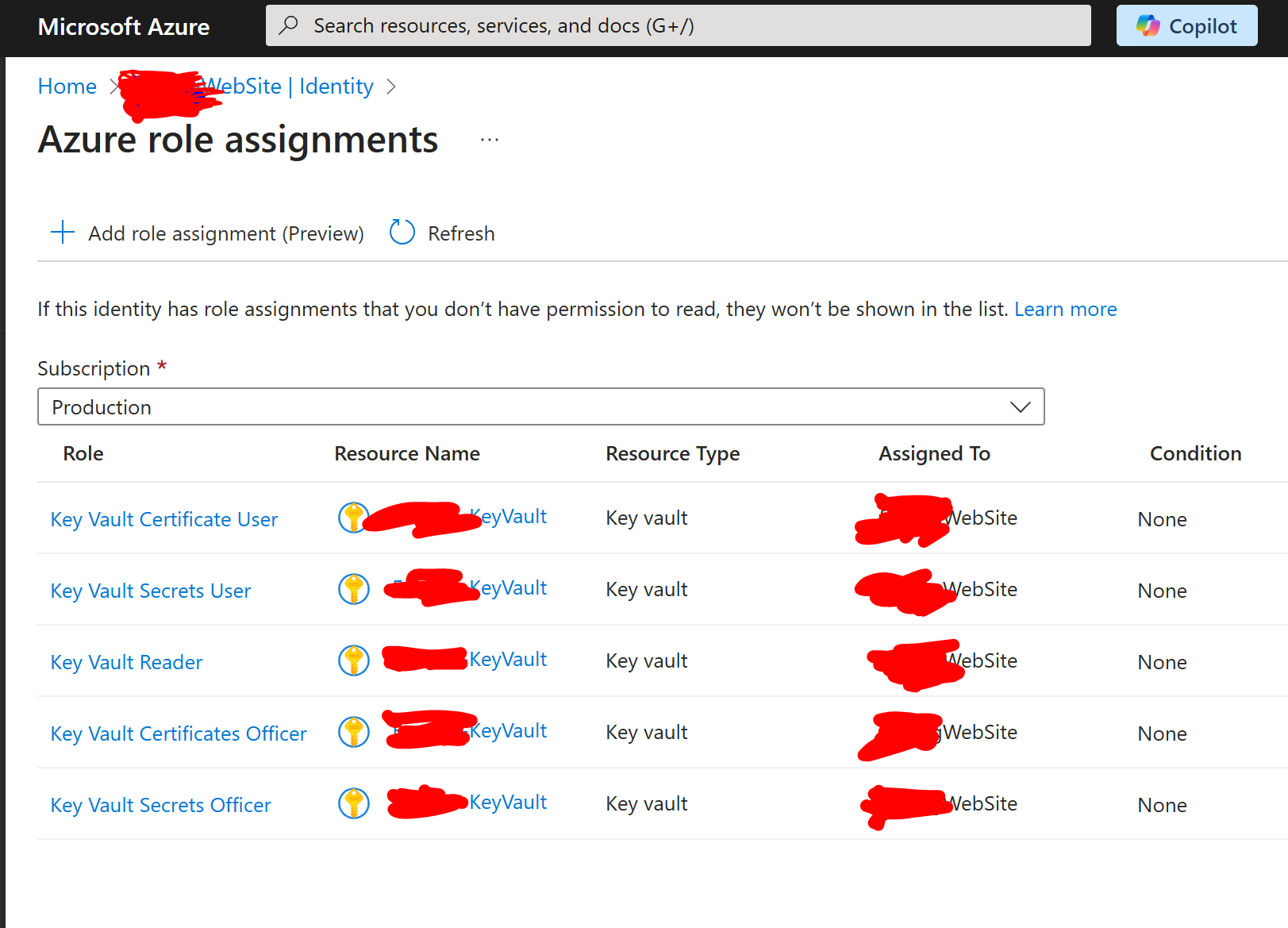
Assuming you are correct and I am misunderstanding you, what in the above recounting am I misunderstanding please?
Thanks,
Richard Freytag