Sir,
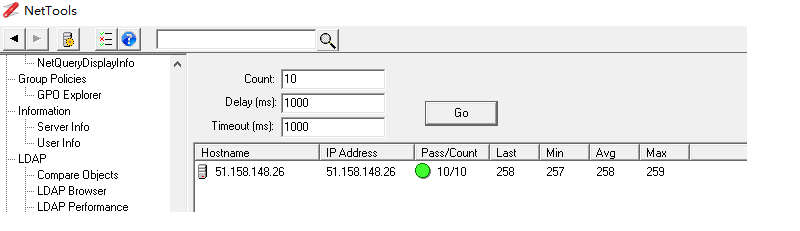
A hosting produce - C2338 CPU with Intel I120 network adpater installed Windows 2019. When I ping it from Internet with default 32 bytes, it is okay. But time out when using 85 or more bytes. How to find out why package was dropped?
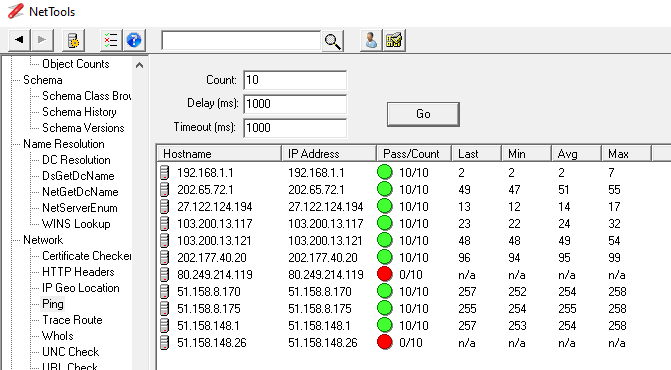
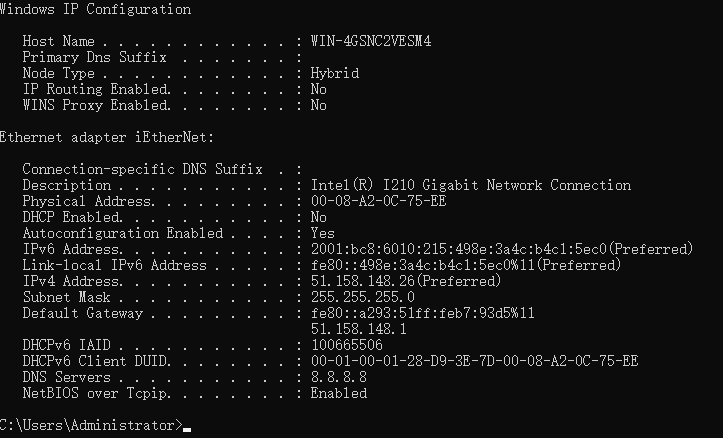
Pinging 51.158.148.26 with 32 bytes of data:
Reply from 51.158.148.26: bytes=32 time=283ms TTL=114
Reply from 51.158.148.26: bytes=32 time=284ms TTL=114
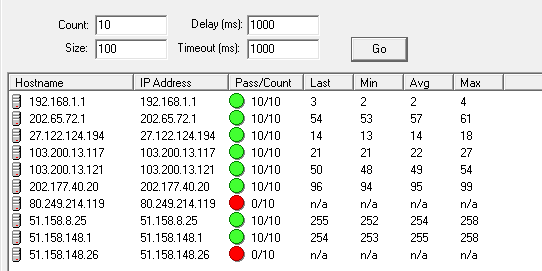
But with 85 or more bytes of data was 'Time out'
Pinging 51.158.148.26 with 85 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 51.158.148.26:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss)
If I run mtupath.exe 51.158.148.26, it shows
MTU path scan to 51.158.148.26, ttl=64, limit=48
# 26 best MSS 84 (estimated MTU 112) [pPPPP****p*p**ppP**P**P***]
#1 MSS IN RANGE 1 <== 83 ==> 84
#2 SCAN TIMEOUT 85 <== 1379 ==> 1464
#3 MSS EXCEEDED 1465 <== 14919 ==> 16384
[WARNING] Minimum IPv4 Internet MTU of 576 was not reached
[WARNING] Possible PMTU blackhole in route to peer
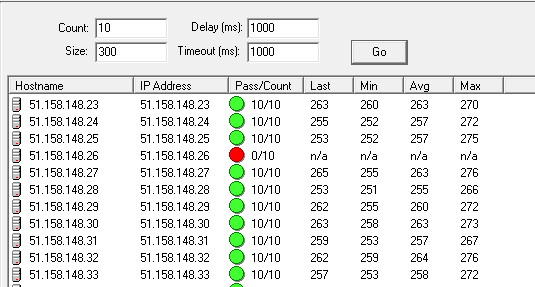
Why this server's MTU has limited to 112 bytes?
I installed latest NIC driver from Intel or Windows update, it did not help. I have disabled Windows Firewall, but nothing was chagned. I tried to run 'netsh wfp show netevents', but there is no related block events by wfp too. If changed server from Windows 2019 to Linux, everyting is okay.
If package did not drop on network layer, it is possible happen on physical layer or data link layer? How to check or debug if package drop on them? Refer: https://learn.microsoft.com/en-us/windows-hardware/drivers/network/windows-network-architecture-and-the-osi-model