Hello is there currently any option to disable the choice of WiFi APs? Is there a way to use this to lock down the system so it only works with one access point, or a list of system admin approved access points?
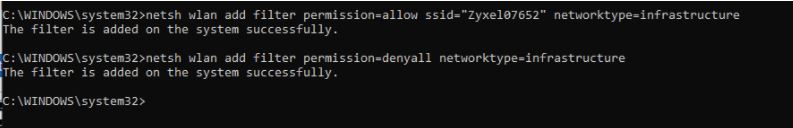
Is there a easier way with a GUI?
Above is the DOS way it works just like mac address lock downs for routers however in reverse pointing toward the wireless router. However this is only SSID based.
Devices are getting to be so small they are now able to download from electronic systems the size of a Tamagotchi that has a built-in AP. They even made a Tamagotchi plus a Gameboy, and it downloads data by changing your PC's access point to point toward the small device's AP. The small device comes with a built in access point. This is used to quickly change files, upload and download data. The current market for this is called a PocketSprite "Wirelessly and easily. You connect your phone or computer to the PocketSprite via [Wi-Fi], and then manage and upload new games, emulators and even saved-games with a single click" (Bruce). This points to a new need for mac address lockdowns that are pointed toward the routers from the Windows 10 devices you use in your homes and offices. If ever the need for changing them, you just add in the new device id. Lists based Wi-Fi much like hardware ID USB drive locking that is used todays secure environments. I personally want a PocketSprite just for gaming it is amazing, and I also see the need to lock down the selection of access points for high security networks. They have also made Wi-Fi equipped SD cards that can do the same thing. All someone needs to do now, is change the AP for 2 seconds and download a invasive file, or download a company classified document and walk out of the office with the access point and file in their pocket.
With Access points small enough to fit inside your pocket, USB jump drive issues that created the need for hardware ID lockdowns have now moved to WIFI access points issues. Same problems just now over Wi-Fi.
We need stricter SSID choices, that include hardware ids.

Nothing locks the laptop side down to a SSID based mac address from the laptop side. We need to point wireless choices to a strict SSID approved list. We need to point your device to only have approved choices for access points.
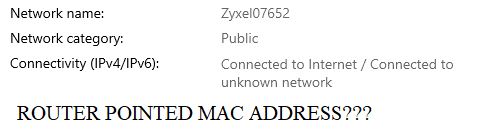

Laptop, smartphones, or other devices should not connect to anything that is not on approved access point list it should be GUI based control.

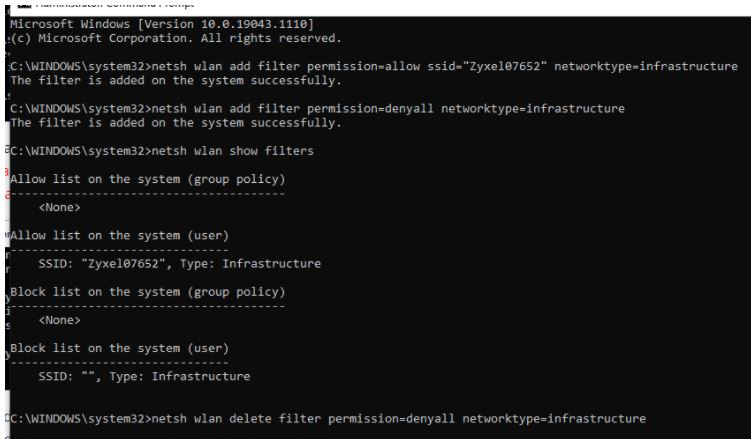
Is there a user friendly GUI option that shows the real routers mac addresses your using not just a SSID filters?
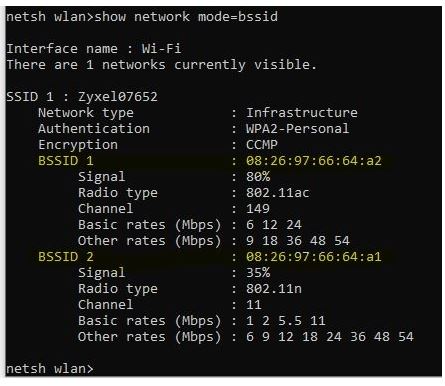
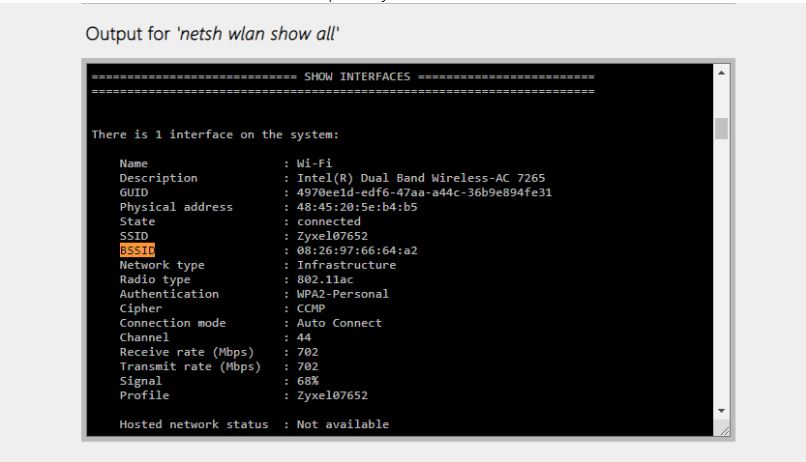
Keep in mind Windows 10 netsh wlan commands have full options for BSSID however fully using this functionality is very illusive, in the world of cyber security this needs to be center stage, not hidden in the background. BSSID is not even listed inside of administration of windows 10 class text books. If I try to add a BSSID filter this is the result.
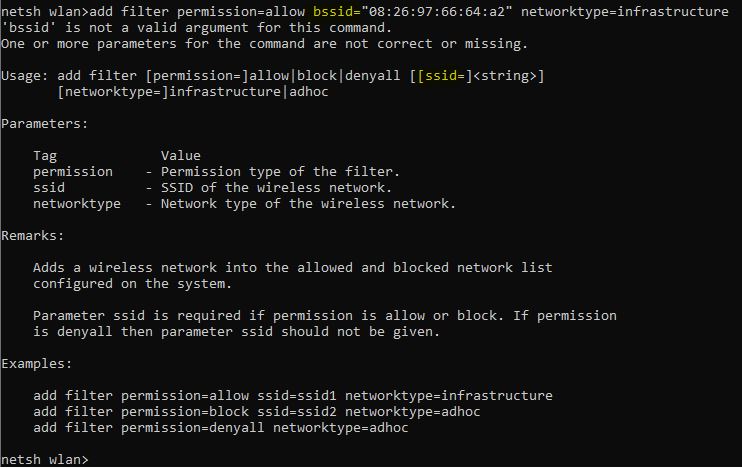
Why is netsh not listing the options for BSSID when we can use the mode list options? The doubling of SSID issues need to be addressed soon. Lets lock this down.
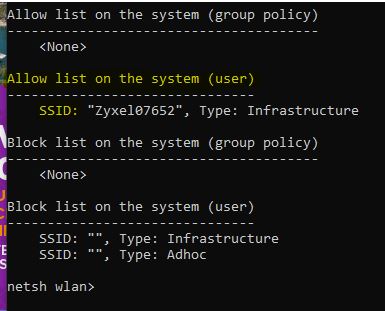
This should be listed as BSSID because the Windows 10 system already has the ability to track them, why not utilize them and fix the magnitudes of Wi-Fi cloned SSID cybersecurity issues?
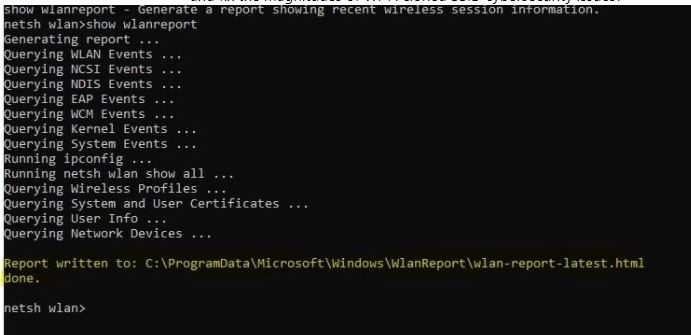
When you generate a report also it will only list current BSSID information historical information list only SSID info that can be changed to anything or mimic one.
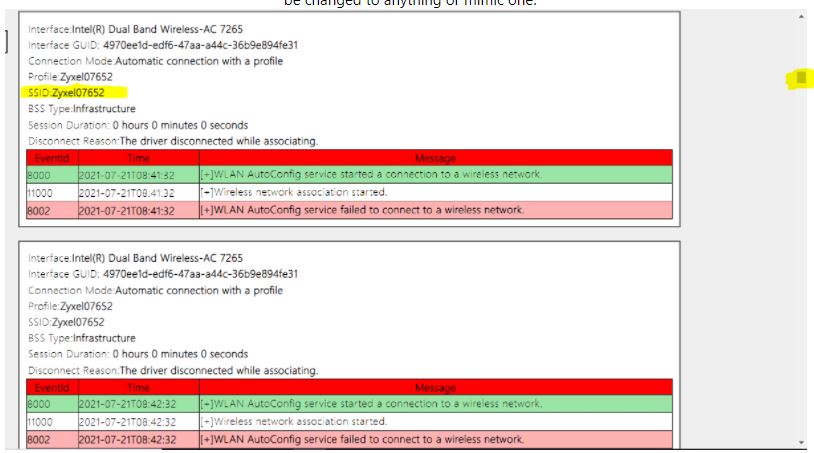
Notice on this massive Microsoft wireless report only historical connected SSIDs that have the BSSID removed.
The only BSSID information listed is in the report is what is currently connected. This has been removed from the SSID historical information
Side Note: This was tested with Zyzel and a Airport Extreme both configured with the same SSID and the same password. I disconnected one and powered up the other wireless router. All items Xbox One Xbox 360, Raspberry PI iMac, MacBook, iPhone 5s, Android version 10, iPhone SE connected to the new router without disruption or changes to logging into the SSID. The only device that required deleting the known network and adding was the Windows 10 Pro 21H119043.1202. This device required a reauthentication however the records are still showing no BSSIDs.
Works Cited:
Bruce, J., & James Bruce (704 Articles Published) . (2014, March 14). Wireless SD Cards Explained: The Features You'll Need. MUO. https://www.makeuseof.com/tag/wireless-sd-cards-explained-the-features-youll-need/.
Patwegar, W. (2018, June 8). How to Hide or Block WiFi Networks in Windows 10. Techbout. https://www.techbout.com/hide-block-wifi-networks-in-windows-10-38797/.
Tiny Retro Gaming on your Keychain. PocketSprite. (2021, July 12). https://pocketsprite.com/.













