This error usually occurs in multi-layer applications when the knownClientApplications parameter is not set in app manifest. I would recommend referring to Amanpreet's example and solution in this thread:
We have Tenant1 where APP1 (Web API) and App2 (Web or Native) multi-tenant applications are registered. We will be accessing App2 by a user account in Tenant2.
In Tenant1, register a web application named App1, which will be used as Web API. Once the application is registered, navigate to Exposing an API and set App ID URI. E.g. set the app ID URI to https://your_verified_domain/api/
Add required scopes such as read, user_impersonation etc. These scopes should be listed as https://your_verified_domain/api/read and https://your_verified_domain/api/user_impersonation on the Expose An API blade
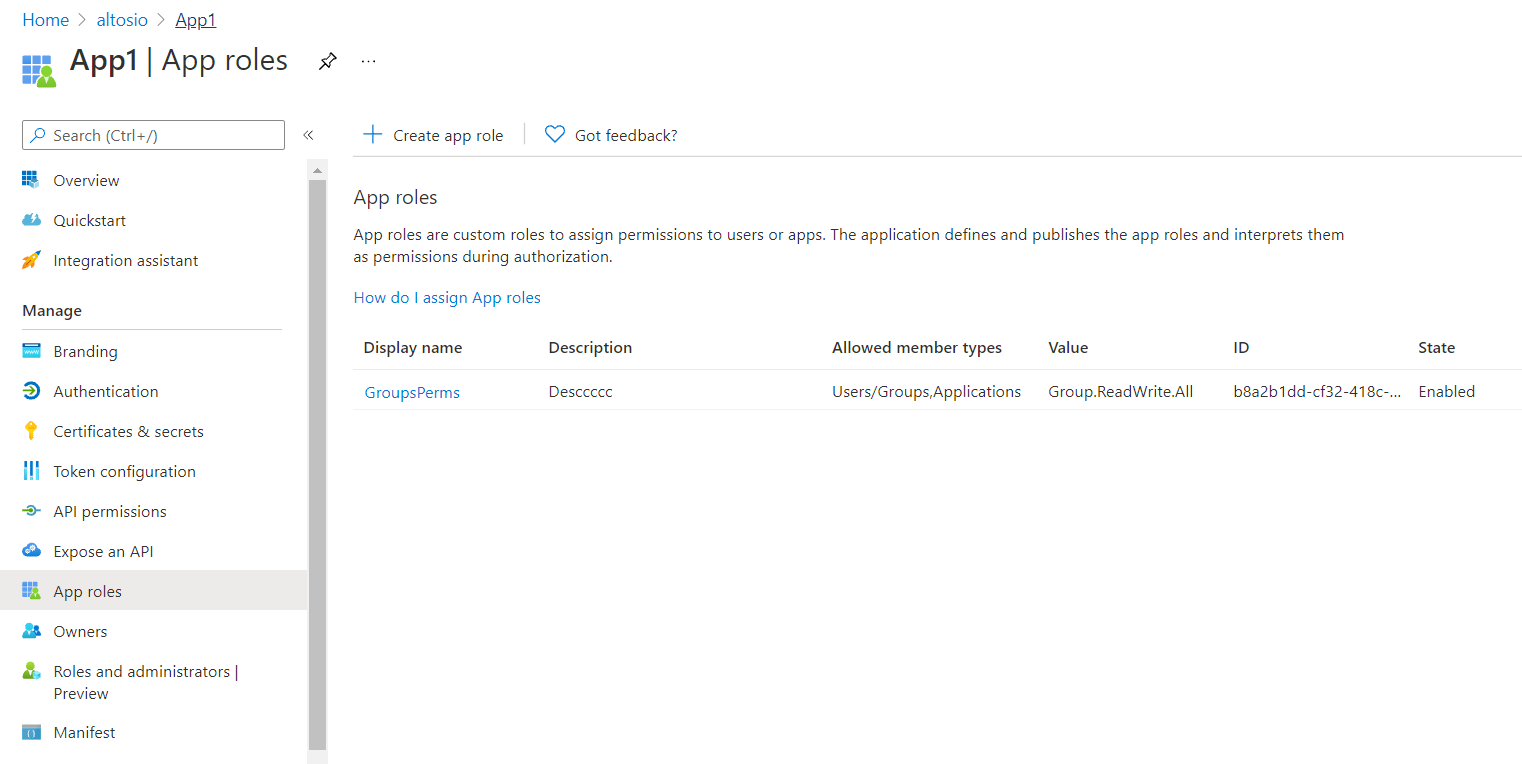
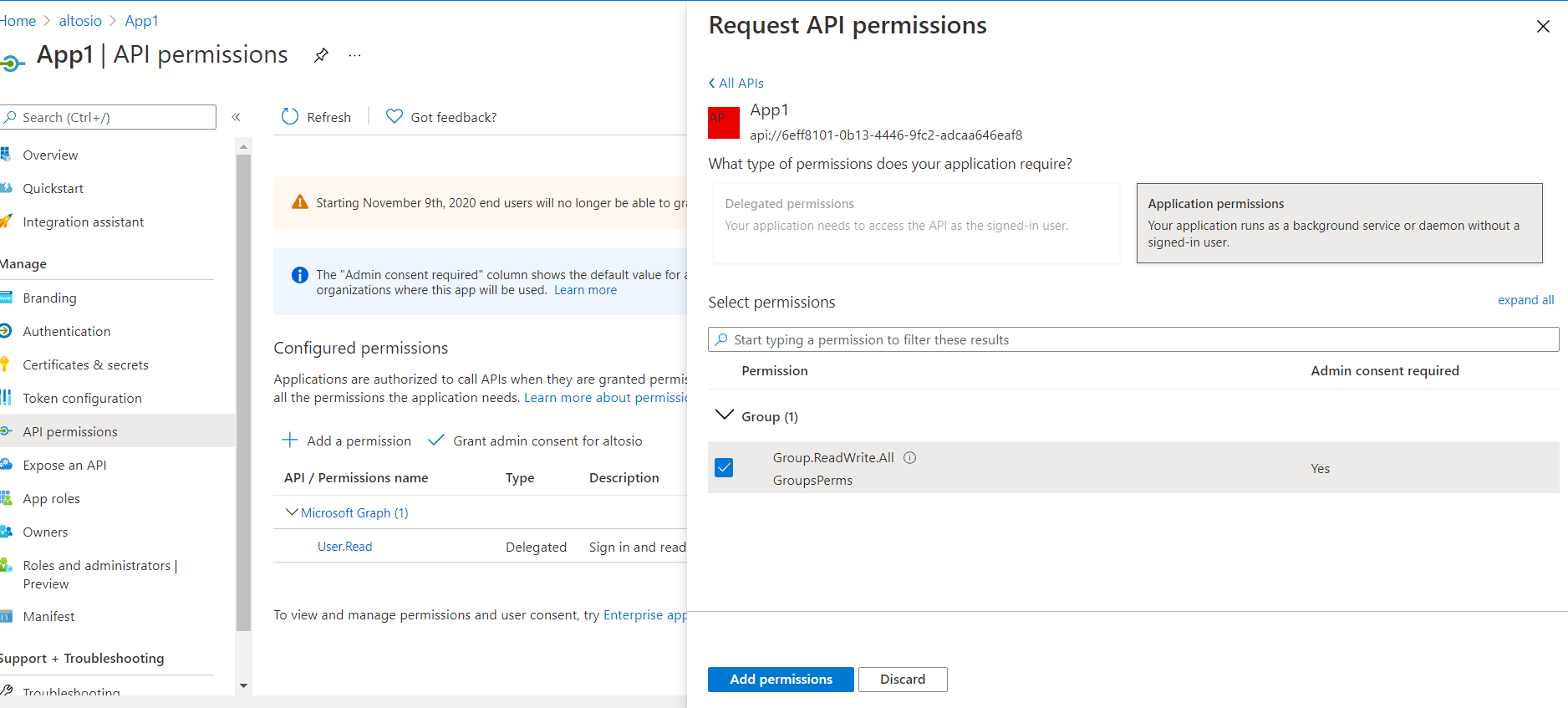
Register another application in Tenant1 and name it App2. Navigate to API Permissions and add the API permissions which are exposed as scopes in the above steps.
Add Client ID of App1 to knownClientApplications parameter in the Manifest of App2.
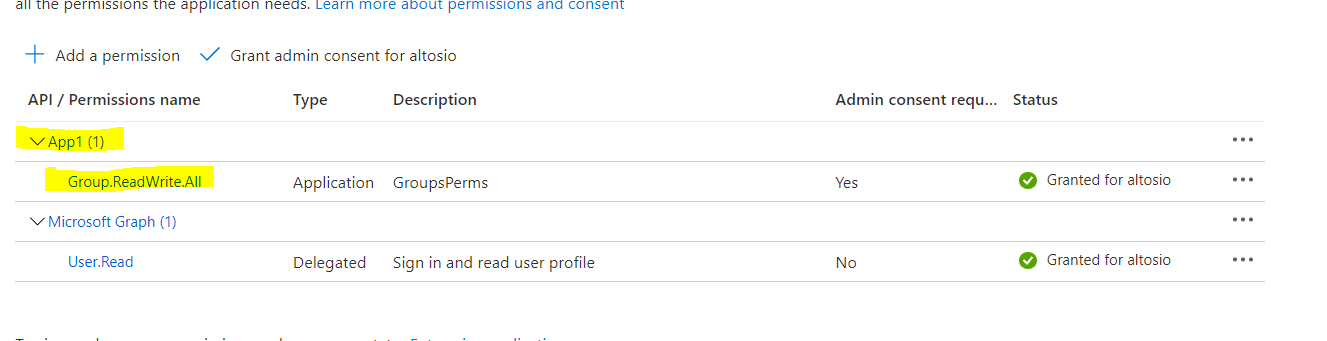
Since it is a multi-tenant app, we need to accept the consent prompt to access this application in Tenant2. For that purpose, use below URL after updating the client_id parameter with App ID of App2. https://login.microsoftonline.com/common/oauth2/authorize?client_id=1a8e25b8-xxxx-xxxx-xxxx-xxxxxxxxxxxx&prompt=admin_consent&response_type=code
The consent prompt will be presented with the permissions added in step3. After accepting the consent, the service principal for both applications, App1 and App2 will be created in Tenant2.
In this case, you shouldn't get the above error and the login should be successful.
Reference: invalid_client error
See also:
The app needs access to a service
Let me know if you still see this error after trying the steps suggested in Aman's answer.