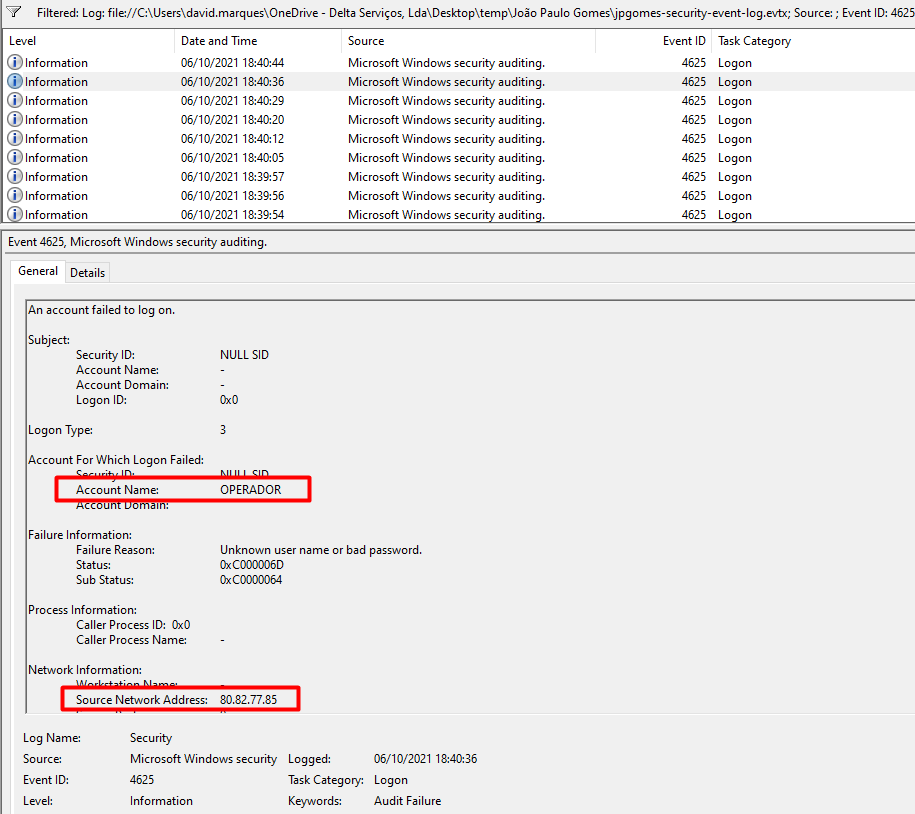
Attackers are using multiple ways , sometimes they just run a scan and perform a brute force and sometimes it is intentional attack meaning they are looking for a way to attack your company. I advise you to reset the password for the client and enforce using strong password. Use the Microsoft 365 Defender and investigate logs for clients and see if there is any other incident. Perform a full scan on the device and check security configuration for the device, M365 Defender will detect and report any other abnormal incident. You may block the IP in the firewall or even block the IP range and investigate it more.
Take a look at:
https://learn.microsoft.com/en-us/defender-for-identity/compromised-credentials-alerts