Hi @Shadab Basha
There is no native AD method get the previous values of an attribute after it has been changed, you need to have an external solution to capture i.e. backup, AD recovery tool, or Auditing.
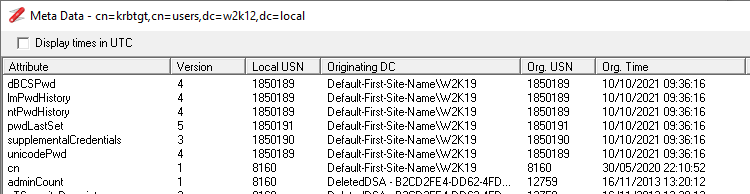
1 - repladmin /showobjmeta command will show you the time the change happened, the Ver column represents how many times the attribute has been changed. So if the Ver is 2 the password has been changed twice since the object was created.
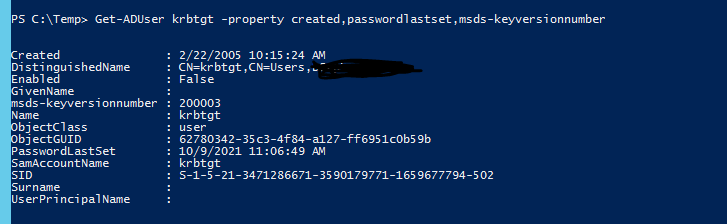
2 - The msDS-KeyVersionNumber is a constructed attribute so it is managed by the system, and as shown above, it is incremented each time the password associated to the account is changed. The attribute is the known as KVNO and is used by ktpass to create keypass table that allows non-Windows services that support Kerberos authentication using the AD KDC. I'm not sure if the ktpass command allow you to specify a new KVNO, if not, then the 200003 would suggest that's the number of times password of the krbtgt has been changed, the Ver number from the showobjmeta show reflect that. If not, then something has changed it to 200003.
I've looked at a couple of my test domains (2008 upgraded to 2019, 2012 build, 2019 build, 2022 build), and none of them have a KVNO this high and it reflects the number of times the password has been changed. Admittedly none of them have been upgraded from 2003 to 2012R2 or used to support Kerberos for non-Windows systems.
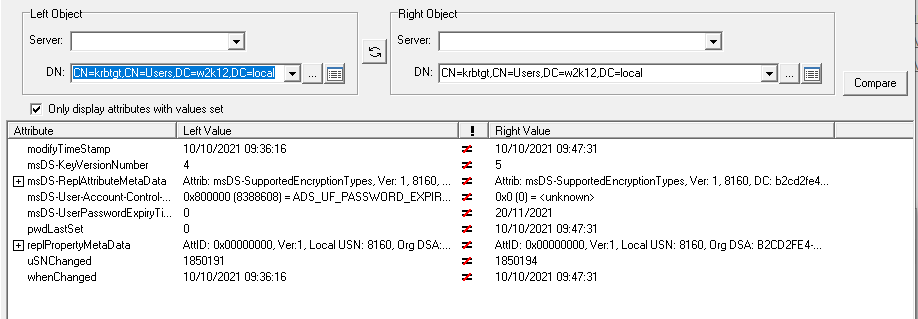
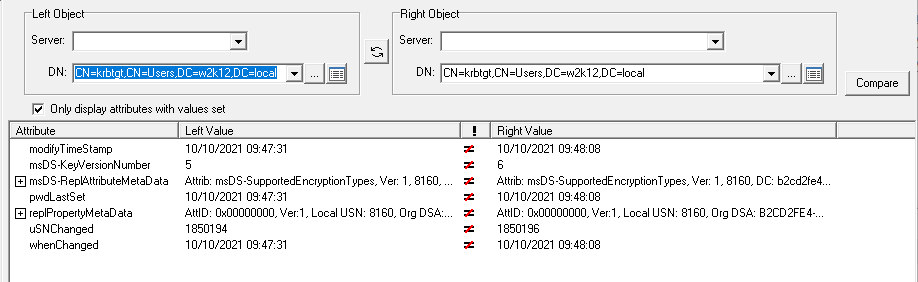
The tools in the screenshots is NetTools, the feature used was Object Compare, it lets you compare the differences between two objects or changed that have been made to a single object. The bottom picture is NetTools Meta Data dialog, which is of the same information you get from repladmin /showobjmeta.
Gary.