@Michael Hathaway
Thank you for your post!
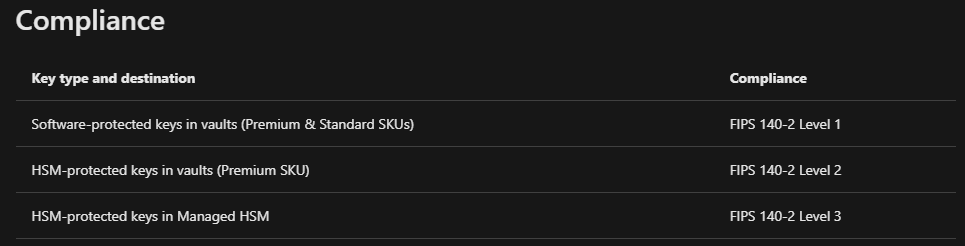
I don't believe there are any Az.KeyVault PowerShell commands that display the FIPS 140-2 Level 2 output. However, I did find some documentation that mentions Azure Key Vault uses nCipher HSMs, which are Federal Information Processing Standards (FIPS) 140-2 Level 2 validated...
For more info:
Securely store secrets and keys
Key Vault roles
I've also reached out to our Azure Key Vault SMEs to see if there are any other way we can see this information and will update as soon as possible.
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.