Hi @NechyporenkoOleksandr-9360
Welcome to Microsoft Q&A! Thanks for posting the question.
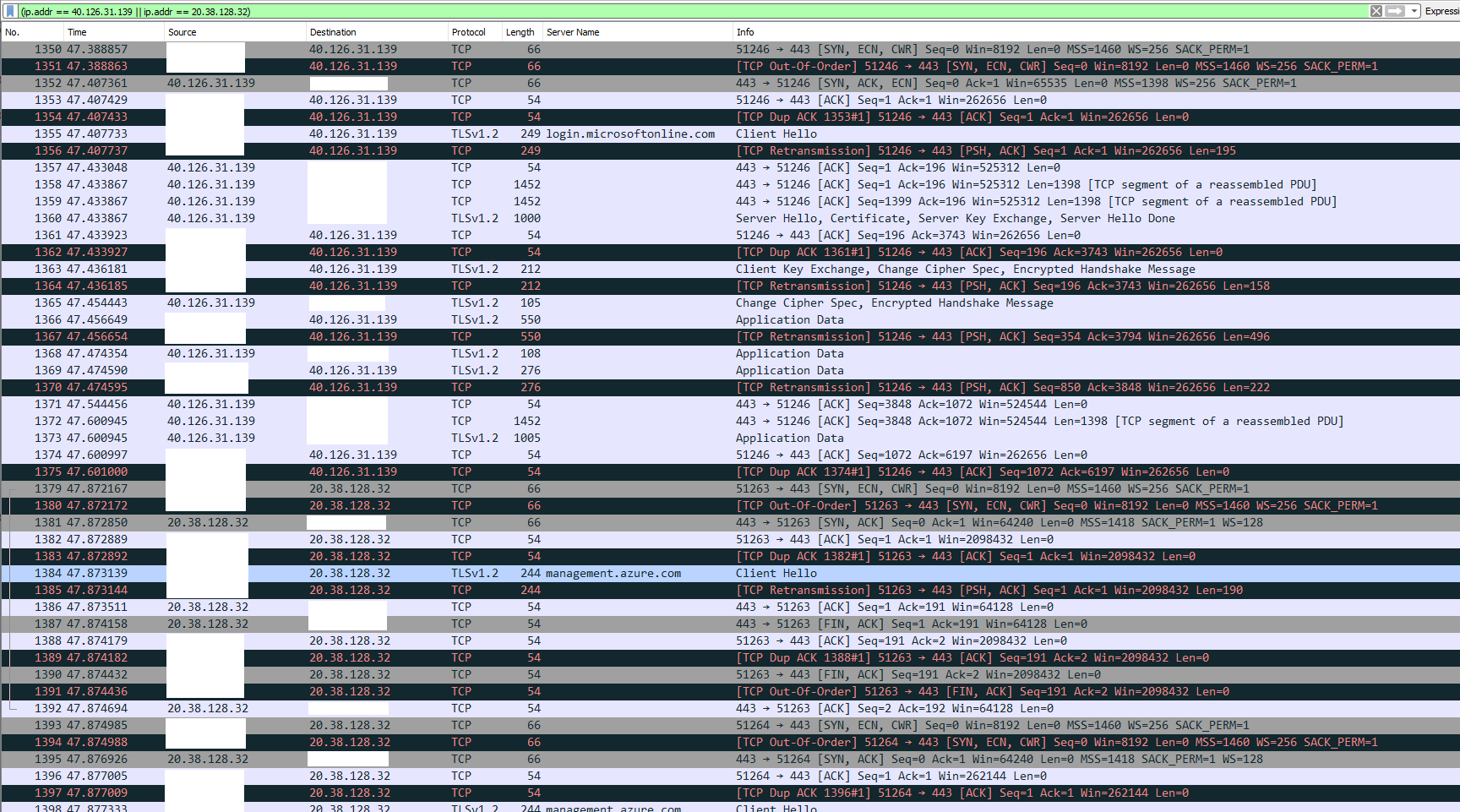
Apologies for the delayed response. The TLS handshake is completed after server responds with “Server hello” along with the negotiated specifications - most importantly Cypher algorithm to use. This link has a good explanation of the complete TLS handshake process. Most common causes for unsuccessful handshake process are:
- Server endpoint does not support the TLS version (which should not be the case here as the version is 1.2)
- Security software (antivirus/malware etc.) blocking OR intercepting the communication.
- None of the Cypher algorithms or other specifications presented by client in
Client Hellopacket is supported by the Server.
In Wireshark, to be able to get an overview of complete packet exchange for a particular conversation, please right click on the line with “Client Hello” message --> Conversation filter --> IP4. From here, the following troubleshooting guide would help you gain more insight of the handshake process and troubleshoot the failure.
- TLS connection common causes and troubleshooting guide – Part 1
- TLS connection common causes and troubleshooting guide – Part 2
- Troubleshooting TLS / SSL communication problems
In case, the steps and troubleshooting guide above does not help with the issue, you can enable Schannel event logging on your machine to get more details on the error. Please let me know if you have any questions.
Please 'Accept as answer' and ‘Upvote’ if it helped so that it can help others in the community looking for help on similar topics.