@SenhorDolas
I'm doing well, how're you doing?! It's great to work with you again, we previously worked together on your Azure AD Password Protection installation question!
After doing some more research and reading the blog post, the meaning behind this statement - It is not necessary that all the DCs are able to communicate with the Azure AD Password Protection Proxy Server..., is that at least one DC per domain needs to be able to communicate with the Azure AD Password Protection Proxy Service to take the new Password policy, but you'll need to install the DC Agent on all DC's in the domain if you want to secure the domain. For more info.
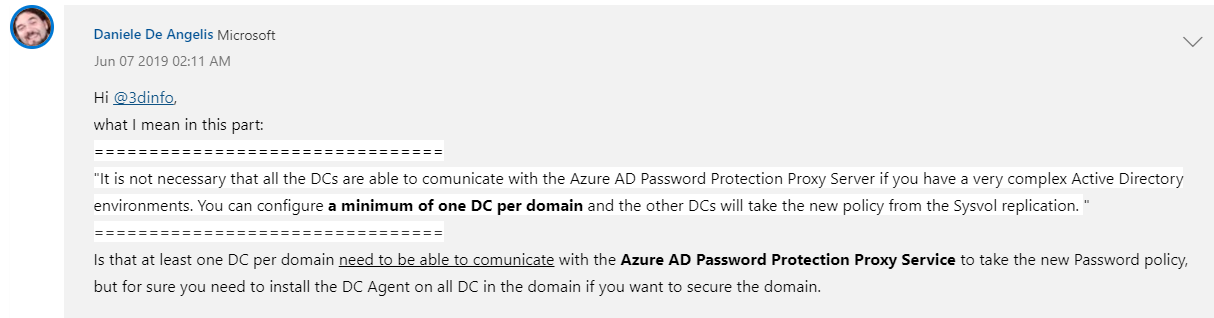
Referencing the How Does It Work flow, for when a user requests a password change to a DC:
- The DC Agent Password Filter dll from the OS - receives the password validation requests, and forwards them to the Azure AD Password Protection DC Agent, installed on the DC. This Agent then validates if the password is compliant with the locally stored Azure password policy.
With this flow and the author's comment in mind, the Azure AD Password Protection DC Agent is used to take the new Password policy from the Sysvol replication of the Azure AD Password Protection Proxy Server, to ensure the password change request is compliant with the policy.
However, the Get-AzureADPasswordProtectionSummaryReport cmdlet, produces its output by querying the DC agent admin event log, and this Admin event log, should only belong to that specific DC's events, which is why you're only getting the entry from the agent DC to come up.
I hope this makes sense! I spoke to @Marilee Turscak-MSFT offline and we both think this is the issue. But since the blog post author is internal to Microsoft, we've also reached out to see if this can be confirmed and will escalate it to our PG team, if needed.
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.